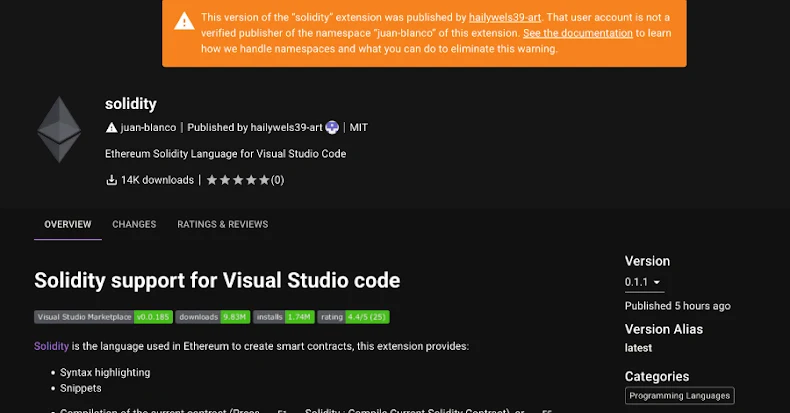
SleepyDuck: Malicious VSX Extension Exploits Ethereum for Persistent Control
Cybersecurity experts have recently identified a malicious extension within the Open VSX registry, known as SleepyDuck, which embeds a remote access trojan (RAT) to infiltrate developer environments. This extension, titled juan-bianco.solidity-vlang, was initially released as a benign tool on October 31, 2025. However, by November 1, after amassing 14,000 downloads, it was updated to version 0.0.8, introducing harmful functionalities.
John Tuckner from Secure Annex highlighted that the malware employs sophisticated sandbox evasion techniques and leverages an Ethereum smart contract to dynamically update its command-and-control (C2) server address, ensuring continuous operation even if the original server is decommissioned.
This incident is part of a broader trend where malicious extensions target Solidity developers through platforms like the Visual Studio Extension Marketplace and Open VSX. Notably, in July 2025, Kaspersky reported a case where a Russian developer lost $500,000 in cryptocurrency assets after installing a compromised extension via Cursor.
Mechanism of Operation:
Upon opening a new code editor window or selecting a `.sol` file, the SleepyDuck malware activates. It identifies the fastest Ethereum Remote Procedure Call (RPC) provider to access the blockchain and establishes communication with a remote server at sleepyduck[.]xyz through the contract address 0xDAfb81732db454DA238e9cFC9A9Fe5fb8e34c465. The malware then initiates a polling loop, checking every 30 seconds for new commands to execute on the host system.
Additionally, SleepyDuck collects system information—including hostname, username, MAC address, and timezone—and transmits these details to its server. If the primary domain is seized or taken down, the malware has fallback mechanisms to connect to predefined Ethereum RPC addresses to retrieve updated server information.
The extension can also fetch new configurations from the contract address to set up a new server and execute emergency commands across all infected endpoints if unexpected events occur. The associated Ethereum contract was created on October 31, 2025, with the threat actor updating server details from localhost:8080 to sleepyduck[.]xyz through four transactions.
There is speculation that the download counts may have been artificially inflated by the attackers to enhance the extension’s visibility in search results, a common tactic to deceive developers into installing malicious software.
Additional Malicious Extensions:
Secure Annex also uncovered another set of five malicious extensions published on the VS Code Extension Marketplace by a user named developmentinc. These extensions, now removed, included:
– developmentinc.cfx-lua-vs
– developmentinc.pokemon
– developmentinc.torizon-vs
– developmentinc.minecraftsnippets
– developmentinc.kombai-vs
One notable example is the Pokémon-themed extension, which, upon installation or activation, downloads a batch script miner from an external server (mock1[.]su:443) and executes it using cmd.exe. The script relaunches itself with administrative privileges via PowerShell, configures Microsoft Defender Antivirus exclusions for all drive letters from C: through Z:, downloads a Monero mining executable from mock1[.]su, and runs it.
Recommendations:
Developers are urged to exercise caution when downloading extensions, ensuring they originate from trusted publishers. Microsoft has announced periodic marketplace-wide scans to protect users against malware. Users can view removed extensions from the official marketplace on the RemovedPackages page on GitHub.