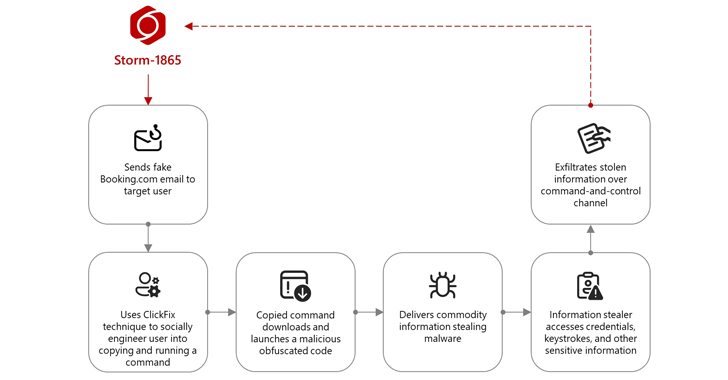
Microsoft has identified a new phishing campaign, known as ClickFix, which is actively impersonating Booking.com to target businesses in the hospitality sector. This campaign is designed to steal credentials, deploy remote access trojans (RATs), and facilitate financial fraud by tricking users into executing malicious commands on their systems.
How the ClickFix Attack Works
Attackers use social engineering techniques to manipulate victims into unknowingly running malicious scripts. The campaign follows a structured attack chain:
- Fake Booking.com Emails – Targeted users receive fraudulent emails that appear to be from Booking.com. These emails often claim to address urgent issues such as guest complaints, account verification, or reservation confirmations.
- Deceptive Attachments and Links – The emails include PDF attachments or links that direct recipients to a counterfeit Booking.com website designed to look legitimate.
- Fake CAPTCHA Challenge – The fraudulent website presents a CAPTCHA verification screen, instructing users to prove they are human. Instead of a real security check, the CAPTCHA copies a malicious command to the clipboard.
- Execution of Malicious Code – The fake CAPTCHA instructs users to open the Windows Run dialog, paste the copied command, and execute it. This action downloads and installs malware onto the victim’s system.
Malware Deployed Through the Campaign
The ClickFix phishing attack delivers multiple types of malware, each serving different purposes. The most common payloads include:
- XWorm – A remote access trojan allowing attackers to control infected machines.
- Lumma Stealer – A credential-stealing malware designed to extract login information and financial data.
- VenomRAT – A remote access tool capable of keylogging and data exfiltration.
- AsyncRAT – Used for surveillance, remote control, and system compromise.
- Danabot – A banking trojan that targets online financial transactions.
- NetSupport RAT – Originally a legitimate remote administration tool, but abused by attackers for unauthorized access.
Once installed, these malware programs allow attackers to steal sensitive business information, monitor employee activity, and facilitate unauthorized financial transactions.
Tactics Used by the Threat Group Behind ClickFix
The Storm-1865 hacking group is believed to be behind this phishing campaign. This group has been active since early 2023, focusing on businesses in the hospitality, e-commerce, and financial sectors. Previous attacks by this group targeted hotel guests with fraudulent emails designed to steal payment details.
The ClickFix campaign represents an evolution in their strategy, incorporating fake security verifications and social engineering tactics to bypass traditional security measures.
How Businesses Can Protect Themselves
Organizations, particularly those in the hospitality industry, can take several steps to defend against ClickFix and similar phishing threats:
- Verify Email Authenticity – Employees should carefully inspect email senders, links, and attachments before taking any action. Any urgent request for login credentials or financial information should be independently verified.
- Avoid Running Unknown Commands – Users should never copy and execute commands from an unknown website or email, even if they appear to come from a trusted source.
- Enable Multi-Factor Authentication (MFA) – Even if attackers obtain login credentials, MFA can prevent unauthorized access to sensitive systems.
- Train Employees on Phishing Risks – Regular security awareness training can help employees recognize and report phishing attempts before they become security incidents.
- Use Advanced Threat Detection – Email filtering systems, endpoint protection software, and behavior-based detection tools can help block phishing emails and detect malicious activity.
Why This Phishing Campaign is Dangerous
ClickFix is more sophisticated than traditional phishing attacks because it tricks users into actively compromising their own systems. By exploiting fake security verifications and urgent booking-related messages, attackers create a false sense of legitimacy, increasing the likelihood that victims will follow through with the malicious instructions.
As phishing campaigns become more deceptive, businesses must adopt stronger security policies, employee training programs, and technical safeguards to mitigate the risks posed by evolving cyber threats.