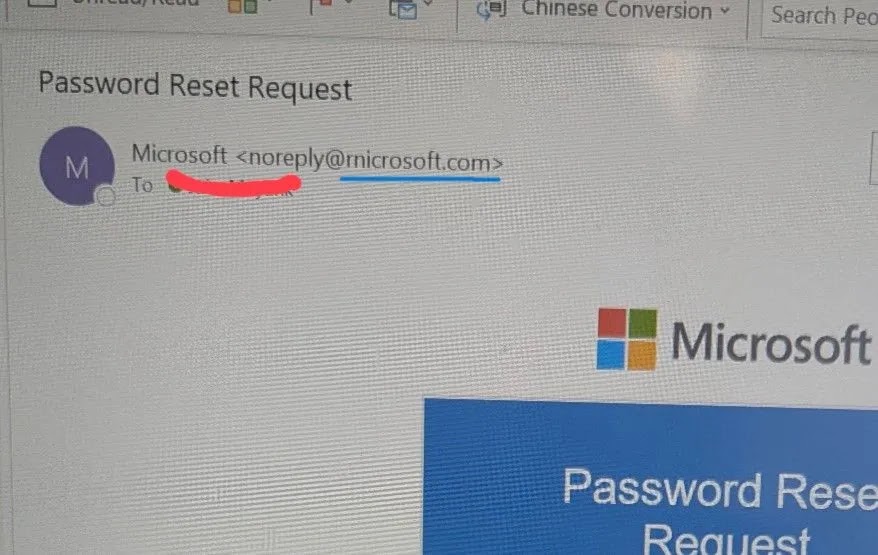
Cybercriminals Exploit Typographical Deception to Mimic Microsoft Domains and Steal Credentials
In a sophisticated phishing campaign, cybercriminals are employing a subtle typographical trick to deceive users into divulging sensitive login credentials. By substituting the letter ‘m’ in microsoft.com with the combination of ‘r’ and ‘n’, they create a counterfeit domain—rnicrosoft.com—that closely resembles the legitimate Microsoft website. This technique, known as typosquatting, exploits the nuances of font rendering in modern email clients and web browsers, where the ‘r’ and ‘n’ characters placed together can visually mimic an ‘m’.
The effectiveness of this deception lies in its subtlety. On high-resolution desktop monitors, the difference might be discernible to a vigilant observer. However, the human brain’s tendency to autocorrect minor anomalies often masks the discrepancy. The threat becomes even more pronounced on mobile devices, where limited screen space and truncated address bars make it challenging to detect such manipulations. Attackers exploit these factors by registering look-alike domains to facilitate credential phishing, vendor invoice scams, and internal HR impersonation campaigns.
Once a user is convinced that an email originates from a trusted source, they are more likely to click on malicious links or download harmful attachments. The rn substitution is just one of several variations employed by attackers. Other common tactics include replacing the letter ‘o’ with the number ‘0’ or adding hyphens to legitimate brand names to create a false sense of authenticity.
Common Typosquatting Variations:
| Technique | Visual Example | Deception Method |
|———————–|—————————-|—————————————————|
| Letter Combination | rnicrosoft.com | Uses ‘r’ and ‘n’ to mimic ‘m’. |
| Number Swapping | micros0ft.com | Replaces the letter ‘o’ with the number ‘0’. |
| Hyphenation | microsoft-support.com | Adds legitimate-sounding subdomains or suffixes. |
| TLD Switching | microsoft.co | Uses a different Top Level Domain (dropping the ‘m’). |
Defending against these homoglyph and typosquatting attacks requires a proactive approach:
1. Verify Sender Addresses: Always expand the full sender address before interacting with any unsolicited email.
2. Inspect Hyperlinks: Hover over hyperlinks to reveal the actual destination URL. On mobile devices, long-press the link to expose the true URL before clicking.
3. Analyze Email Headers: Examine email headers, specifically the Reply-To field, to determine if responses are being routed to an external, unauthorized inbox.
4. Direct Navigation: For unexpected password reset requests or account notifications, avoid clicking on email links. Instead, navigate directly to the official service by typing the URL into your browser.
5. Educate and Train: Organizations should conduct regular training sessions to help employees recognize and respond appropriately to phishing attempts.
By adopting these practices, individuals and organizations can enhance their defenses against deceptive phishing tactics that exploit typographical similarities to impersonate trusted entities.