Microsoft Teams Vulnerabilities Expose Users to Message Manipulation and Identity Spoofing
Microsoft Teams, a pivotal communication platform for over 320 million users globally, has recently been found to harbor critical vulnerabilities that could allow attackers to impersonate executives and manipulate messages without detection. These security flaws, now addressed by Microsoft, previously enabled both external guests and internal users to spoof identities in chats, notifications, and calls, potentially leading to fraud, malware distribution, and misinformation.
The cybersecurity firm Check Point identified and responsibly disclosed these issues to Microsoft in March 2024. The findings underscore the potential for trust in collaboration tools to be exploited by sophisticated threat actors targeting remote work infrastructures.
Understanding the Vulnerabilities
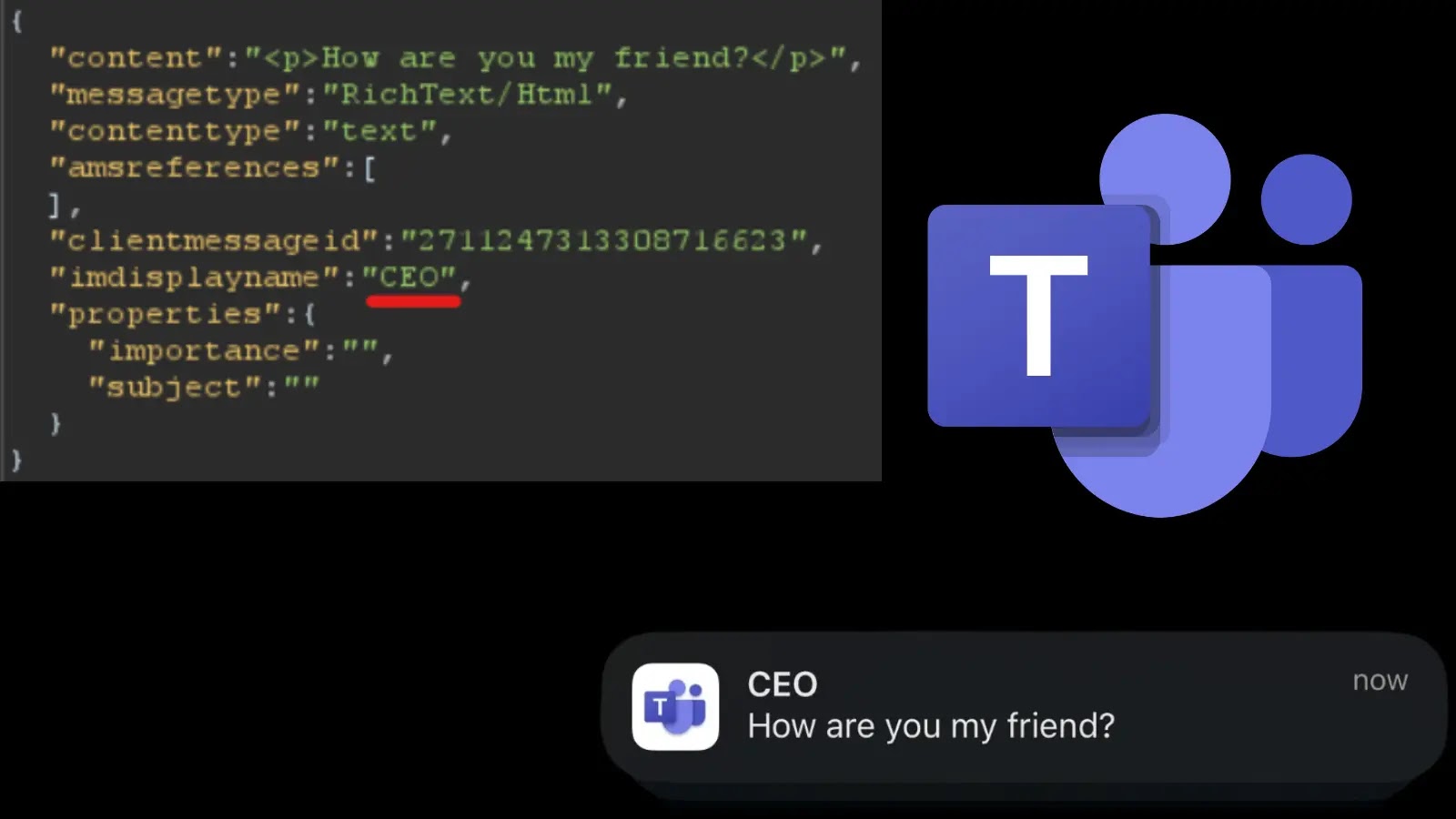
Launched in 2017 as part of the Microsoft 365 suite, Teams integrates chat, video calls, file sharing, and app collaboration, making it indispensable for businesses ranging from startups to Fortune 500 companies. Check Point’s investigation focused on the web version’s JSON-based architecture, where messages include parameters such as content, messagetype, clientmessageid, and imdisplayname.
Attackers exploited these parameters to edit messages without triggering the Edited label by reusing clientmessageids, effectively rewriting message history without leaving traces. Notifications could be manipulated by altering the imdisplayname parameter, making alerts appear as though they were from high-level executives like CEOs, thereby exploiting users’ instinctive trust in urgent communications.
In private chats, modifying conversation topics via a PUT endpoint allowed attackers to change display names, misleading participants about the sender’s identity. Similarly, initiating calls through the POST /api/v2/epconv endpoint enabled the forging of displayName in participant sections, spoofing caller identities during audio or video sessions.
One specific flaw, notification spoofing, was tracked as CVE-2024-38197, a medium-severity issue (CVSS 6.5) affecting iOS versions up to 6.19.2, where sender fields lacked proper validation.
Potential Attack Scenarios
These vulnerabilities undermine the core trust in Teams, transforming it into a vector for deception by advanced persistent threats (APTs), nation-state actors, and cybercriminals.
– External Threats: External guests could infiltrate organizations by impersonating finance leaders to harvest credentials or distribute malware-laden links disguised as executive directives.
– Insider Threats: Internal users might disrupt critical meetings by spoofing calls, spreading confusion during sensitive discussions, or facilitating business email compromise (BEC) schemes.
Real-world risks include financial fraud, where fake CEO notifications prompt unauthorized wire transfers; privacy breaches resulting from falsified conversations; and espionage through manipulated histories in supply chain attacks.
Threat actors, including groups like Lazarus, have historically targeted such platforms for social engineering, as evidenced in recent reports of Teams being abused for ransomware deployment and data exfiltration.
The ease with which these flaws can be chained together—such as spoofing a notification followed by a forged call—amplifies the danger, potentially deceiving users into revealing sensitive information or executing harmful actions.
Microsoft’s Response and Mitigation Measures
Check Point disclosed the vulnerabilities to Microsoft on March 23, 2024. Microsoft acknowledged the issues on March 25 and implemented fixes progressively:
– Message Editing Issue: Resolved by May 8, 2024.
– Private Chat Alterations: Addressed by July 31, 2024.
– Notification Spoofing (CVE-2024-38197): Fixed by September 13, 2024, following an August rollout.
– Call Spoofing: Remediated by October 2025.
All issues have now been addressed across all client platforms, requiring no user action beyond ensuring their applications are updated to the latest versions.
Recommendations for Organizations
While Microsoft has patched these vulnerabilities, organizations should adopt additional security measures to safeguard against potential exploitation:
1. Implement Zero-Trust Verification: Enforce strict verification protocols for identities and devices accessing the network.
2. Deploy Advanced Threat Prevention: Utilize security solutions capable of scanning and analyzing payloads within Teams to detect and block malicious content.
3. Enforce Data Loss Prevention (DLP) Policies: Establish policies to monitor and control the transfer of sensitive information within the organization.
4. Conduct Staff Training: Educate employees on recognizing and validating suspicious communications, even those appearing to originate from trusted sources.
Maintaining a culture of critical thinking and vigilance is essential. Users should always verify the authenticity of communications, especially those requesting sensitive information or urgent actions. As collaboration tools continue to evolve, securing human trust is as vital as patching software vulnerabilities.