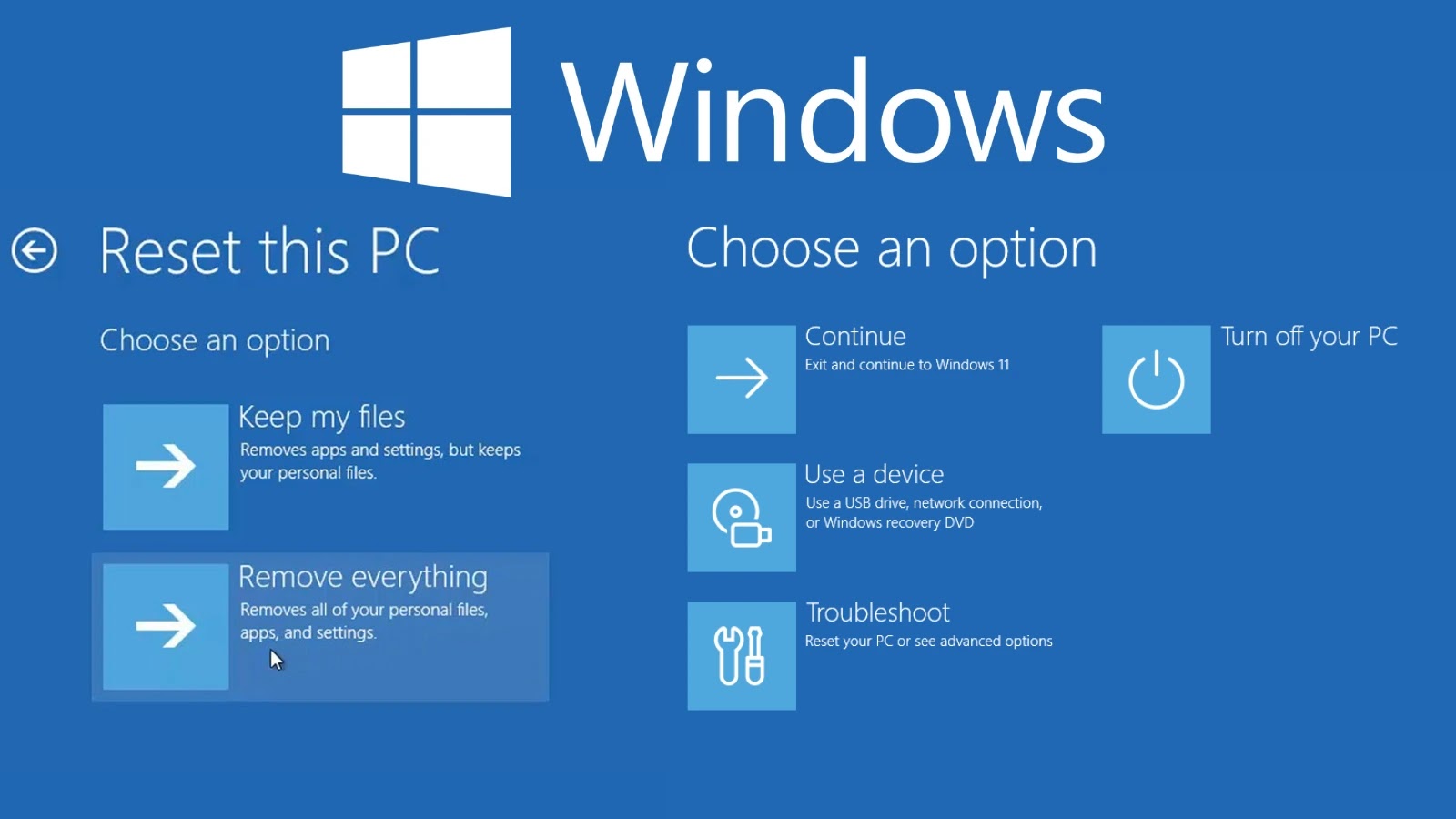
Microsoft has officially acknowledged that the August 2025 security update, designated as KB5063709, is causing failures in critical reset and recovery functionalities across multiple Windows versions. This issue, identified shortly after the update’s release on August 12, 2025, affects a broad spectrum of client operating systems, potentially leaving users unable to perform essential troubleshooting or device resets.
Understanding the Issue
The problem originates from the installation of KB5063709, a monthly security update intended to address vulnerabilities and enhance system protections. According to Microsoft’s advisory dated August 18, 2025, attempts to reset or recover affected devices may fail entirely. This includes common recovery methods such as navigating to System > Recovery > Reset my PC or using System > Recovery > Fix problems using Windows Update. Enterprise users relying on the RemoteWipe Configuration Service Provider (CSP) for remote device management may also encounter similar disruptions.
The confirmation came swiftly after reports began surfacing, with Microsoft initiating an investigation at 6:03 PM PT on August 18 and updating the status by 6:44 PM the same day. Notably, the latest security update for Windows 11, known as the 24H2 update, may lead to problems with hard drives and solid-state drives, potentially resulting in failures and putting data at risk of corruption.
Affected Platforms: A Detailed Breakdown
To help users identify if they’re at risk, here’s a structured list of the impacted Windows versions:
– Windows 11, version 23H2: The latest consumer-focused build, popular among home users and professionals for its enhanced security features.
– Windows 11, version 22H2: An earlier iteration still widely used in enterprise environments for its stability.
– Windows 10, version 22H2: A staple for organizations not yet migrated to Windows 11, including many with legacy hardware.
– Windows 10 Enterprise LTSC 2021 and Windows 10 IoT Enterprise LTSC 2021: Long-term servicing channels favored in industrial and embedded systems where updates are infrequent.
– Windows 10 Enterprise LTSC 2019 and Windows 10 IoT Enterprise LTSC 2019: Older LTSC variants, often deployed in mission-critical setups like medical devices or manufacturing.
It’s important to note that no server editions, such as Windows Server 2022 or older, are listed as vulnerable, which is a relief for data center operators.
Microsoft’s Response and Recommendations
Microsoft has been proactive in addressing this issue, promising an out-of-band update in the coming days to resolve the problem. Until then, users are advised to avoid initiating resets or recoveries on affected systems.
For those in high-stakes environments, alternatives include booting from external media like a Windows installation USB to perform repairs, though this requires technical expertise and access to recovery tools.
Microsoft has committed to providing more details as the fix progresses, urging users to check official support channels for updates. In the meantime, here’s a quick action plan for affected parties:
– Backup Data Immediately: Ensure critical files are secured externally before any issues arise.
– Delay Resets: Postpone any planned device wipes or recoveries until the patch is available.
– Monitor for Exploits: Stay vigilant for any related vulnerabilities that could be exploited in conjunction with this glitch.
– Enterprise Admins: Test the update in isolated environments and prepare rollback strategies.
Broader Implications and Context
This incident underscores the complexities involved in maintaining and updating large-scale operating systems. While security updates are essential for protecting systems against emerging threats, they can sometimes introduce unforeseen issues that disrupt critical functionalities.
In recent years, Microsoft has made significant strides in enhancing the resilience and security of its operating systems. For instance, the introduction of the Windows Resiliency Initiative aims to fortify Windows against emerging threats, with a particular focus on preventing phishing attacks. This initiative encompasses areas such as strengthened reliability, reduced administrative privileges, enhanced app and driver controls, and improved identity protection.
Additionally, Microsoft has unveiled features like Quick Machine Recovery (QMR), designed to enable IT administrators to execute targeted fixes remotely on PCs, even when they are unable to boot. This innovation is part of a broader effort to minimize downtime and streamline recovery processes when system failures occur.
However, the recent issues with KB5063709 highlight the challenges that can arise even with well-intentioned updates. Users and administrators must remain vigilant, ensuring that they have robust backup and recovery plans in place and staying informed about potential issues through official channels.
Conclusion
The confirmation of disruptions caused by the August 2025 security update serves as a reminder of the delicate balance between implementing necessary security measures and maintaining system stability. As Microsoft works to resolve this issue, users are encouraged to follow the recommended action plan, stay informed through official updates, and exercise caution when performing system resets or recoveries.