In a significant cybersecurity development, researchers have identified 175 malicious packages within the npm registry, collectively downloaded approximately 26,000 times. These packages serve as the backbone for a sophisticated phishing campaign, dubbed Beamglea, which has set its sights on more than 135 industrial, technology, and energy companies worldwide.
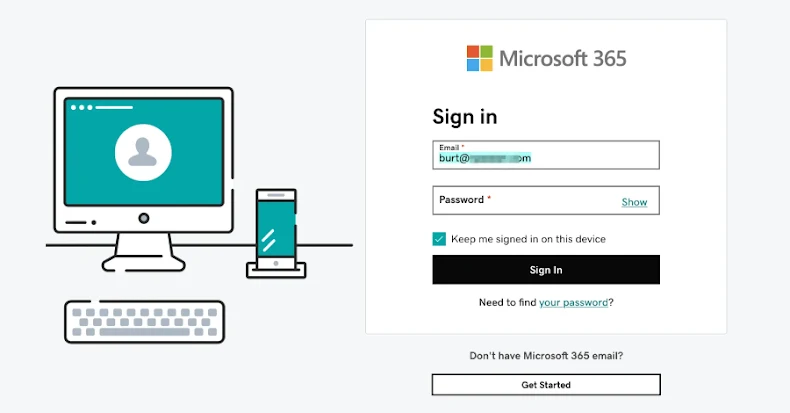
The campaign’s modus operandi involves leveraging npm’s public registry and the content delivery network (CDN) unpkg.com to host redirect scripts. These scripts are designed to funnel unsuspecting victims to credential harvesting pages, primarily targeting Microsoft login credentials.
Mechanics of the Attack
Central to this campaign is a Python script named redirect_generator.py. This script automates the creation and publication of npm packages with names formatted as redirect-xxxxxx, where xxxxxx represents a random alphanumeric sequence. Within each package, the script embeds the victim’s email address and a custom phishing URL.
Once these packages are live on the npm registry, the attackers craft HTML files that reference the UNPKG CDN associated with the newly published package. For instance, a reference might look like unpkg[.]com/[email protected]/beamglea.js. When a victim opens such an HTML file, the embedded JavaScript loads from the UNPKG CDN and redirects the user to a phishing page designed to mimic Microsoft’s login portal.
The JavaScript file, beamglea.js, plays a pivotal role by including the victim’s email address and the destination URL for credential capture. Researchers have uncovered over 630 such HTML files masquerading as legitimate documents like purchase orders, technical specifications, or project plans.
Distribution and Execution
Unlike traditional malware, these npm packages don’t execute malicious code upon installation. Instead, they function as hosts for the phishing infrastructure. The exact distribution method of these HTML files remains uncertain, but it’s plausible that they are disseminated via emails that deceive recipients into opening the specially crafted files.
Upon opening these HTML files in a browser, the embedded JavaScript immediately redirects the user to the phishing domain, passing along the victim’s email address via a URL fragment. This tactic pre-fills the email field on the phishing page, lending an air of legitimacy and increasing the likelihood of the victim entering their credentials.
Implications and Insights
This campaign underscores the evolving strategies of cybercriminals who exploit legitimate infrastructures to orchestrate large-scale attacks. By publishing 175 packages across nine accounts and automating the generation of victim-specific HTML files, the attackers have established a resilient phishing framework that is cost-effective and leverages trusted CDN services.
The npm ecosystem, in this scenario, becomes an unwitting participant rather than a direct attack vector. Developers installing these packages may not observe any malicious behavior, but victims interacting with the crafted HTML files are redirected to phishing sites.
Recommendations for Developers and Organizations
1. Vigilant Package Management: Regularly audit and monitor the npm packages used in your projects. Be cautious of packages with randomized or unfamiliar names.
2. Email Scrutiny: Exercise caution with unsolicited emails containing HTML attachments, especially those purporting to be official documents.
3. User Education: Train employees to recognize phishing attempts and the importance of verifying the authenticity of login pages.
4. Implement Security Tools: Utilize security solutions that can detect and block malicious scripts and phishing attempts.
By adopting these measures, organizations can bolster their defenses against such sophisticated phishing campaigns and protect sensitive credentials from being compromised.