In today’s corporate landscape, major companies are streamlining operations, often reducing their workforce to enhance efficiency. For instance, Wells Fargo has decreased its staff by 23% over five years, Bank of America has let go of 88,000 employees since 2010, and Verizon’s CEO has highlighted a continuous reduction in headcount. While these measures are celebrated as signs of operational agility and AI-driven productivity, they pose significant challenges for Chief Information Security Officers (CISOs). With leaner teams, the repercussions of preventable security incidents become more severe, stretching already limited resources to their limits. In this context, hardcoded secrets emerge as a critical vulnerability that cannot be effectively managed through manual processes and reactive measures.
The Stark Reality of Credential Compromise
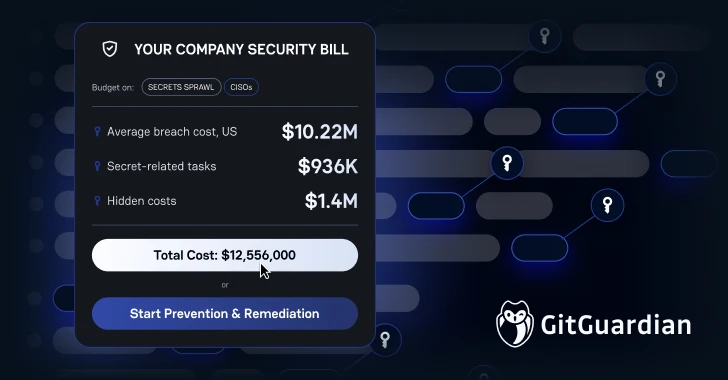
The issue of compromised credentials is both prevalent and costly. IBM’s recent research indicates that 86% of security breaches involve stolen or compromised credentials, with an average detection and containment period of 292 days. Financially, the stakes are escalating. In the U.S., the average cost of a data breach has reached $10.22 million, influenced by increased regulatory fines and detection expenses. Specifically, breaches involving hardcoded secrets carry an additional premium of $750,000, potentially elevating the total cost to over $11 million for affected organizations.
Beyond direct financial losses, the inefficiencies in managing secrets manually are substantial. Organizations spend approximately $1.4 million annually on these processes, including $936,000 on developer time for credential rotation and exposure investigations, and over $500,000 on security analysts addressing false positives and tracking leaked credentials. Real-world incidents underscore these challenges. For example, Canva experienced multiple days of downtime across various teams due to a single leaked secret, diverting engineering resources from core product development tasks.
Amplified Risks in Lean Operational Environments
Reducing workforce size correlates with extended mean-time-to-remediate incidents, making the 292-day average containment period even more perilous. Each security incident diverts already overstretched teams from essential business functions, introducing costly context-switching that lean organizations can ill afford. The problem’s scope continues to expand even as teams contract. Large organizations often have thousands of unmanaged secrets dispersed across code repositories, CI/CD pipelines, and collaboration platforms like Slack and Jira. Research indicates that up to 40% of these secrets are high-risk, frequently granting direct access to production environments.
This situation creates a compounding effect: a single hardcoded API key can facilitate lateral movement within networks, compromise supply chains, and enable large-scale ransomware attacks. The recent s1ngularity attack exemplifies this risk. It began with a GitHub Action token-stealing pull request that compromised Nx packages, leading to the theft of 2,349 credentials. This initial breach cascaded into attackers exposing an additional 82,901 secrets by making over 10,000 private repositories public.
Strategic Shift: Emphasizing Precision in Remediation
Addressing the challenge of hardcoded secrets requires a strategic shift from mere detection to effective remediation. Without efficient remediation processes, alerts can overwhelm already stretched teams, turning into costly noise. For CISOs managing lean security operations, recognizing this distinction is crucial. Secrets differ fundamentally from traditional vulnerabilities. While developers can often patch code vulnerabilities independently, remediating exposed secrets necessitates understanding the broader infrastructure context—identifying where the secret is used across multiple services, determining system dependencies, and establishing who has the authority to rotate it. This process typically requires coordination among development, platform, and DevOps teams, each with distinct priorities and workflows. Manually gathering this context becomes prohibitively expensive for security teams operating at full capacity, transforming what should be quick fixes into complex, multi-team investigations that can extend over weeks.
Advanced platforms now prioritize understanding the magnitude of exposure by providing contextual information, including roles, permissions, ownership, and threat scope. This holistic approach directly addresses the burden of false positives, which costs organizations over $500,000 annually in wasted analyst time.
Reducing Remediation Time from Weeks to Hours
Effective remediation frameworks align seamlessly with the constraints of lean teams:
– Proactive Detection: Implementing both preventive scanning during code commits and reactive scanning for existing leaks helps catch issues before they reach the average 292-day containment window.
– Clear Ownership: Modern tools assign ownership for each secret, ensuring responsible developers receive notifications with comprehensive context, eliminating time wasted in identifying secret owners.
– Informed Decision-Making: Teams receive precise location data, understand what each secret unlocks, and know whether it’s still active. This targeted approach prevents the annual productivity drain from manual investigation tasks.
– Workflow Integration: Developers receive clear remediation guidance directly within their existing tools, reducing the context-switching costs that plague smaller teams. Advanced platforms now offer automated secret revocation capabilities and can generate code-fixing pull requests directly within version control systems, meeting developers where they work rather than forcing them into separate security tools.
The Return on Investment of Smart Remediation
By pinpointing specific files and lines of code where secrets are hardcoded, this approach transforms the economics of incident response. Instead of developers spending hours searching codebases, they can focus their efforts precisely where needed. Real-time remediation tracking provides security teams with visibility without manual oversight. This precision approach directly addresses the core challenge facing downsized security teams: maintaining a robust security posture while doing more with less.