Microsoft Threat Intelligence has unveiled a significant evolution in ransomware methodologies, spearheaded by the financially motivated threat actor known as Storm-0501. This group has transitioned from traditional on-premises ransomware attacks to a more destructive, cloud-centric approach that involves both data exfiltration and destruction. This shift fundamentally alters the ransomware threat landscape for organizations operating in hybrid cloud environments.
Traditional vs. Cloud-Native Ransomware Attacks
Historically, ransomware attacks have focused on encrypting files on local servers, followed by ransom demands for decryption keys. Storm-0501’s new strategy, however, is markedly more devastating. The group leverages cloud-native capabilities to first exfiltrate large volumes of sensitive data. Subsequently, they systematically destroy the original data and any backups within the victim’s cloud environment before issuing a ransom demand. This steal-and-destroy tactic eliminates the possibility of recovery from local backups, placing immense pressure on victim organizations to comply with ransom demands.
Detailed Attack Chain
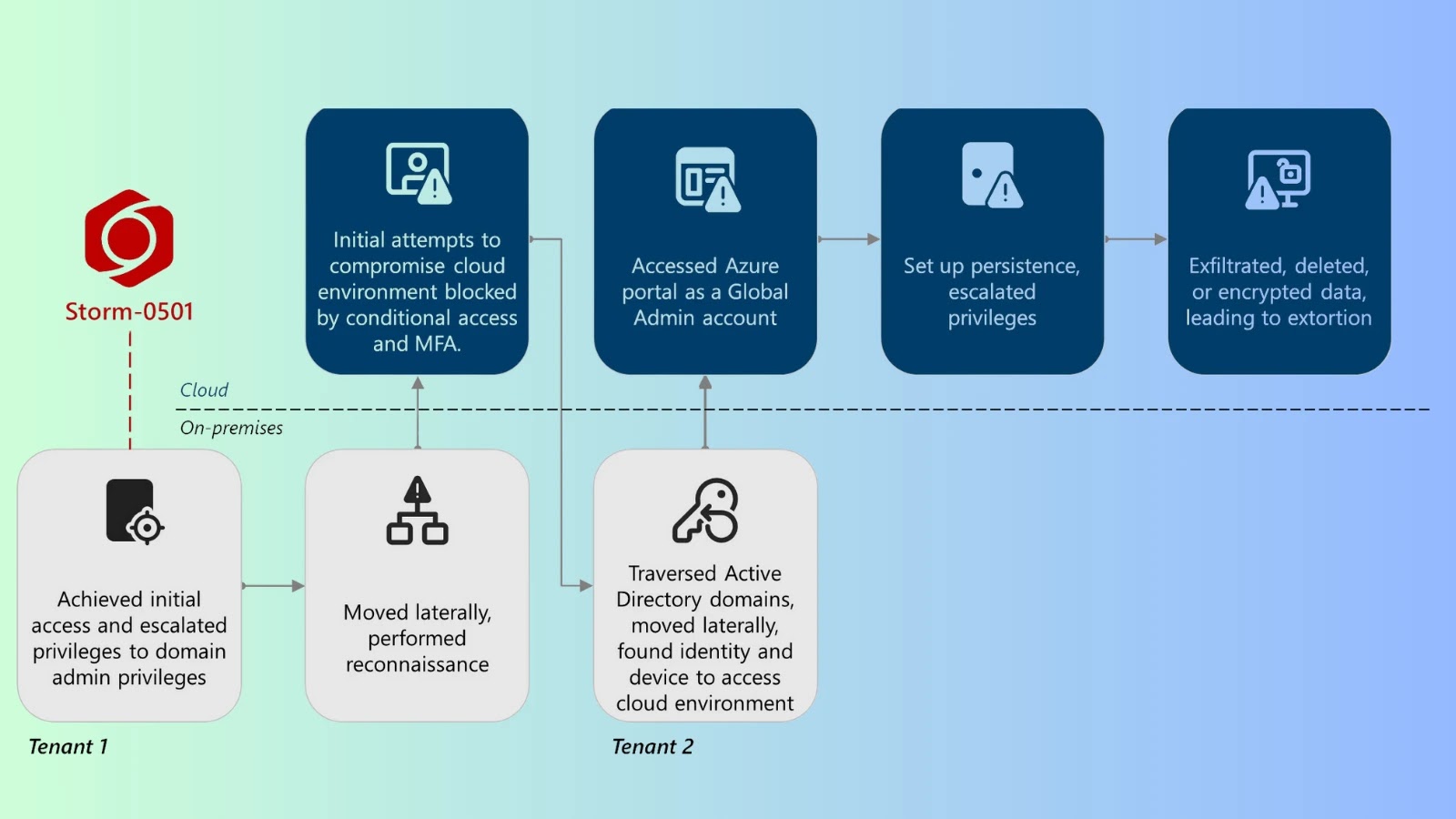
Microsoft’s analysis reveals a sophisticated attack chain that blends on-premises and cloud infiltration techniques:
1. Initial Compromise: The attack often begins with the compromise of a company’s local Active Directory.
2. Cloud Pivot: From this foothold, attackers pivot to the cloud, targeting Microsoft Entra ID (formerly Azure Active Directory).
3. Privilege Escalation: The primary objective is to identify high-privilege accounts, such as Global Administrators, that lack robust security measures, particularly multi-factor authentication (MFA).
4. Account Takeover: In a recent campaign, Storm-0501 identified a synchronized, non-human Global Administrator account without a registered MFA method. They reset the account’s password on-premises, which then synchronized to the cloud. By taking over this account, they enrolled their own MFA device, bypassing existing security policies and gaining complete control over the cloud domain.
5. Privilege Elevation: With top-level administrative access, the attackers elevated their privileges within Azure to become Owners of all the organization’s cloud subscriptions.
6. Discovery Phase: They initiated a discovery phase to map out critical assets, including data stores and backups.
7. Data Exfiltration: Using cloud tools like AzCopy, they exfiltrated the data.
8. Destruction Phase: The final impact phase is swift and catastrophic. Storm-0501 initiated a mass deletion of Azure resources, including storage accounts, virtual machine snapshots, and recovery vaults. For data protected by resource locks or immutability policies, the attackers first attempted to disable these protections. If unsuccessful, they resorted to encrypting the remaining data with a key they controlled and then deleting the key, rendering the information permanently inaccessible. The extortion demand was then typically delivered via Microsoft Teams using a compromised account.
Mitigation Strategies
To combat these advanced threats, Microsoft recommends organizations adopt a multi-layered defense strategy:
– Enforce Phishing-Resistant MFA: Implement multi-factor authentication for all users to prevent unauthorized access.
– Principle of Least Privilege: Ensure that users have only the access necessary for their roles, minimizing potential attack surfaces.
– Secure Privileged Accounts: Ensure that privileged accounts are cloud-native and secured with robust authentication methods.
– Utilize Built-In Cloud Security Features: Leverage tools like Microsoft Defender for Cloud to monitor and protect cloud environments.
– Apply Resource Locks: Implement resource locks on critical assets to prevent unauthorized modifications or deletions.
– Enable Immutability and Soft-Delete Policies: Configure storage and key vaults with immutability and soft-delete policies to prevent irreversible data loss.
Conclusion
Storm-0501, previously known for attacks on U.S. school districts and the healthcare sector, continues to demonstrate its proficiency in navigating complex hybrid environments. This underscores the urgent need for businesses to adapt their security postures to address the evolving threats in the cloud era.