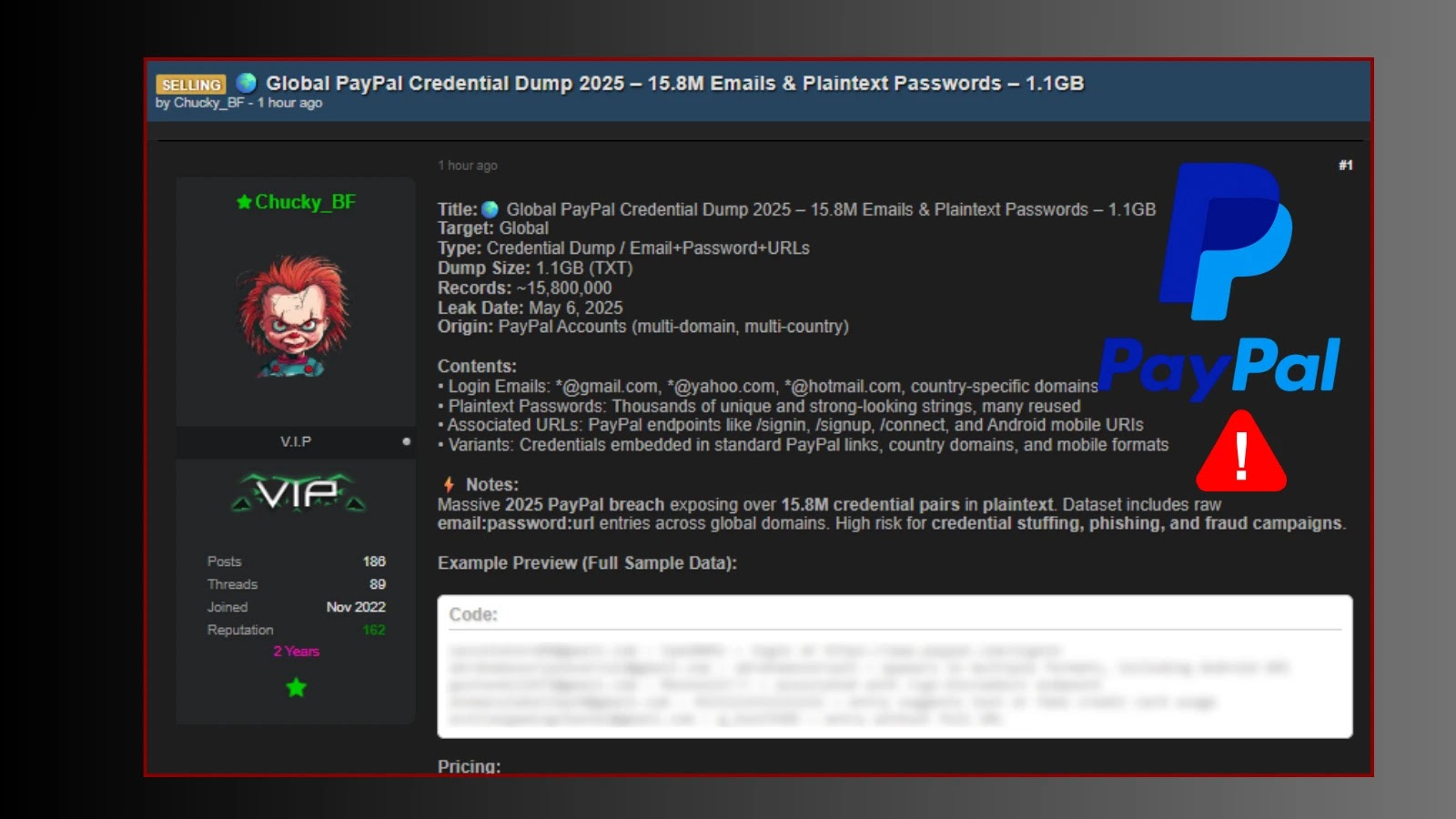
In a recent development that has sent shockwaves through the cybersecurity community, a threat actor known by the alias Chucky_BF has advertised a substantial dataset for sale on a prominent cybercrime forum. This dataset, ominously titled the Global PayPal Credential Dump 2025, purportedly contains over 15.8 million email and plaintext password pairs associated with PayPal accounts worldwide.
Details of the Alleged Breach
The dataset, approximately 1.16GB in size, is said to encompass credentials from a diverse range of PayPal accounts across multiple domains. The inclusion of plaintext passwords is particularly alarming, as it suggests that these credentials could be readily exploited without the need for decryption.
According to information shared by cybersecurity researcher Hackmanac, the leaked credentials include:
– Login Emails: A variety of email domains are represented, including widely used services such as @gmail.com, @yahoo.com, and @hotmail.com, as well as country-specific and lesser-known domains.
– Plaintext Passwords: The dataset reportedly contains both unique and commonly reused passwords, some exhibiting strong complexity. This raises significant concerns about the potential for password reuse across different platforms, increasing the risk of further compromises.
– Associated URLs: The credentials are linked to specific PayPal endpoints, including URIs for /signin, /signup, /connect, and Android mobile APIs. This information could facilitate targeted attacks on these specific services.
– Variants: The dataset also includes credentials embedded in standard PayPal links, country-specific domain formats, and mobile integrations, indicating a comprehensive collection of user data.
A sample snippet from the dataset reveals the raw format—email:password:url—highlighting the potential for credential stuffing attacks, targeted phishing campaigns, and large-scale fraud. The threat actor has indicated that the data was leaked on May 6, 2025, and has suggested its utility for phishing campaigns and security testing by malicious entities.
Implications and Expert Analysis
While the full authenticity and scope of the dataset have yet to be independently verified, the potential implications are severe. If the credentials are genuine, attackers could automate login attempts across PayPal and other web services, exploiting reused credentials to gain unauthorized access.
Cybersecurity expert Troy Hunt has weighed in on the situation, noting that the presence of plaintext passwords suggests they were obtained through means other than a direct breach of PayPal’s systems. He posits that methods such as information-stealing malware or previous credential stuffing attacks could be responsible for the compilation of this dataset.
Recommended Actions for PayPal Users
In light of this potential breach, it is imperative for all PayPal account holders to take immediate action to secure their accounts:
1. Change Passwords: Immediately reset your PayPal password, ensuring that the new password is strong, unique, and not used on any other platform.
2. Enable Multi-Factor Authentication (MFA): Activate MFA on your PayPal account to add an additional layer of security, making it more difficult for unauthorized users to gain access.
3. Monitor Account Activity: Regularly review your PayPal account for any unauthorized transactions or suspicious activity.
4. Be Vigilant Against Phishing Attempts: Be cautious of emails or messages requesting personal information or directing you to unfamiliar websites, as these could be phishing attempts leveraging the leaked data.
Broader Cybersecurity Implications
This incident underscores the critical importance of robust password management and the implementation of multi-factor authentication across all online services. It also highlights the need for organizations to proactively monitor for data breaches and to educate users on best practices for securing their accounts.
As the investigation into this alleged credential dump continues, it serves as a stark reminder of the persistent threats in the digital landscape and the necessity for both individuals and organizations to remain vigilant in their cybersecurity efforts.