Critical Vulnerability in K7 Antivirus Grants Attackers SYSTEM-Level Access
A significant security flaw has been identified in K7 Ultimate Security, a product of K7 Computing, which could allow attackers to escalate privileges to SYSTEM level. This vulnerability arises from the misuse of named pipes with overly permissive access control lists (ACLs), enabling low-privileged users to manipulate registry settings without triggering User Account Control (UAC) prompts.
Discovery and Initial Findings
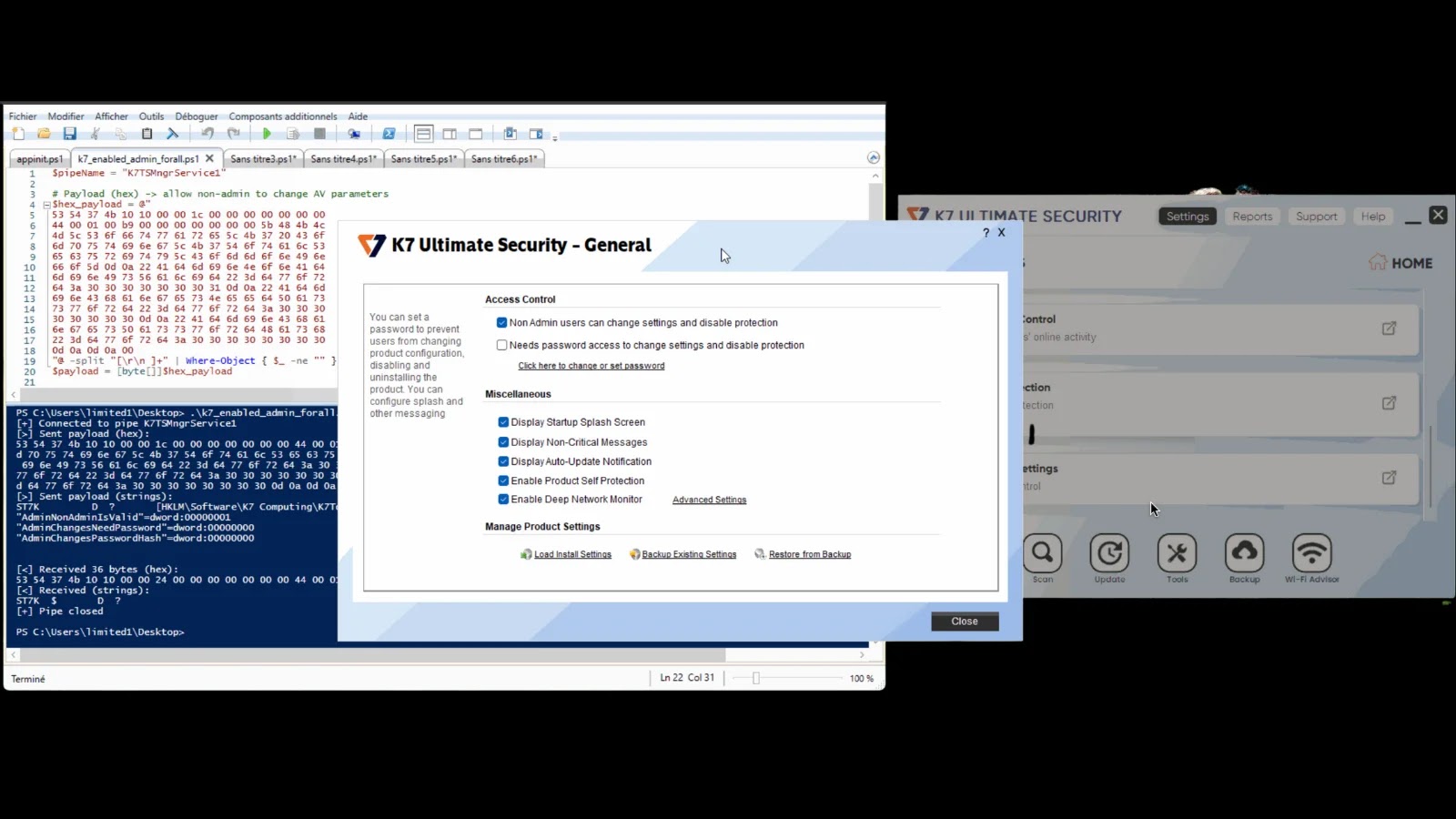
Security researcher Lucas Laise from Quarkslab uncovered this vulnerability while investigating an unrelated denial-of-service issue, designated as CVE-2024-36424, affecting K7RKScan.sys in versions prior to 17.0.2019. During tests on version 17.0.2045, it was observed that non-administrative users had limited functionality, such as the inability to modify configurations without elevation. However, administrators could enable a setting allowing non-admin users to change settings and disable protection without UAC prompts, indicating potential flaws in inter-process communication.
Technical Analysis
Tools like PipeViewer identified SYSTEM-owned named pipes, notably \.\pipe\K7MailProxyV1 with full permissions and \.\pipe\K7TSMngrService1, utilized by K7TSMain.exe for registry modifications. Further analysis using IoNinja confirmed that binary payloads sent to K7TSMngrService1 during setting changes were executed in the SYSTEM context. This communication pathway became the exploitation vector, allowing low-privilege processes to impersonate legitimate requests.
Attackers could replay captured packets via PowerShell to universally tamper with configurations, such as disabling real-time scans or whitelisting malware. A more refined approach targeted the registry key AdminNonAdminIsValid; by altering a single byte (changing B9 to B8 in hexadecimal), arbitrary values could be injected, bypassing validation mechanisms.
Exploitation for Privilege Escalation
To achieve full local privilege escalation, researchers exploited the Image File Execution Options (MITRE ATT&CK T1546.012) by setting a debugger on K7TSHlpr.exe. This method allowed the execution of arbitrary code as SYSTEM during simulated updates. A provided script could create a batch file to add new administrative users, trigger the update process, and subsequently clean up traces.
Patch Attempts and Bypasses
K7 Computing released three patches in response to these findings:
1. First Patch: Introduced caller validation on K7TSMngrService1. However, this was bypassed by manually mapping a DLL into k7tsmngr.exe.
2. Second Patch: Implemented via K7Sentry.sys driver version 22.0.0.70, aimed to block injection into protected processes. This was circumvented by using renamed signed K7 binaries, such as K7QuervarCleaningTool.exe, which were not included in the protected lists.
Root Cause Analysis
An in-depth analysis using IDA Pro revealed that the ValidatePipeClient function checks for the installation path, MD5 hashes, and K7 signatures, along with K7Sentry’s VDefProtectedProcs registry whitelist. Bypasses were achieved by utilizing unsigned or relocated signed binaries, effectively evading both pipe access controls and protection hooks.
Disclosure Timeline and Recommendations
The responsible disclosure process spanned from August to December 2025. Quarkslab notified K7 Computing on August 25, and after confirming bypasses of the initial patches, published their findings on December 2. K7 Computing acknowledged the issues and deferred full ACL enforcement to a future major release, recognizing the interim nature of the fixes.
User Advisory
Users are strongly advised to update to the latest versions of K7 Ultimate Security and remain vigilant for comprehensive remediation measures. For defensive analysis, exploit scripts have been made available on the Quarkslab blog.