Cybersecurity experts have identified a new ransomware variant named HybridPetya, which mirrors the infamous Petya and NotPetya malware strains. This sophisticated ransomware can circumvent the Secure Boot mechanism in Unified Extensible Firmware Interface (UEFI) systems by exploiting a vulnerability disclosed earlier this year.
Slovakian cybersecurity firm ESET reported that HybridPetya samples were uploaded to the VirusTotal platform in February 2025. The ransomware encrypts the Master File Table (MFT), a critical component containing metadata about all files on NTFS-formatted partitions. Unlike its predecessors, HybridPetya can compromise modern UEFI-based systems by installing a malicious EFI application onto the EFI System Partition.
The ransomware comprises two primary components: a bootkit and an installer. The bootkit, deployed by the installer, manages its configuration and monitors the encryption status. It can assume three states:
– 0: Ready for encryption
– 1: Already encrypted
– 2: Ransom paid, disk decrypted
When set to 0, the bootkit changes the flag to 1 and encrypts the \EFI\Microsoft\Boot\verify file using the Salsa20 encryption algorithm with a specified key and nonce. It also creates a file named \EFI\Microsoft\Boot\counter on the EFI System Partition to track encrypted disk clusters.
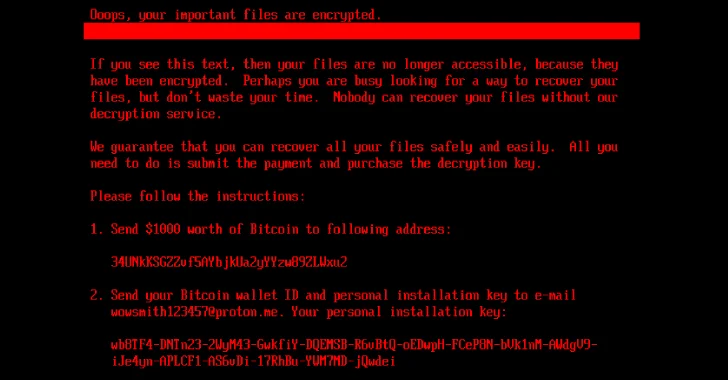
During encryption, the bootkit displays a fake CHKDSK message, misleading victims into believing the system is repairing disk errors. If the disk is already encrypted (flag set to 1), the bootkit presents a ransom note demanding $1,000 in Bitcoin. The ransom note includes an option for victims to enter a decryption key obtained after payment. Upon entering the correct key, the bootkit sets the flag to 2 and initiates the decryption process, reading the \EFI\Microsoft\Boot\counter file to determine the number of clusters to decrypt.
The decryption process involves restoring legitimate bootloaders from backups created during installation. Once completed, victims are prompted to reboot their Windows machines.
Notably, changes to the bootloader by the installer during UEFI bootkit deployment trigger a system crash (Blue Screen of Death), ensuring the bootkit binary executes upon device restart.
Some HybridPetya variants exploit CVE-2024-7344, a vulnerability in the UEFI Secure Boot process, allowing the malware to bypass security measures and gain control over the system’s boot process.