A sophisticated cyberattack technique known as LNK Stomping has emerged as a significant threat to Windows security. This method exploits inherent flaws in how the operating system processes shortcut files, enabling attackers to circumvent critical security features and execute malicious code without triggering alerts.
Understanding LNK Stomping
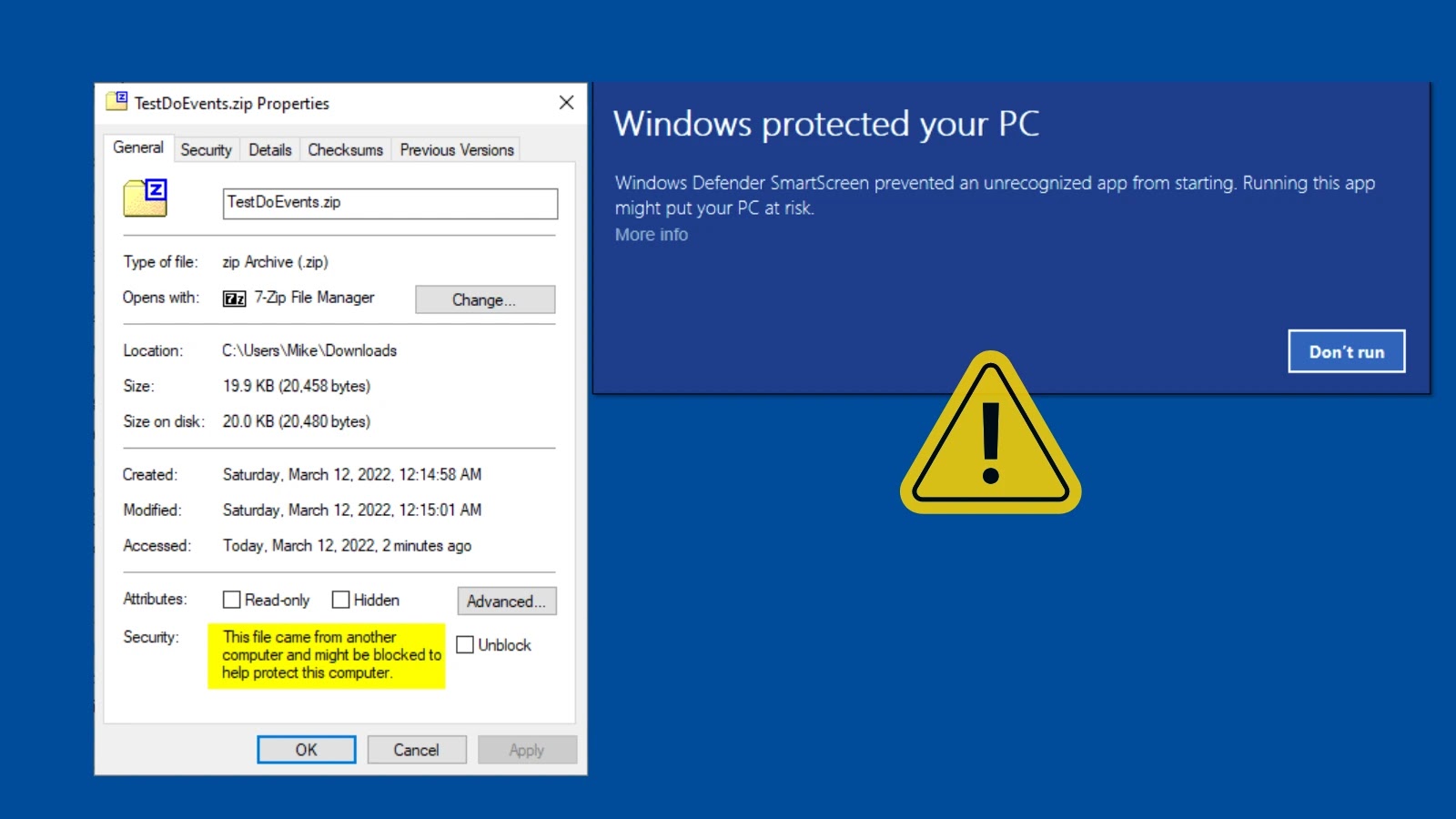
LNK Stomping involves the manipulation of Windows shortcut files (.lnk) to bypass the Mark of the Web (MoTW) security feature. MoTW is designed to flag files downloaded from the internet, prompting security warnings when users attempt to open potentially unsafe content. By exploiting this vulnerability, attackers can execute malicious payloads while evading detection from security components like Smart App Control (SAC) and SmartScreen.
Technical Exploitation Details
The attack leverages the complex binary structure of LNK files, specifically targeting the LinkTarget IDList component. This section contains Shell Item IDs that define the hierarchical location of target files within the Windows Shell namespace. By creating non-standard path configurations, attackers trigger Windows Explorer’s path normalization process, which inadvertently removes the MoTW metadata from the malicious files.
When a user clicks on a maliciously crafted LNK file with abnormal path structures, Windows Explorer detects the irregular configuration and attempts to normalize it. During this process, the system overwrites the original LNK file, unintentionally stripping away the NTFS Alternate Data Stream (ADS) known as Zone.Identifier, which contains the MoTW metadata. This removal occurs before any security checks are performed, allowing the malicious payload to execute without triggering defensive mechanisms.
Identified Manipulation Techniques
Researchers have identified three primary manipulation techniques used in LNK Stomping attacks:
1. PathSegment Type Attacks: These involve placing entire file paths within a single IDList array element instead of properly segmenting them.
2. Dot Type Attacks: These append periods or spaces to execution target paths, creating structural inconsistencies.
3. Relative Type Attacks: These use only filenames without complete path specifications, leading to normalization vulnerabilities.
Historical Context and Detection Challenges
Security researchers have discovered numerous LNK Stomping samples dating back six years, indicating that this technique has been exploited in the wild long before its formal disclosure. The effectiveness of this method lies in its ability to mimic legitimate system behavior. When LNK files execute, they invoke trusted Windows utilities, making malicious activities blend seamlessly with normal system operations.
The Cybersecurity and Infrastructure Security Agency (CISA) has added CVE-2024-38217 to its Known Exploited Vulnerabilities (KEV) catalog, confirming active exploitation by threat actors. This approach has gained popularity following Microsoft’s macro-blocking policies implemented in 2022, which forced attackers to seek alternative initial access vectors through file formats like ISO, RAR, and LNK files distributed via email attachments or compressed archives.
Organizations face significant detection challenges because this attack exploits fundamental Windows file handling mechanisms rather than external vulnerabilities. Traditional signature-based detection methods may fail to identify these attacks since they leverage legitimate system processes and file structures. The persistence of this vulnerability for years before discovery underscores the importance of format-level security research and behavior-based analysis to identify previously unknown evasion techniques in familiar file types.
Broader Implications and Related Threats
The exploitation of LNK files is not isolated to LNK Stomping. Other sophisticated attack vectors have emerged, leveraging similar techniques to bypass security measures:
– FileFix 2.0 Attack: This method exploits how Chrome and Microsoft Edge handle webpage saving functionality. By saving HTML pages with specific MIME types, attackers can create files without MoTW protection. Users are tricked into saving these files as .hta (HTML Application) files, which can execute malicious scripts without warnings. Social engineering tactics, such as fake backup code pages, prompt users to save and open these dangerous files. Blocking or removing mshta.exe can prevent these .hta files from running and mitigate the attack.
– WinZip MoTW Bypass Vulnerability (CVE-2025-33028): A critical flaw in WinZip allows attackers to bypass Windows’ MoTW security feature. When extracting files from internet-downloaded ZIP archives, WinZip fails to propagate the MoTW tag to the extracted files. This oversight enables malicious code to execute without warning on victims’ computers.
– 7-Zip MoTW Bypass Vulnerability (CVE-2025-0411): A high-severity vulnerability in 7-Zip allows attackers to bypass the MoTW security mechanism. When users extract files from crafted archives carrying the MoTW flag, the extracted files fail to retain the MoTW designation. This flaw effectively disables critical security warnings and protections, potentially enabling the execution of arbitrary code.
– Coyote Banking Malware: This malware targets financial institutions by employing malicious LNK files as an entry point to execute PowerShell scripts. The attack begins with a malicious LNK file that executes a stealthy PowerShell command, connecting to a remote server to download additional payloads. This multi-stage infection chain ends in data theft and system compromise.
– XDSpy Threat Actors: The XDSpy group has exploited a zero-day vulnerability in Windows shortcut files to attack Windows system users. By hiding executed commands from the Windows user interface in specially crafted LNK files, they can execute hidden commands when triggered. This campaign primarily targets government entities in Eastern Europe and Russia.
– Weaponized PDF and LNK Files: Attackers have combined seemingly innocuous PDF newsletters with malicious LNK files to infiltrate enterprise environments. Victims receive an archive containing both a PDF decoy and a companion .lnk file masquerading as the newsletter. When the shortcut is executed, a multi-stage PowerShell loader embedded within the LNK unpacks and deploys additional payloads entirely in memory, evading disk-based detection.
– Windows SmartScreen Vulnerability (CVE-2024-21412): A critical security bypass vulnerability in Windows SmartScreen allows remote attackers to bypass security warnings and deliver malicious payloads. Cybercriminals, including groups like Water Hydra, Lumma Stealer, and Meduza Stealer, have exploited this vulnerability to conduct widespread attacks.
– DarkSamural APT Group: This group has targeted critical infrastructure and government entities across South Asia by leveraging malicious LNK and PDF files to steal critical data. The attack chain involves deceptively crafted LNK and PDF files to infiltrate networks, establish persistence, and exfiltrate sensitive information.
– Sidewinder Hacker Group: Also known as APT-C-24, this group has evolved its attack methodology by deploying sophisticated LNK file-based phishing campaigns targeting various sectors across South Asia. By disguising malicious MSC files with familiar PDF icons, they entice recipients to inadvertently launch embedded scripts, leading to unauthorized file transfers and credential theft.
Mitigation Strategies
To defend against LNK Stomping and related attacks, organizations should consider the following measures:
1. Patch Systems Promptly: Ensure that all systems are updated with the latest security patches to address known vulnerabilities like CVE-2024-38217.
2. Enhance User Awareness: Educate users about the risks associated with opening files from untrusted sources, especially those with double extensions or unfamiliar formats.
3. Implement Advanced Detection Mechanisms: Deploy behavior-based detection systems capable of identifying anomalies in file execution and system processes.
4. Restrict Execution of Untrusted LNK Files: Configure security policies to limit the execution of LNK files from untrusted locations.
5. Monitor System Behavior: Regularly monitor system logs and network traffic for signs of unusual activity that may indicate exploitation attempts.
By adopting a comprehensive security posture that includes timely patching, user education, and advanced detection capabilities, organizations can better protect themselves against LNK Stomping and similar sophisticated attack techniques.