Advanced Persistent Threats (APTs) represent some of the most sophisticated and damaging cyber threats facing organizations today. Unlike conventional cyberattacks, APTs involve highly skilled adversaries who infiltrate networks and maintain a covert presence over extended periods, often months or even years. Their primary objectives include data exfiltration, espionage, or causing significant operational disruptions. Given their stealthy nature and persistence, APTs pose a formidable challenge to traditional security measures.
Understanding the APT Landscape
APTs are meticulously planned and executed by threat actors, including state-sponsored groups and organized cybercriminal organizations. These attackers employ advanced techniques such as custom malware, zero-day exploits, and social engineering to infiltrate networks. Once inside, they establish multiple backdoors and redundant entry points to ensure prolonged access, allowing them to continuously extract valuable information or disrupt critical operations without triggering alarms.
The impact of APTs on organizations can be devastating and multifaceted. Financial losses from these attacks can include direct theft of assets, regulatory fines for data breaches, forensic investigation costs, and revenue losses from business disruption. Beyond financial implications, APTs frequently target intellectual property, customer information, and strategic business data, potentially crippling an organization’s competitive advantage.
Stages of an APT Attack
APTs typically progress through several stages:
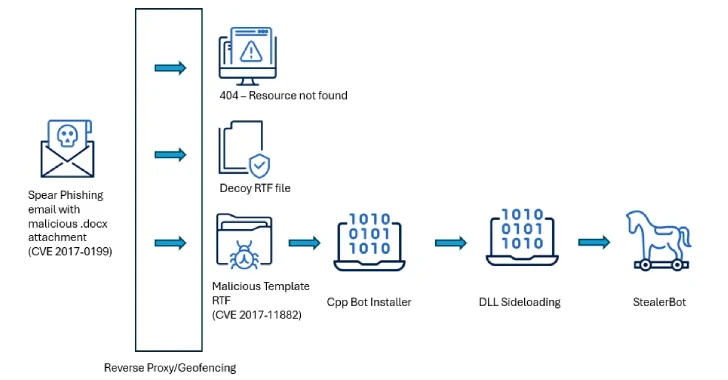
1. Infiltration: Attackers gain initial access to the target network, often through social engineering tactics like spear-phishing emails or exploiting vulnerabilities in web applications.
2. Expansion: Once inside, attackers establish their presence by compromising additional systems and user accounts, moving laterally within the network to access sensitive data.
3. Extraction: The final stage involves exfiltrating the stolen data. Attackers may use sophisticated methods to transfer data out of the network, sometimes employing diversionary tactics like Distributed Denial-of-Service (DDoS) attacks to distract security teams.
The Role of Threat Intelligence in Combating APTs
To effectively defend against APTs, organizations must adopt a proactive and intelligence-driven approach. Threat intelligence plays a crucial role in this strategy by providing insights into potential threats, attacker tactics, and indicators of compromise (IOCs).
Building an Effective Threat Intelligence Platform
An effective Threat Intelligence Platform (TIP) involves several key components:
1. Data Collection and Analysis:
– Comprehensive Data Gathering: Collect intelligence from diverse sources, including internal logs from firewalls, intrusion detection systems, and endpoint detection tools, as well as external sources like open-source intelligence, industry alerts, and government advisories.
– Contextual Analysis: Analyze the collected data in the context of the organization’s specific risk profile. This helps in filtering out irrelevant information and focusing on threats that pose a real risk.
2. Implementation and Integration:
– Integration with Security Tools: Connect the TIP with existing Security Information and Event Management (SIEM) systems and endpoint detection tools to enable unified threat detection and response.
– Automated Response Actions: Set up automated workflows to respond to identified threats, such as blocking malicious IP addresses, isolating compromised systems, and quarantining suspicious files.
Utilizing Threat Intelligence to Detect and Mitigate APTs
Threat intelligence can be leveraged in several ways to detect and mitigate APTs:
1. Identifying Indicators of Compromise (IOCs): By analyzing threat intelligence data, organizations can identify IOCs associated with APTs, such as specific malware signatures, command-and-control server addresses, and unusual network traffic patterns.
2. Behavioral Analysis: Monitor network and user behavior to detect anomalies that may indicate an APT presence. For example, unusual login times, unexpected data transfers, or unauthorized access to sensitive information can be signs of an APT.
3. Threat Hunting: Proactively search for signs of APT activity within the network using threat intelligence insights. This involves analyzing logs, network traffic, and endpoint data to uncover hidden threats.
4. Incident Response: Develop and refine incident response plans based on threat intelligence. This ensures that the organization can quickly and effectively respond to APT incidents, minimizing potential damage.
Case Studies: Applying Threat Intelligence Against APTs
Several real-world examples illustrate the effectiveness of threat intelligence in combating APTs:
1. APT41 (Wicked Panda): This China-based cyber espionage group has been known to use PowerShell backdoors to infiltrate systems. By monitoring for specific registry modifications and the use of legitimate tools like forfiles.exe for malicious purposes, organizations can detect and mitigate such threats.
2. MuddyWater APT: Linked to Iran, this group employs unique techniques to establish persistence using mutexes in their BugSleep backdoor. Security teams can detect infections by searching for specific mutex names and analyzing related sandbox sessions.
3. Lazarus Group: Attributed to North Korea, this group has engaged in fake job interview schemes targeting tech professionals to distribute malware. Monitoring for indicators associated with Lazarus-related threats can help in early detection and prevention.
Conclusion
Advanced Persistent Threats pose a significant challenge to organizations due to their sophisticated and stealthy nature. Traditional security measures are often insufficient to detect and mitigate these threats. By leveraging threat intelligence, organizations can gain valuable insights into potential threats, attacker tactics, and indicators of compromise. Building an effective Threat Intelligence Platform that integrates with existing security tools and enables automated response actions is crucial in defending against APTs. Proactive measures such as identifying IOCs, conducting behavioral analysis, engaging in threat hunting, and refining incident response plans based on threat intelligence can significantly enhance an organization’s ability to detect, mitigate, and respond to APTs effectively.