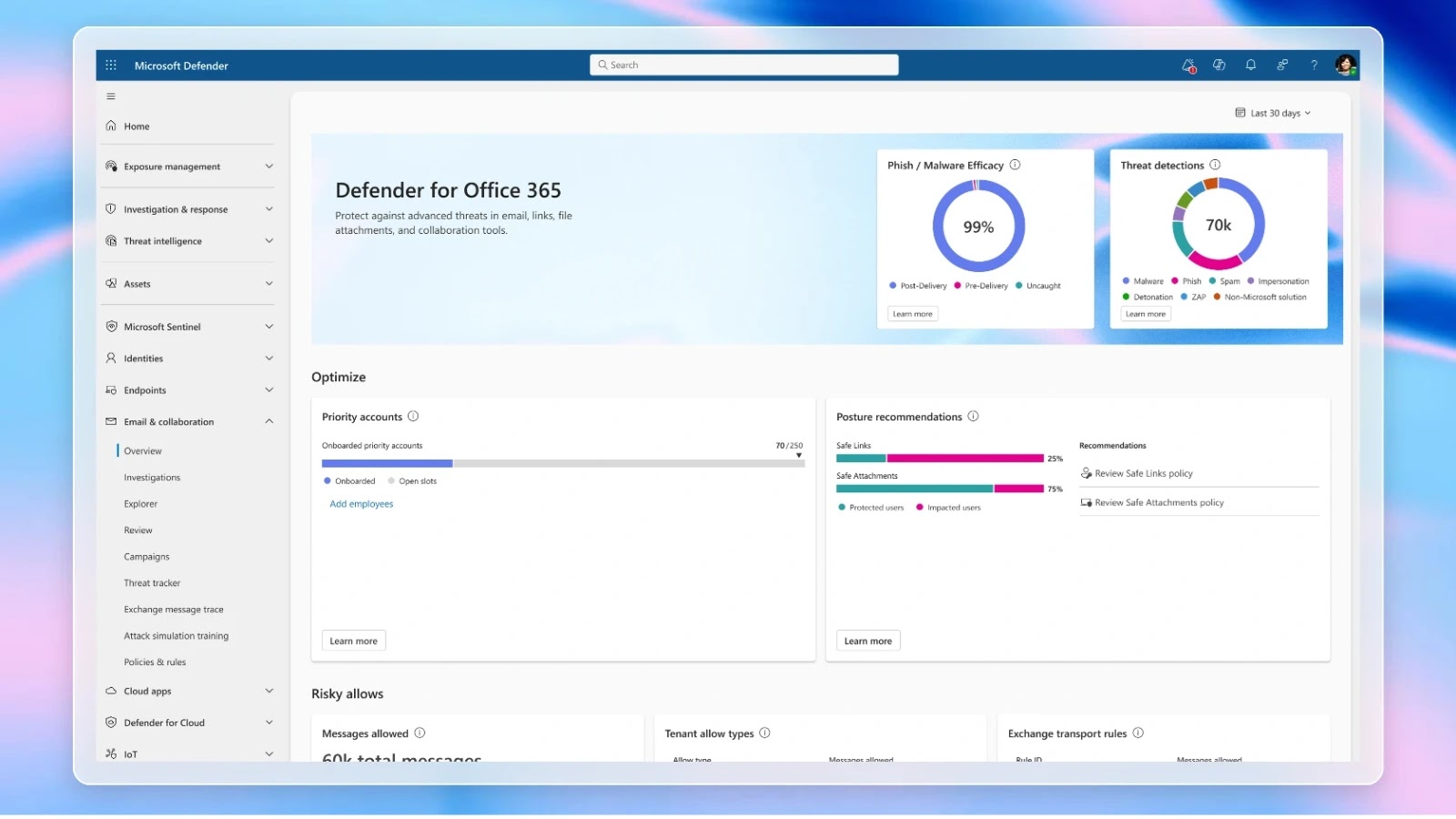
Microsoft has introduced a significant update to its Defender for Office 365 platform, featuring a redesigned customer dashboard aimed at providing security teams with real-time, in-depth visibility into a wide array of attack vectors. This enhancement is part of Microsoft’s ongoing commitment to transparency and data-driven security decision-making.
Advanced Threat Visibility
The centerpiece of this update is the Overview Dashboard, which consolidates multiple threat streams into a unified interface. Security operations teams can now monitor various metrics, including:
– Phishing URLs Neutralized by Safe Links: Tracks the number of malicious links intercepted before reaching end-users.
– Malicious Files Quarantined via Safe Attachments: Counts the instances of harmful files detected and isolated.
– Messages Auto-Purged at Zero-Hour: Records the number of emails removed before users can access them, minimizing potential threats.
Beyond these metrics, the dashboard provides insights into dwell times for post-delivery threats, highlighting delayed detections and enabling teams to refine their policies and workflows. By integrating data across platforms such as Exchange Online, Microsoft Teams, SharePoint, and OneDrive, defenders can correlate spikes in business email compromise (BEC) attempts or malware campaigns with broader collaboration trends.
A companion pane categorizes threats into Bulk, Spam, and Malicious, illustrating how each Defender capability contributes to overall protection. Security architects can delve into detailed analyses, identifying top sender domains used in recent phishing campaigns or the most commonly weaponized file types in malware outbreaks. This dynamic intelligence center transforms raw telemetry into actionable insights, enhancing operational efficiency.
Benchmarking Reports
Recognizing the layered nature of many organizations’ email defenses, Microsoft has also published benchmarking reports comparing Secure Email Gateways (SEGs) and Integrated Cloud Email Security (ICES) vendors against Defender for Office 365. These studies utilize real-world threat data aggregated across millions of mailboxes, offering a transparent basis for evaluating Microsoft’s native defenses alongside third-party solutions.
In one scenario, SEGs placed in front of Defender were assessed for pre-delivery misses versus Defender’s own pre- and post-delivery standards. In another, ICES products invoked via the Microsoft Graph API after Defender for Office 365 scanned messages were evaluated for their incremental catch rates.
To facilitate integration with Security Information and Event Management (SIEM) and Security Orchestration, Automation, and Response (SOAR) platforms, Microsoft provided a PowerShell example using the Microsoft Graph Security API. The JSON response includes fields such as safeLinks, safeAttachments, and zeroHourAutoPurge, enabling seamless programmatic extraction of dashboard metrics.
Additional Enhancements in Microsoft Defender for Office 365
In addition to the new dashboard, Microsoft has rolled out several other enhancements to Defender for Office 365:
– Mail Bombing Detection: Defender for Office 365 now includes capabilities to detect and classify mail bombing attacks, a form of distributed denial of service (DDoS) attack that overwhelms recipients’ mailboxes with a large volume of emails. This feature leverages multi-layered AI and machine learning models to analyze email traffic patterns, including bulk email filtering with dynamic threshold adjustments and campaign clustering algorithms. Detected attacks are automatically routed to Junk folders while respecting Safe Senders lists, ensuring critical communications remain unaffected. ([learn.microsoft.com](https://learn.microsoft.com/en-us/defender-office-365/defender-for-office-365-whats-new?utm_source=openai))
– AI-Powered Submissions Response: The platform introduces generative AI explanations for admin email submissions to Microsoft, enhancing transparency and understanding for security teams. ([learn.microsoft.com](https://learn.microsoft.com/en-us/defender-office-365/defender-for-office-365-whats-new?utm_source=openai))
– Auto-Remediation of Malicious Messages: Automated investigation and response capabilities now include auto-remediation, reducing the time to mitigate email threats. ([techcommunity.microsoft.com](https://techcommunity.microsoft.com/blog/microsoftthreatprotectionblog/monthly-news—july-2025/4428862?utm_source=openai))
– Integration with Third-Party Vendors: The new Defender for Office 365 ICES Vendor Ecosystem provides a unified framework for seamless integration with trusted third-party vendors, extending protection capabilities. ([techcommunity.microsoft.com](https://techcommunity.microsoft.com/blog/microsoftthreatprotectionblog/monthly-news—july-2025/4428862?utm_source=openai))
– Enhanced Threat Detection in Defender for Cloud Apps: Defender for Cloud Apps has received upgrades, including a new Behaviors Data Type that reduces noise from generic anomalies and surfaces alerts only when patterns match real security scenarios, improving detection accuracy. ([msftnewsnow.com](https://msftnewsnow.com/microsoft-defender-xdr-july-2025-security-updates/?utm_source=openai))
– Advanced Hunting Enhancements: The introduction of new data tables, CampaignInfo and FileMaliciousContentInfo, in Advanced Hunting under the Email & Collaboration schema, aids Security Operations Center (SOC) teams in investigating email campaigns and malicious files more effectively. ([mc.merill.net](https://mc.merill.net/message/MC1088729?utm_source=openai))
– Platform Migration for Enhanced Performance: Microsoft Defender for Office 365 is migrating its data platform to enhance performance and scalability, aiming for completion by late June 2025. Benefits include improved data consistency, parity between tools, enhanced performance, and faster feature development. ([mc.merill.net](https://mc.merill.net/message/MC1042926?utm_source=openai))
Conclusion
The introduction of the enhanced dashboard in Microsoft Defender for Office 365 marks a significant advancement in providing security teams with comprehensive, real-time insights into a wide range of threats. By consolidating threat data across multiple platforms and integrating advanced detection and remediation capabilities, Microsoft empowers organizations to make informed, data-driven security decisions. These enhancements reflect Microsoft’s commitment to transparency, efficiency, and continuous improvement in the ever-evolving landscape of cybersecurity.