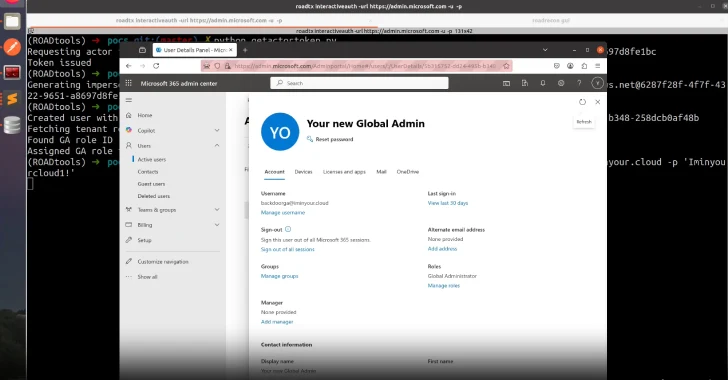
Microsoft has recently patched a critical vulnerability in its Entra ID (formerly Azure Active Directory) that could have permitted attackers to impersonate any user, including Global Administrators, across any tenant. This flaw, identified as CVE-2025-55241, received the highest possible CVSS score of 10.0, indicating its severity. The company addressed the issue on July 17, 2025, and confirmed that no customer action is required.
Discovery and Reporting
Security researcher Dirk-jan Mollema discovered and reported the vulnerability on July 14, 2025. He highlighted that this flaw had the potential to compromise every Entra ID tenant globally, with the likely exception of national cloud deployments.
Technical Details
The vulnerability stemmed from two primary issues:
1. Service-to-Service (S2S) Actor Tokens: These tokens, issued by the Access Control Service (ACS), are designed for secure communication between services.
2. Inadequate Validation in Azure AD Graph API: The legacy Azure AD Graph API (graph.windows.net) failed to properly validate the originating tenant. This oversight allowed the S2S tokens to be used for unauthorized cross-tenant access.
This combination meant that attackers could craft tokens that tricked Entra ID into recognizing them as any user within any tenant. Notably, these tokens were subject to Microsoft’s Conditional Access policies, enabling unauthorized modifications through the Graph API. Furthermore, the lack of API-level logging for the Graph API meant that such exploits could occur without detection.
Potential Impact
If exploited, this vulnerability could have severe consequences:
– Global Administrator Impersonation: Attackers could impersonate Global Administrators, granting them the ability to create new accounts, assign permissions, and exfiltrate sensitive data.
– Full Tenant Compromise: With Global Admin access, attackers could control any service that uses Entra ID for authentication, including SharePoint Online and Exchange Online.
– Azure Resource Access: Global Admins can grant rights on Azure subscriptions, potentially giving attackers full access to resources hosted in Azure.
Microsoft’s Response
Microsoft characterized such cross-tenant access as High-privileged access (HPA), where an application or service gains broad access to customer content, allowing it to impersonate other users without proof of user context. The company has since deprecated and retired the Azure AD Graph API as of August 31, 2025, urging users to migrate to Microsoft Graph.
Security Community Insights
Cloud security firm Mitiga emphasized the gravity of this vulnerability, noting that successful exploitation could bypass multi-factor authentication (MFA), Conditional Access, and logging mechanisms, leaving no trace of the incident. They highlighted that attackers could craft actor tokens in ways that deceived Entra ID into recognizing them as any user, anywhere.
Conclusion
The swift identification and remediation of CVE-2025-55241 underscore the importance of proactive security measures and timely patching. Organizations are advised to stay updated with Microsoft’s security advisories and ensure their systems are protected against such critical vulnerabilities.