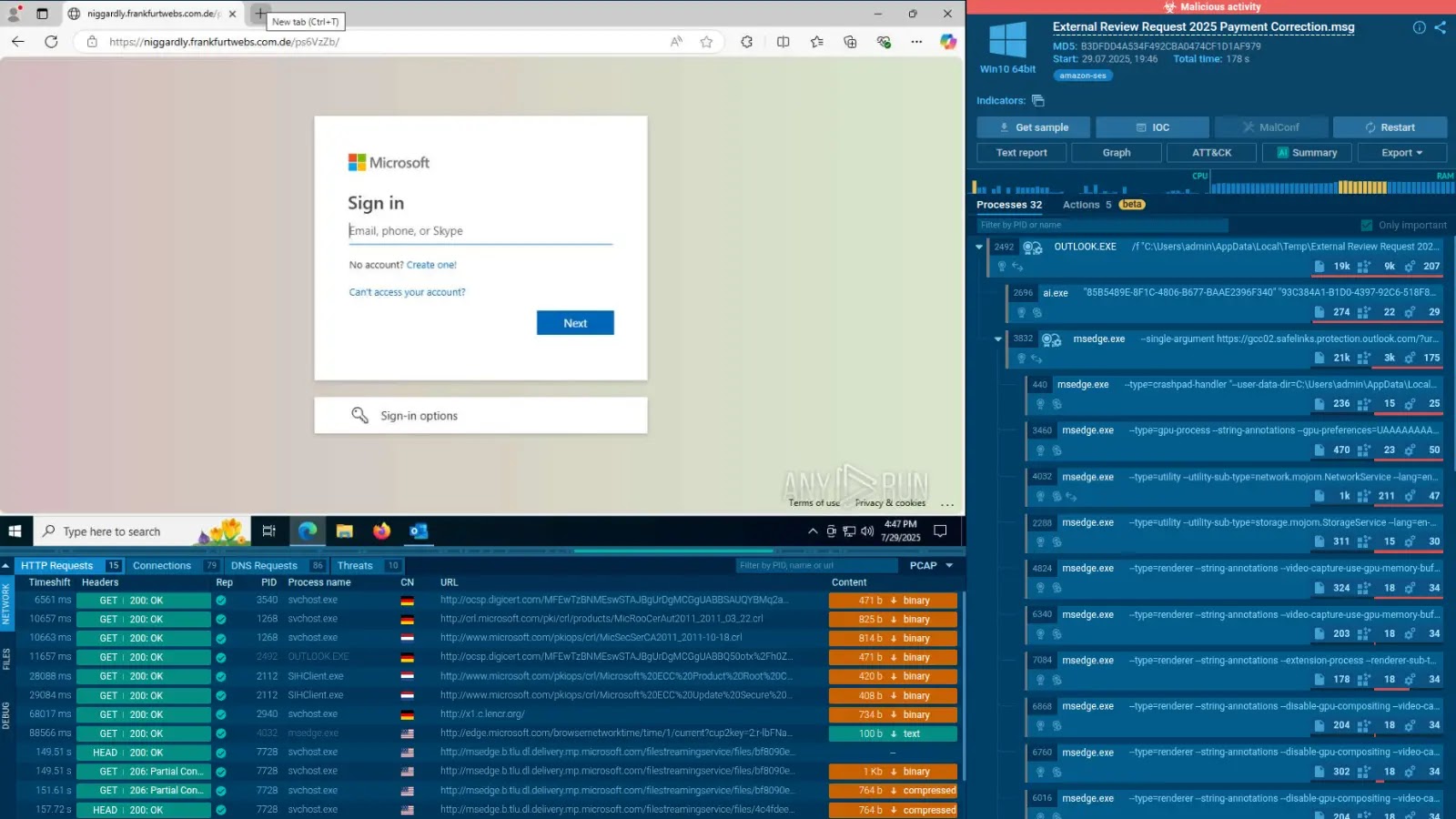
In today’s digital landscape, cybersecurity transcends mere defense mechanisms; it is integral to safeguarding a company’s financial health. Organizations lacking sophisticated threat intelligence (TI) systems often grapple with escalating breach costs, misallocated resources, and operational inefficiencies that directly impact their bottom line. Implementing actionable threat intelligence can empower businesses to reduce expenses, streamline operations, and mitigate risks before they escalate into significant issues.
The High Cost of Inadequate Threat Intelligence
Security Operations Centers (SOCs) that operate without high-quality threat intelligence often face inefficiencies and increased staff burnout. Analysts are burdened with manually processing thousands of alerts, many of which are false positives. This not only wastes valuable time and financial resources but also increases the likelihood of overlooking genuine threats. Such a reactive approach can lead to high employee turnover rates, with false positives costing enterprises up to $1.3 million annually in labor alone. Moreover, burnout makes staff twice as likely to seek new employment opportunities.
Undetected threats can evolve into financial catastrophes, exploiting gaps in visibility and slow response times. Generic threat intelligence feeds often fail to detect sophisticated attacks, allowing breaches to result in operational downtime, regulatory fines, and erosion of customer trust. As of 2025, the global average cost of a data breach is $4.44 million, with U.S. organizations facing an average of $10.22 million per incident. Alarmingly, nearly 20% of small and medium-sized businesses (SMBs) risk closure following a successful cyberattack.
Compliance deficiencies further expose organizations to fines and legal challenges, as regulatory bodies demand proactive threat documentation. Without real-time threat intelligence, audits may uncover shortcomings, leading to penalties such as the General Data Protection Regulation (GDPR) fines of up to 4% of global revenue or €20 million, and Health Insurance Portability and Accountability Act (HIPAA) violations exceeding $1.5 million per incident.
Five Strategies for Cost Savings with Threat Intelligence
Integrating advanced threat intelligence into business operations can lead to substantial cost savings and enhanced security. Here are five strategies to achieve this:
1. Proactive Breach Prevention
Implementing real-time threat intelligence feeds that provide data on indicators of compromise (IOCs) allows businesses to prevent breaches before they occur. These feeds can integrate with firewalls and Endpoint Detection and Response (EDR) tools to automatically block threats such as malicious domains. For instance, platforms like ANY.RUN offer 24 times more IOCs derived from global SOC data, enabling rapid risk isolation and reducing the likelihood of breaches by up to 70% through predictive insights into attacker behavior.
2. Reduction of False Positives
High-quality threat intelligence enriches alerts with context regarding threat actors and their tactics, techniques, and procedures (TTPs). This enrichment reduces the time spent investigating benign events and alleviates alert fatigue, which can consume up to 30% of an analyst’s working hours. Tools like ANY.RUN’s Threat Intelligence Lookup prioritize high-risk threats through Security Information and Event Management (SIEM) integrations, potentially saving up to 50% in labor costs by focusing teams on verified dangers rather than noise.
3. Automated Triage to Lower Labor Costs
Automating the triage process through threat intelligence APIs that connect with Security Orchestration, Automation, and Response (SOAR) and EDR systems provides instant sandbox context, reducing the need for manual escalations and empowering junior analysts. ANY.RUN’s Software Development Kit (SDK) automates artifact enrichment, minimizing staff turnover and overtime while increasing SOC capacity by 20-30% without the need for additional hires.
4. Accelerated Incident Response
Threat intelligence enhances incident response by offering comprehensive attack visibility from single IOCs, thereby shortening the Mean Time to Respond (MTTR) by 40-60%. Sandbox reports on malware behaviors enable precise containment strategies that can reduce downtime costs—potentially up to $100,000 per hour—and prevent revenue loss from prolonged incidents.
5. Effortless Maintenance of Up-to-Date Defenses
Continuous updates from threat intelligence feeds deliver real-time, unique IOCs with MITRE ATT&CK mappings, automating adaptations to evolving threats like ransomware without manual intervention. ANY.RUN’s query notifications keep defenses proactive, reducing breach risks by 50% and avoiding costs associated with outdated static feeds.
Case Study: Enhancing Security in the Transportation Sector
An international transportation company faced challenges with phishing and malware attacks. By adopting ANY.RUN’s Threat Intelligence Lookup, the company automated the tracking of geo-targeted threats and Common Vulnerabilities and Exposures (CVEs). Utilizing custom queries and real-time updates, the organization swiftly created security rules, significantly reducing manual research efforts and improving detection speed. This proactive approach enabled the company to block attacks preemptively, optimize resource allocation, and strengthen defenses against evolving attacker tactics.
Conclusion
Integrating advanced threat intelligence into business operations is not merely a defensive measure; it is a strategic investment that protects profits and enhances operational efficiency. By proactively preventing breaches, reducing false positives, automating triage processes, accelerating incident responses, and maintaining up-to-date defenses, organizations can achieve substantial cost savings and bolster their cybersecurity posture. Embracing solutions like ANY.RUN’s Threat Intelligence Feeds and Lookup transforms security from a cost center into a profit protector, ensuring businesses remain resilient in the face of an ever-evolving threat landscape.