Security researchers have uncovered a sophisticated cyber threat actor, dubbed Hazy Hawk, actively exploiting DNS misconfigurations to hijack subdomains of prominent organizations worldwide. Since at least December 2023, Hazy Hawk has been leveraging abandoned cloud resources to disseminate scams and malware, posing significant risks to government agencies, major corporations, and academic institutions.
Discovery and Initial Findings
In February 2025, Infoblox researchers identified Hazy Hawk’s activities when the group successfully hijacked subdomains belonging to the U.S. Centers for Disease Control and Prevention (CDC). Subsequent investigations revealed that Hazy Hawk had targeted numerous domains associated with global government entities, Fortune 500 companies, and prestigious universities.
Exploitation of DNS Misconfigurations
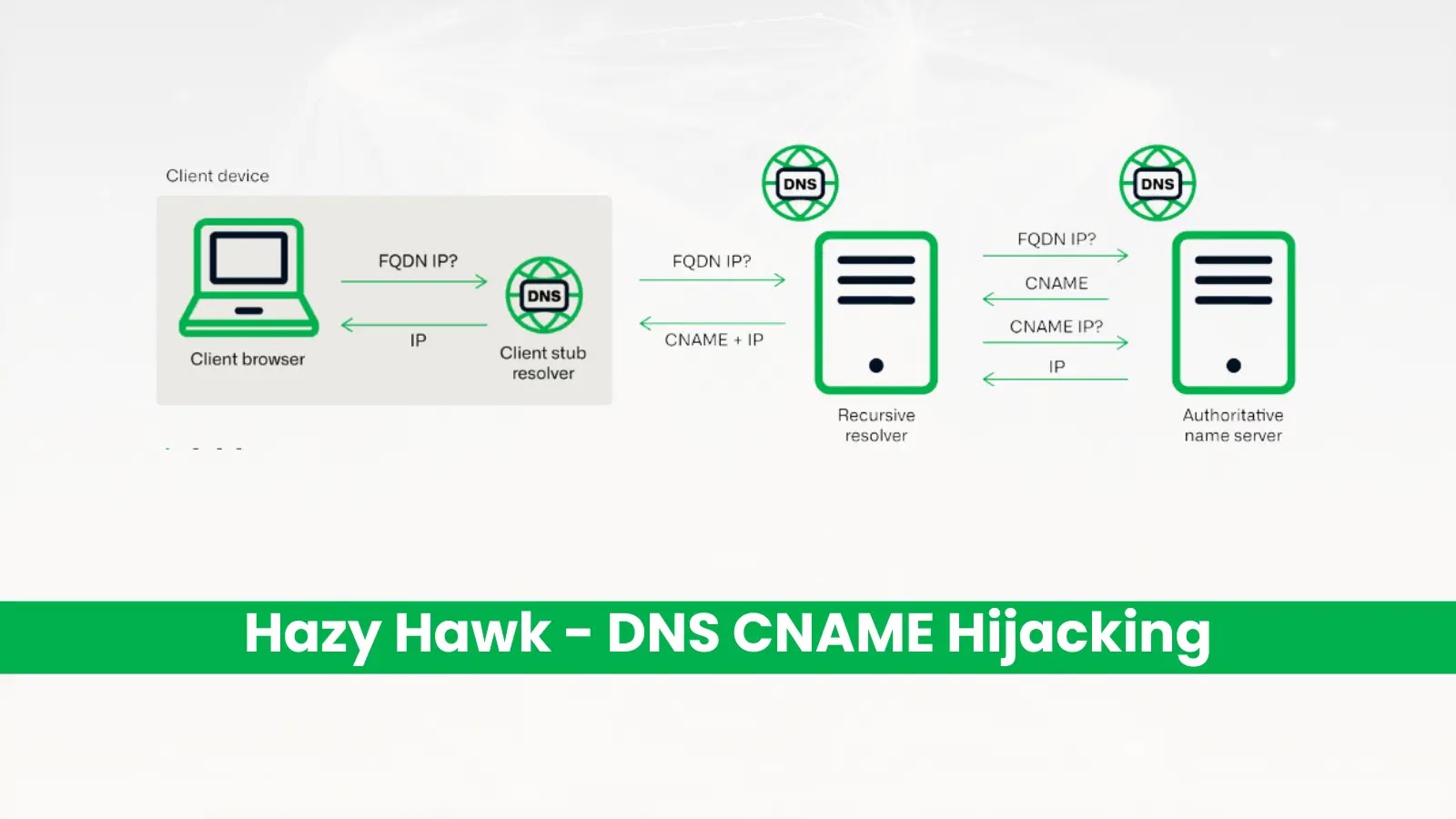
Hazy Hawk employs a technique known as CNAME hijacking, which exploits dangling DNS records pointing to cloud resources that are no longer in use. When organizations decommission cloud services without removing the corresponding DNS entries, attackers can register identical resources and gain control of the subdomain without breaching any systems. This method allows Hazy Hawk to host malicious URLs under trusted domains, increasing the likelihood of successful phishing and malware distribution.
Notable Victims and Impact
The group’s targets include federal agencies such as cdc[.]gov and alabama[.]gov, universities like Berkeley[.]edu and nyu[.]edu, and global corporations including Deloitte, PricewaterhouseCoopers, and Ernst & Young. Even international organizations like UNICEF have been affected. By hijacking these subdomains, Hazy Hawk generates hundreds of malicious URLs that appear legitimate in search results due to the parent domain’s high trust score. Unsuspecting users clicking these links are redirected through complex traffic distribution systems designed to profile them based on factors like device type and location.
Technical Sophistication and Deceptive Techniques
Hazy Hawk demonstrates a high level of technical sophistication. Identifying vulnerable DNS records in the cloud is significantly more challenging than identifying regular unregistered domains. As cloud usage has grown, the number of abandoned fire and forget resources has skyrocketed. Once in control of a subdomain, Hazy Hawk employs several deceptive techniques, including stealing content from legitimate websites like PBS to make their initial pages appear trustworthy. They also use URL obfuscation to hide link destinations, sometimes specifically altering AWS S3 bucket URLs to thwart security measures.
Persistent Threats and Financial Impact
Users who interact with these malicious sites may unknowingly grant permission for push notifications, creating a persistent channel for scammers to send alerts even after leaving the initial site. These notifications often impersonate legitimate brands and claim the user’s device has been compromised, leading to tech support scams and fake antivirus offers. The financial impact is substantial, particularly among elderly victims. The FBI reports that tech support scams, one of Hazy Hawk’s primary deceptions, resulted in losses exceeding $347 million in 2021 alone.
Mitigation Strategies
To defend against such attacks, organizations must implement robust DNS hygiene practices. Regular audits of DNS records are essential to identify and remove entries pointing to decommissioned cloud resources. Additionally, organizations should monitor for unauthorized changes to DNS configurations and employ security measures to detect and block malicious activities associated with their domains.
Conclusion
Hazy Hawk’s exploitation of DNS misconfigurations underscores the critical importance of diligent DNS management and cloud resource monitoring. By addressing these vulnerabilities, organizations can significantly reduce the risk of subdomain hijacking and protect their users from associated scams and malware.