Kimwolf Botnet Compromises Over 2 Million Android Devices via Exposed ADB and Proxy Networks
The Kimwolf botnet has emerged as a significant cybersecurity threat, infecting over 2 million Android devices by exploiting vulnerabilities in exposed Android Debug Bridge (ADB) services and leveraging residential proxy networks. This large-scale infiltration has transformed compromised devices into conduits for malicious activities, including distributed denial-of-service (DDoS) attacks and unauthorized data relays.
Origins and Evolution of Kimwolf
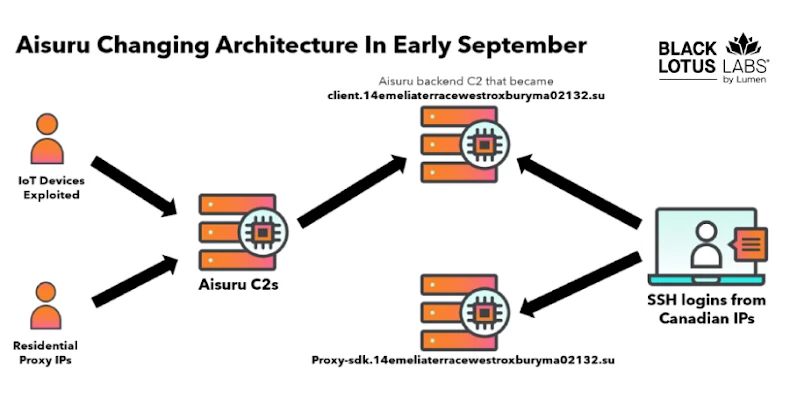
First identified by QiAnXin XLab in December 2025, Kimwolf is believed to be an Android variant of the AISURU botnet. Active since at least August 2025, Kimwolf has been linked to a series of record-setting DDoS attacks. The malware primarily targets Android-based smart TVs, set-top boxes, and tablets, with infections predominantly in countries like Vietnam, Brazil, India, and Saudi Arabia. Synthient’s analysis indicates that approximately 12 million unique IP addresses are associated with the botnet weekly.
Infection Mechanisms
Kimwolf’s propagation strategy involves targeting devices with exposed ADB services. A significant portion of these devices, about 67%, are unauthenticated and have ADB enabled by default, making them susceptible to attacks. The botnet utilizes scanning infrastructures that exploit residential proxy networks to install the malware. Notably, many compromised devices are unofficial Android-based smart TVs and set-top boxes, some of which come pre-infected with software development kits (SDKs) from proxy providers, enlisting them into the botnet without user knowledge.
Monetization Strategies
The operators behind Kimwolf employ multiple monetization avenues:
– App Installations: Distributing and installing applications on infected devices to generate revenue.
– Selling Proxy Bandwidth: Utilizing the compromised devices as part of residential proxy networks, offering their bandwidth for rent.
– DDoS Services: Leveraging the botnet’s scale to offer DDoS attack capabilities as a service.
Synthient’s findings reveal that Kimwolf infections have been associated with proxy IP addresses offered by China-based IPIDEA. In December 2025, IPIDEA implemented a security patch to block access to local network devices and sensitive ports, aiming to mitigate the misuse of their services.
Technical Infrastructure and Operations
Kimwolf’s operational framework is sophisticated:
– Command and Control (C2): The main payload listens on port 40860 and connects to specific IP addresses to receive further commands.
– Proxy Networks: The botnet leverages proxy networks to tunnel through local networks of systems running proxy software, facilitating malware distribution.
– Bandwidth Monetization: Infected devices are integrated with services like Plainproxies Byteconnect SDK, which uses relay servers to execute proxy tasks assigned by a command-and-control server.
Synthient detected the botnet’s infrastructure being used for credential-stuffing attacks targeting IMAP servers and popular online platforms.
Countermeasures and Recommendations
To combat the Kimwolf botnet, several measures are recommended:
– For Proxy Providers: Implement blocks on requests to private IP address ranges (RFC 1918 addresses) to prevent unauthorized access.
– For Organizations: Secure devices running unauthenticated ADB shells to prevent exploitation.
The discovery of pre-infected TV boxes and the monetization of these bots through SDKs like Byteconnect highlight a deepening relationship between threat actors and commercial proxy providers. This underscores the need for heightened vigilance and proactive security measures in the face of evolving cyber threats.