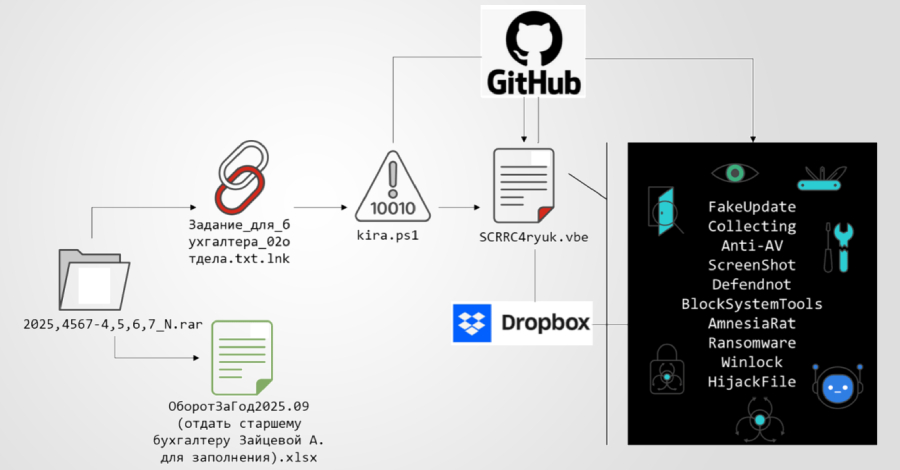
Cybersecurity researchers have recently identified malicious packages within the Python Package Index (PyPI) and npm repositories, underscoring the escalating threat of supply chain attacks targeting open-source ecosystems.
Discovery of Malicious PyPI Packages
A notable case involves the PyPI package named `termncolor`, which, upon installation, imports a dependency called `colorinal`. This dependency initiates a multi-stage malware operation. Once executed, `colorinal` loads a rogue DLL that decrypts and runs the next-stage payload. This payload deploys a legitimate binary, `vcpktsvr.exe`, and a DLL named `libcef.dll`, utilizing DLL side-loading to execute malicious code. The malware collects system information and communicates with a command-and-control (C2) server via Zulip, an open-source chat application, effectively concealing its activities. Persistence is achieved by creating a registry entry under the Windows Run key, ensuring the malware executes automatically at system startup. Notably, this malware also targets Linux systems by dropping a shared object file named `terminate.so` to replicate its functionality. Both `termncolor` and `colorinal` have been removed from PyPI following their discovery.
Malicious npm Packages Targeting Developers
Simultaneously, threat actors have been exploiting npm packages to target developers. Under the guise of job assessments, attackers trick developers into cloning GitHub repositories containing malicious npm packages. These packages are designed to harvest sensitive data, including iCloud Keychain information, web browser data, and cryptocurrency wallet details, which are then exfiltrated to external servers. The malicious npm packages also download and execute Python scripts, capture system information, scan file systems for sensitive files, steal credentials, log keystrokes, take screenshots, and monitor clipboard content. Identified packages such as `redux-ace` and `rtk-logger` have been removed from npm to mitigate further risk.
Broader Implications and Recent Incidents
These incidents are part of a broader trend of increasing supply chain attacks targeting open-source repositories. For instance, in November 2023, 48 malicious npm packages were discovered deploying reverse shells on developer systems. These packages, deceptively named to appear legitimate, contained obfuscated JavaScript designed to initiate a reverse shell upon installation. Similarly, in March 2025, malicious PyPI packages were found stealing cloud access tokens, with over 14,100 downloads before their removal. These packages masqueraded as utilities related to time but harbored hidden functionality to exfiltrate sensitive data.
Recommendations for Developers
The recurrence of such attacks highlights the critical need for developers to exercise caution when incorporating third-party packages into their projects. To mitigate risks, developers should:
– Verify Package Authenticity: Ensure that packages are sourced from reputable authors and have a history of legitimate use.
– Review Code Thoroughly: Examine the codebase of third-party packages for any suspicious or obfuscated code.
– Monitor Dependencies: Regularly update and monitor dependencies to identify and address potential vulnerabilities promptly.
– Implement Security Tools: Utilize security tools and services that can detect and alert on malicious packages and unusual behaviors.
By adopting these practices, developers can enhance the security of their software supply chains and protect their systems and data from malicious actors.