Cybercriminals have orchestrated a sophisticated malware campaign by creating a counterfeit Bitdefender antivirus website to distribute a trio of malicious programs aimed at stealing financial data and maintaining persistent access to victims’ computers. This operation, identified by DomainTools Intelligence (DTI), targets users’ cryptocurrency wallets, banking credentials, and personal information.
Deceptive Website and Malware Distribution
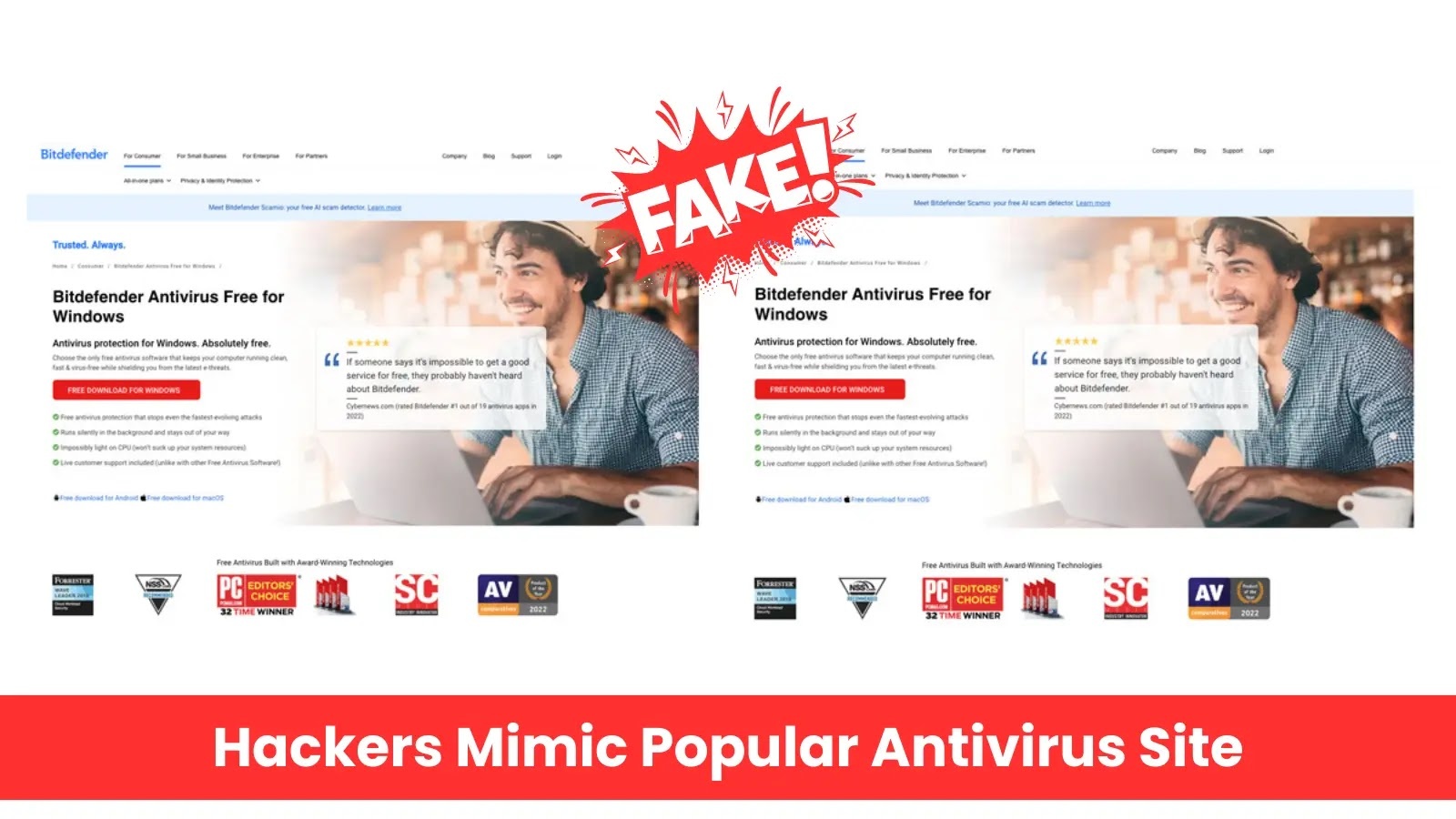
The fraudulent domain, bitdefender-download[.]co, closely resembles the legitimate Bitdefender antivirus download page, making it challenging for users to discern its authenticity. Upon clicking the Download For Windows button, visitors inadvertently download a ZIP file containing three distinct malware strains: VenomRAT, StormKitty, and SilentTrinity.
Multi-Stage Attack Strategy
The attack initiates with a file hosted on Bitbucket that redirects to Amazon S3 storage, lending an air of legitimacy to the download process. The bundled executable, disguised as StoreInstaller.exe, contains configurations for all three malware families, each serving a specific role in the cybercriminals’ operation.
– VenomRAT: This remote access tool provides attackers with initial and ongoing access to victim machines. It can steal files, cryptocurrency wallets, browser data including credit card details, and perform keylogging activities.
– StormKitty: Functions as a rapid credential harvester, quickly gathering sensitive information from the infected system.
– SilentTrinity: An open-source post-exploitation framework that ensures stealthy long-term access for potential repeat compromises or selling access to other criminals.
Targeting Financial Data
The malware specifically targets financial data, with VenomRAT capable of stealing cryptocurrency wallets and browser-stored banking information. Recent analysis shows that newer versions of VenomRAT have expanded their capabilities to include credit card information theft.
Coordinated Phishing Operation
DTI discovered that the fake Bitdefender site shares infrastructure with other malicious domains impersonating banks and IT services, suggesting a coordinated phishing operation. The campaign includes fraudulent sites that spoof the Armenian IDBank and Royal Bank of Canada online banking portals.
Protection Recommendations
Bitdefender has acknowledged the threat, stating they are working to have the fraudulent site taken offline and that their security software detects the malicious files. Google Chrome now flags the fake download link as malicious, preventing users from accessing it.
Security experts recommend exercising extreme caution when downloading software, verifying website authenticity, and avoiding suspicious links or email attachments. Users should only download antivirus software from official vendor websites and be wary of unsolicited security alerts or download prompts.