Mustang Panda Enhances Cyber Espionage Tactics with Updated COOLCLIENT Backdoor
In 2025, the Chinese state-sponsored cyber espionage group known as Mustang Panda, also referred to as Earth Preta, Fireant, HoneyMyte, Polaris, and Twill Typhoon, intensified its cyber operations by deploying an updated version of the COOLCLIENT backdoor. This sophisticated malware was primarily used to infiltrate government entities across Myanmar, Mongolia, Malaysia, and Russia, facilitating extensive data exfiltration from compromised systems.
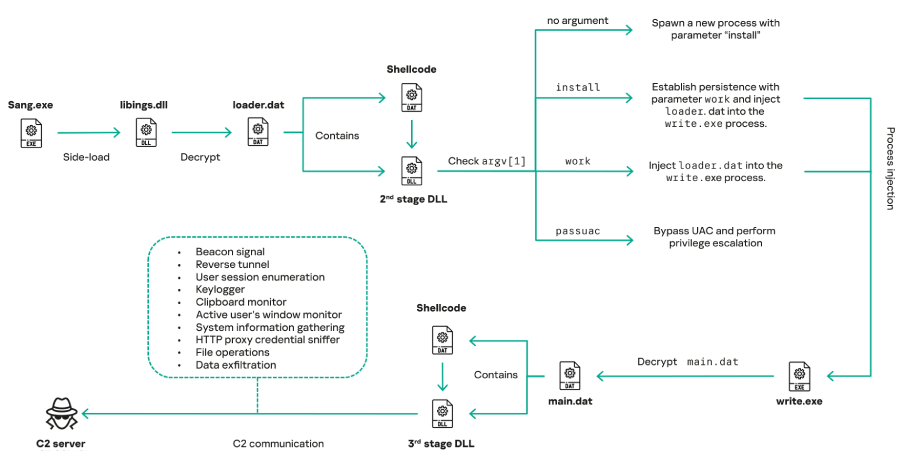
Kaspersky’s cybersecurity experts revealed that COOLCLIENT was often deployed alongside other malicious tools such as PlugX and LuminousMoth. The malware’s delivery mechanism involved encrypted loader files containing configuration data, shellcode, and in-memory DLL modules. These components utilized DLL side-loading techniques, wherein legitimate signed executables were exploited to load malicious DLLs, thereby evading detection.
Between 2021 and 2025, Mustang Panda leveraged signed binaries from various software products, including Bitdefender’s qutppy.exe, VLC Media Player’s vlc.exe (renamed as googleupdate.exe), Ulead PhotoImpact’s olreg.exe, and Sangfor’s sang.exe. Notably, campaigns in 2024 and 2025 abused Sangfor’s software to deliver a COOLCLIENT variant that deployed a previously unseen rootkit, enhancing the malware’s stealth and persistence.
Initially documented by Sophos in November 2022, COOLCLIENT was identified as part of a broader trend of DLL side-loading by Chinese APT groups. Trend Micro later attributed the backdoor to Mustang Panda, highlighting its capabilities to read and delete files, monitor clipboard activities, and track active windows. The malware was also implicated in attacks targeting multiple telecom operators in a single Asian country, suggesting a long-term espionage campaign that may have begun in 2021.
COOLCLIENT is engineered to collect comprehensive system and user information, including keystrokes, clipboard contents, files, and HTTP proxy credentials. It communicates with command-and-control (C2) servers over TCP, enabling the establishment of reverse tunnels or proxies and the execution of additional plugins in memory. Key plugins include:
– ServiceMgrS.dll: Manages all services on the infected host.
– FileMgrS.dll: Handles file operations such as enumeration, creation, movement, reading, compression, searching, and deletion.
– RemoteShellS.dll: Initiates a cmd.exe process, allowing operators to execute commands and capture outputs.
In addition to COOLCLIENT, Mustang Panda deployed three distinct stealer programs aimed at extracting saved login credentials from browsers like Google Chrome, Microsoft Edge, and other Chromium-based browsers. In certain instances, the group utilized cURL commands to exfiltrate Mozilla Firefox’s cookie file (cookies.sqlite) to Google Drive, indicating a sophisticated approach to data theft.
These stealers were detected in attacks against government sectors in Myanmar, Malaysia, and Thailand, suggesting their role in broader post-exploitation efforts. The campaigns also featured the use of TONESHELL (also known as TOnePipeShell), a malware employed to establish persistence and deploy additional payloads like QReverse. QReverse is a remote access trojan capable of executing remote shells, managing files, capturing screenshots, and gathering information.
Mustang Panda’s continuous evolution of its malware arsenal underscores the persistent threat posed by state-sponsored cyber espionage groups. Their ability to adapt and enhance their tools necessitates vigilant cybersecurity measures and proactive defense strategies to mitigate potential risks.