On May 7, 2025, the notorious LockBit ransomware group experienced a significant security breach that led to the defacement of their dark web infrastructure and the public release of a comprehensive database containing sensitive operational details. This incident marks a substantial setback for one of the world’s most prolific ransomware organizations.
Defacement and Data Leak
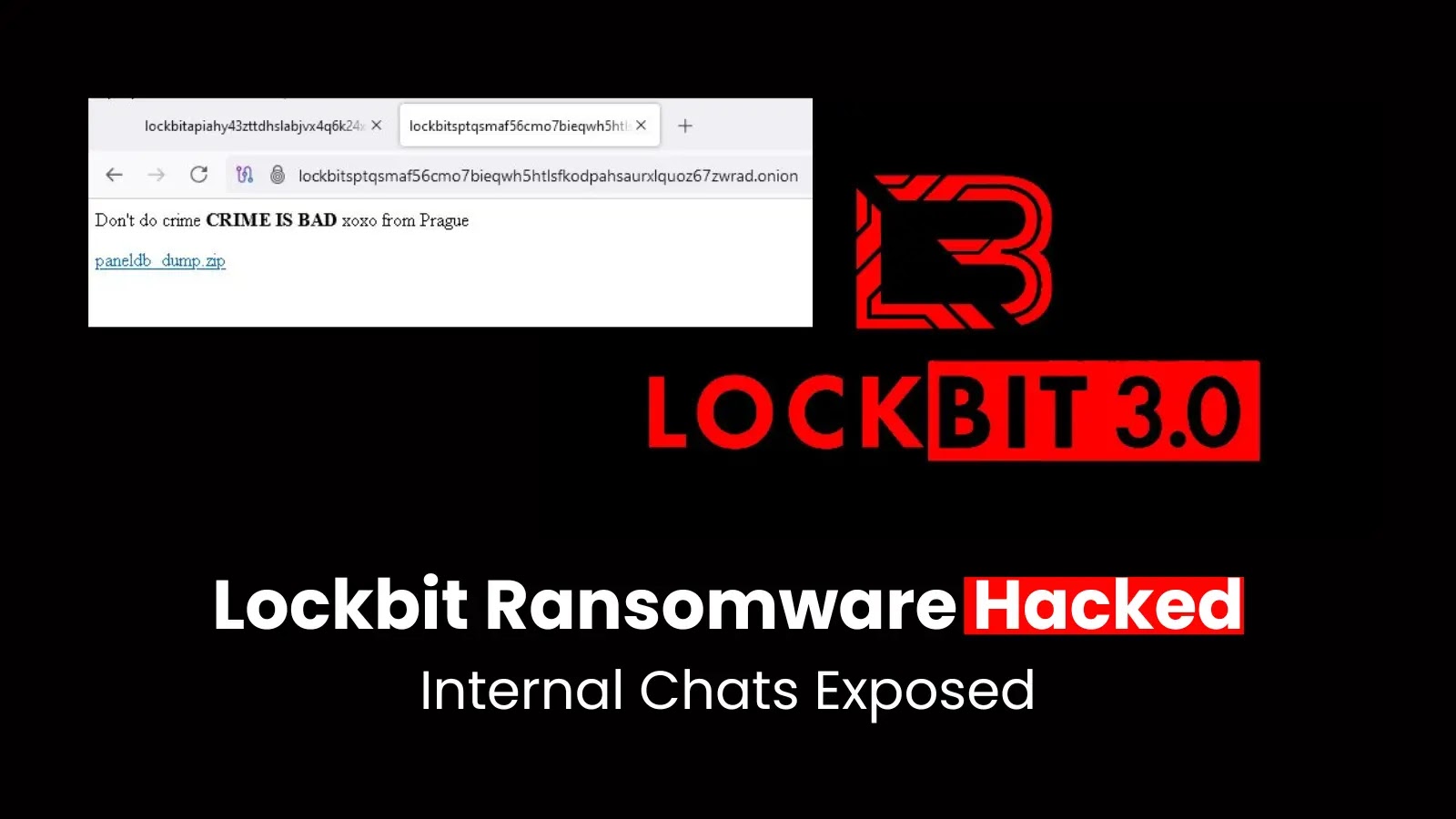
Visitors to LockBit’s dark web sites were met with a defiant message stating, Don’t do crime CRIME IS BAD xoxo from Prague, accompanied by a link to download a file named paneldb_dump.zip. This file contains a MySQL database dump, which has been confirmed by security researchers to be authentic. The leaked data encompasses approximately 60,000 unique Bitcoin wallet addresses used for ransom payments, 4,442 negotiation messages between LockBit operators and their victims spanning from December to late April, and details of custom ransomware builds created for specific attacks.
Exposure of Internal Credentials
Embarrassingly for LockBit, the leak also exposed a user table containing plaintext passwords for 75 administrators and affiliates. Alon Gal, Co-Founder and CTO at Hudson Rock, described the breach as a goldmine for law enforcement that could significantly aid in tracing cryptocurrency payments and attributing attacks to specific threat actors.
LockBit’s Response
In response to the breach, LockBit attempted to downplay the incident. In a message posted on their leak site in Cyrillic text, the group claimed: On May 7, they hacked the light panel with autoregistration for everyone, took the database, not a single decryptor and not a single stolen company data was affected. The group has offered payment for information about the Prague-based hacker responsible for the breach.
Context and Implications
This hack comes just months after Operation Cronos, a coordinated law enforcement action that temporarily disrupted LockBit’s infrastructure in February 2024. While the group managed to rebuild and resume operations after that takedown, its reputation had already suffered significant damage. Researchers noted that many of its recent victim claims were recycled from earlier attacks or from other ransomware groups.
The breach resembles a recent attack against the Everest ransomware operation, which used an identical defacement message. Cybersecurity researchers speculate that both attacks might be related to a critical vulnerability in PHP 8.1.2 (CVE-2024-4577) that allows for remote code execution.
For LockBit, which was responsible for approximately 44% of all ransomware incidents globally in early 2023, this breach represents a potentially devastating setback that could undermine affiliate trust and further hinder their operations.