Introducing MAD-CAT: A Tool to Simulate and Defend Against Meow Data Corruption Attacks
In the ever-evolving landscape of cybersecurity, the emergence of tools like MAD-CAT (Meow Attack Data Corruption Automation Tool) marks a significant advancement in proactive defense strategies. Developed by security researcher Karl Biron of Trustwave, MAD-CAT is a Python-based utility designed to replicate the infamous Meow attacks that have plagued various database systems.
Background on Meow Attacks
The Meow attacks first surfaced in 2020, targeting exposed databases by overwriting their contents with random strings ending in -MEOW. This wave of attacks led to the loss of vast amounts of data across multiple platforms. Despite the passage of time, recent Shodan scans in 2025 have identified numerous databases still vulnerable to such exploits, underscoring the persistent threat posed by these attacks.
Purpose and Functionality of MAD-CAT
MAD-CAT was conceived to provide cybersecurity professionals with a means to simulate Meow-style data corruption attacks in a controlled environment. By doing so, organizations can assess their systems’ vulnerabilities and implement necessary safeguards without the risk of actual data loss.
The tool is compatible with six major database platforms:
– MongoDB
– Elasticsearch
– Cassandra
– Redis
– CouchDB
– Hadoop HDFS
These platforms were specifically chosen as they were the primary targets during the original Meow attack wave.
Operational Modes and Features
MAD-CAT offers two primary operational modes:
1. Non-Credentialed Mode: This mode targets open database instances without requiring authentication, mimicking opportunistic exploits.
2. Credentialed Mode: Designed for setups with weak authentication, this mode allows users to test systems that require login credentials.
Users can conduct tests on individual targets or perform bulk assessments using CSV lists, making it suitable for large-scale simulations. The tool’s architecture follows a factory pattern, facilitating easy extension to support additional databases and encouraging community contributions.
Command-Line Interface and Options
MAD-CAT’s command-line interface provides various options to tailor the simulation:
– Service Selection (`-s`): Specify the database service to target.
– Port Specification (`-p`): Define the port number for the target service.
– Verbose Output (`-v`): Enable detailed output for monitoring the simulation process.
– List Supported Services (`–list`): Display all supported database services, highlighting Hadoop’s inclusion due to its frequent treatment as a database in enterprise settings.
Simulation Process
The simulation conducted by MAD-CAT involves a four-phase process:
1. Connection: Establish a link to the target database.
2. Enumeration: Identify user databases and collections, excluding system ones.
3. Data Retrieval: Fetch existing records from the identified collections.
4. Data Corruption: Overwrite string and numeric fields with 10-character random alphanumeric strings appended with -MEOW.
This method ensures that the simulation closely mirrors the signature of actual Meow attacks, providing realistic scenarios for testing and analysis.
Verification and Setup
To verify the integrity of data before and after simulations, MAD-CAT includes a companion script, `fetch_data.py`. This script allows users to pull contents by service or collectively, facilitating comprehensive assessments.
For ease of setup, MAD-CAT provides a Docker Compose file that launches all six supported databases with vulnerable configurations and seeded sample data through initialization scripts. Executing `sudo docker-compose up` sets up a bridged network with persistent volumes and sequentially initializes the services, confirming readiness with done statuses.
Practical Application Examples
MongoDB:
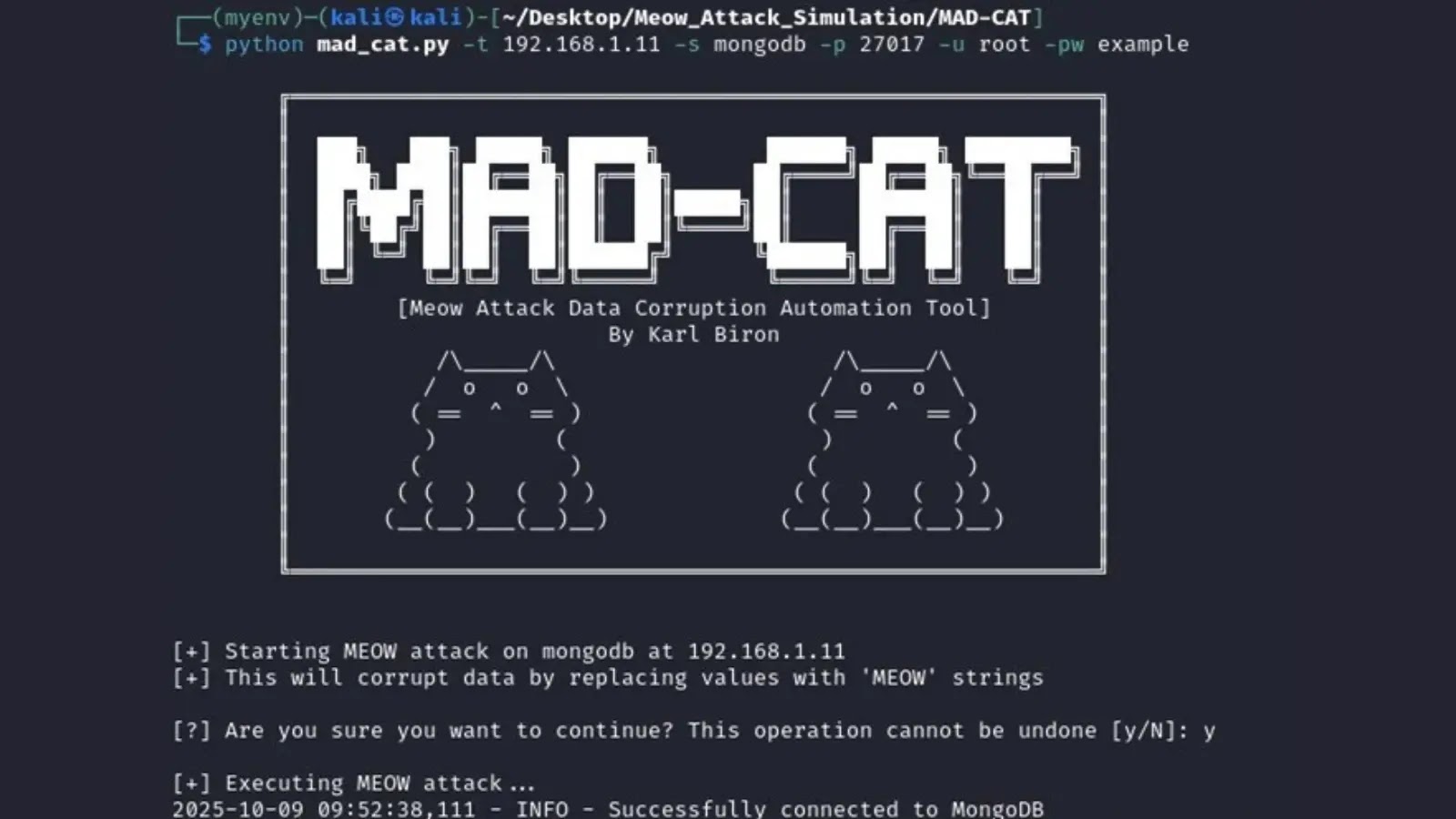
MongoDB, known for its schema flexibility, is a common target due to frequent misconfigurations. An initial run of `fetch_data.py mongo` reveals clean documents. Executing `python mad_cat.py -t 192.168.1.11 -s mongodb -p 27017 -u root -pw example` connects to the database, enumerates collections, and corrupts records seamlessly. Post-attack retrieval shows all values altered with -MEOW, potentially crippling applications handling sensitive information and leading to compliance breaches.
Elasticsearch:
As a core component of ELK stacks for logs and search functionalities, Elasticsearch is susceptible to index poisoning through data corruption, disrupting analytics and e-commerce features. A pre-attack fetch dumps intact JSON data. Running `python mad_cat.py -t 192.168.1.12 -s elasticsearch -p 9200 -u admin -pw secret` rewrites documents, resulting in indices filled with corrupted data.
Cassandra:
Cassandra, a high-throughput wide-column store used for big data applications, can experience widespread data corruption across clusters. Executing `python mad_cat.py -t 192.168.1.13 -s cassandra -p 9042` updates CQL tables, with post-attack data retrieval showing pervasive -MEOW alterations.
Implications and Recommendations
The development and utilization of MAD-CAT underscore the critical need for robust security measures, including proper authentication, firewall implementation, and continuous monitoring of exposed databases. By simulating real-world data corruption attacks, organizations can proactively identify vulnerabilities and fortify their defenses against potential threats.