Microsoft Uncovers Sophisticated Multi-Stage Phishing and BEC Attacks on Energy Sector
Microsoft has recently identified a complex, multi-stage adversary-in-the-middle (AitM) phishing and business email compromise (BEC) campaign specifically targeting organizations within the energy sector. This campaign exploits trusted platforms and sophisticated techniques to infiltrate and persist within corporate email systems.
Initial Compromise via Trusted Platforms
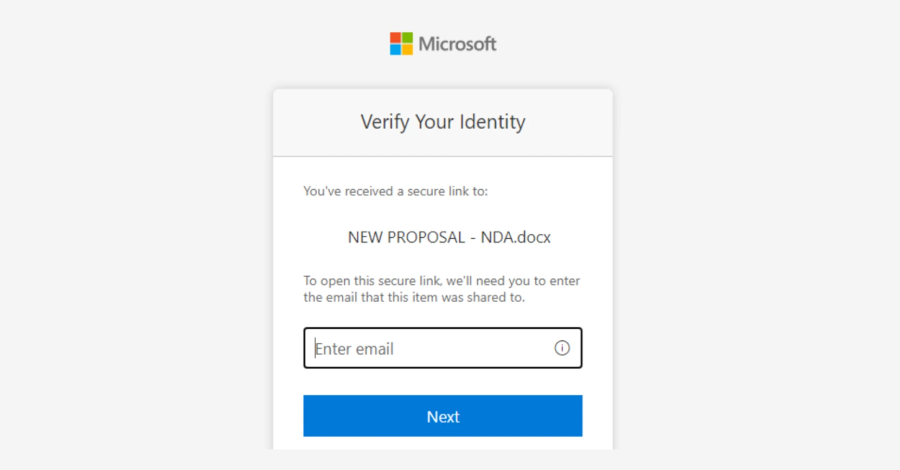
The attack begins with phishing emails sent from previously compromised accounts within trusted organizations. These emails mimic legitimate SharePoint document-sharing notifications, a tactic that leverages the widespread use and trust of SharePoint and OneDrive in enterprise environments. By originating from authentic addresses and referencing familiar platforms, these messages are less likely to raise suspicion among recipients.
Embedded within these emails are links that redirect users to counterfeit login pages designed to harvest credentials. Once the attackers obtain these credentials, they gain unauthorized access to the victim’s email account.
Establishing Persistence and Evading Detection
Upon accessing the compromised account, the attackers implement several measures to maintain control and avoid detection:
– Inbox Rule Manipulation: They create rules to delete incoming emails and mark them as read, effectively concealing their activities from the account owner.
– Session Hijacking: By capturing session cookies, the attackers can bypass multi-factor authentication (MFA) protocols, allowing them to sustain access even if the user changes their password.
Expansion Through Internal and External Phishing
With control over the compromised account, the attackers launch extensive phishing campaigns targeting the victim’s contacts both within and outside the organization. In one observed instance, over 600 phishing emails were dispatched from a single compromised account. These emails contain malicious links leading to AitM phishing sites that replicate legitimate login pages, further harvesting credentials and session cookies from new victims.
Operational Complexity and Mitigation Strategies
This campaign underscores the sophisticated nature of modern phishing and BEC attacks. Simple password resets are insufficient to remediate such breaches due to the attackers’ ability to hijack sessions and manipulate inbox rules. Comprehensive mitigation requires:
– Revoking Active Sessions: Ensuring that all active session cookies are invalidated to prevent unauthorized access.
– Removing Malicious Inbox Rules: Identifying and deleting any rules created by the attackers to conceal their presence.
– Implementing Phishing-Resistant MFA: Adopting multi-factor authentication methods that are less susceptible to phishing attacks.
– Continuous Access Evaluation: Monitoring and evaluating access patterns to detect and respond to anomalies promptly.
– Advanced Anti-Phishing Solutions: Deploying solutions that can scan and monitor incoming emails and visited websites for phishing indicators.
Organizations are advised to collaborate with their identity providers to enforce these security controls and remain vigilant against such sophisticated attack vectors.