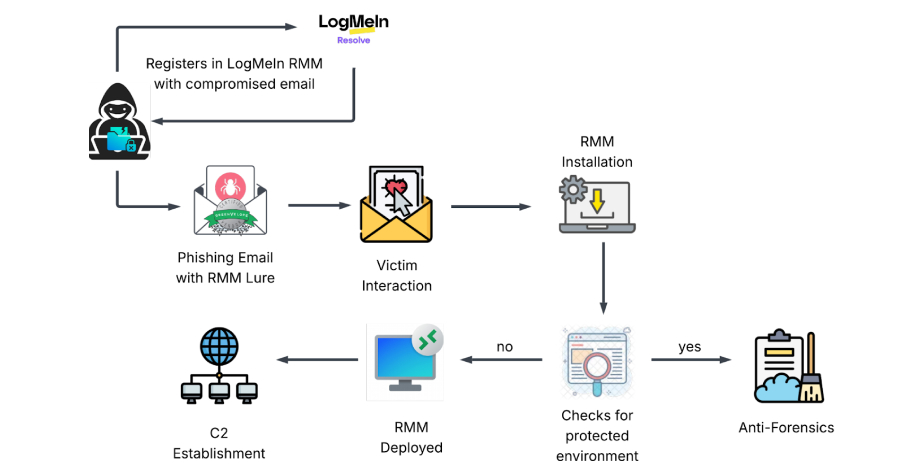
In August 2025, cybersecurity experts identified a sophisticated cyberattack exploiting Microsoft Edge’s Internet Explorer (IE) mode. This attack leverages the compatibility feature designed to support legacy web applications, exposing users to significant security risks.
Understanding the Attack Mechanism
Cybercriminals initiate the attack by directing users to meticulously crafted, deceptive websites that mimic legitimate ones. Upon visiting these sites, users encounter a prompt urging them to reload the page in Internet Explorer mode. This transition shifts the browsing environment from Edge’s secure Chromium-based framework to the less secure legacy IE framework.
The crux of the vulnerability lies in Internet Explorer’s Chakra JavaScript engine. Despite Microsoft’s efforts to enhance its security, the Chakra engine remains susceptible to memory corruption exploits. Once users switch to IE mode, attackers deploy zero-day exploits targeting this engine, enabling remote code execution within the browser context.
Escalation to Full System Compromise
After achieving code execution within the browser, attackers employ additional exploits to escalate privileges. This escalation allows them to break free from the browser’s sandbox environment, gaining elevated system privileges. Consequently, attackers can install malware, move laterally within corporate networks, and exfiltrate sensitive data.
Microsoft’s Response and Mitigation Measures
Upon detecting these exploitation campaigns, Microsoft took decisive action to mitigate the threat. The company restricted access to IE mode by removing high-risk entry points, such as toolbar buttons and context menus. However, enterprise policy support for legitimate business needs remains intact.
Recommendations for Users and Organizations
To safeguard against such attacks, users and organizations should:
– Limit Use of IE Mode: Only utilize Internet Explorer mode when absolutely necessary for compatibility with legacy applications.
– Regularly Update Software: Ensure that all software, including browsers and operating systems, are up-to-date with the latest security patches.
– Enhance User Awareness: Educate users about the risks associated with social engineering tactics and the importance of verifying the authenticity of websites.
– Implement Robust Security Measures: Deploy comprehensive security solutions that can detect and prevent exploitation attempts.
Conclusion
The exploitation of Microsoft Edge’s Internet Explorer mode underscores the persistent threats posed by legacy technologies. As cybercriminals continue to adapt and find new attack vectors, it is imperative for users and organizations to remain vigilant, adopt proactive security measures, and stay informed about emerging threats.