Cybercriminals Exploit Cisco IOS XE Vulnerability to Deploy BADCANDY Web Shell
In recent developments, both cybercriminals and state-sponsored entities have intensified their attacks on unpatched Cisco IOS XE devices, particularly in Australia. These adversaries are deploying a persistent, Lua-based web shell known as BADCANDY to maintain unauthorized access to compromised systems.
Understanding the BADCANDY Web Shell
BADCANDY is a lightweight implant that enables attackers to execute commands with root-level privileges on affected devices. It operates by creating a hidden Uniform Resource Identifier (URI) path within an Nginx configuration file named `cisco_service.conf`. This covert pathway allows malicious actors to issue commands remotely, effectively granting them full control over the compromised system.
The implant was first identified in October 2023 and has since been observed in various forms throughout 2024 and into 2025. Its primary method of deployment involves exploiting a critical vulnerability in the Cisco IOS XE software’s web user interface, specifically the CVE-2023-20198 flaw.
The CVE-2023-20198 Vulnerability
CVE-2023-20198 is a severe security flaw that allows remote, unauthenticated attackers to create highly privileged accounts on affected Cisco IOS XE routers and switches. By exploiting this vulnerability, attackers can gain full system control without the need for valid credentials. Cisco addressed this zero-day vulnerability in October 2023; however, public exploits emerged shortly thereafter, leading to widespread abuse by various threat groups, including the Chinese state-sponsored group known as SALT TYPHOON.
The Scope of the Threat
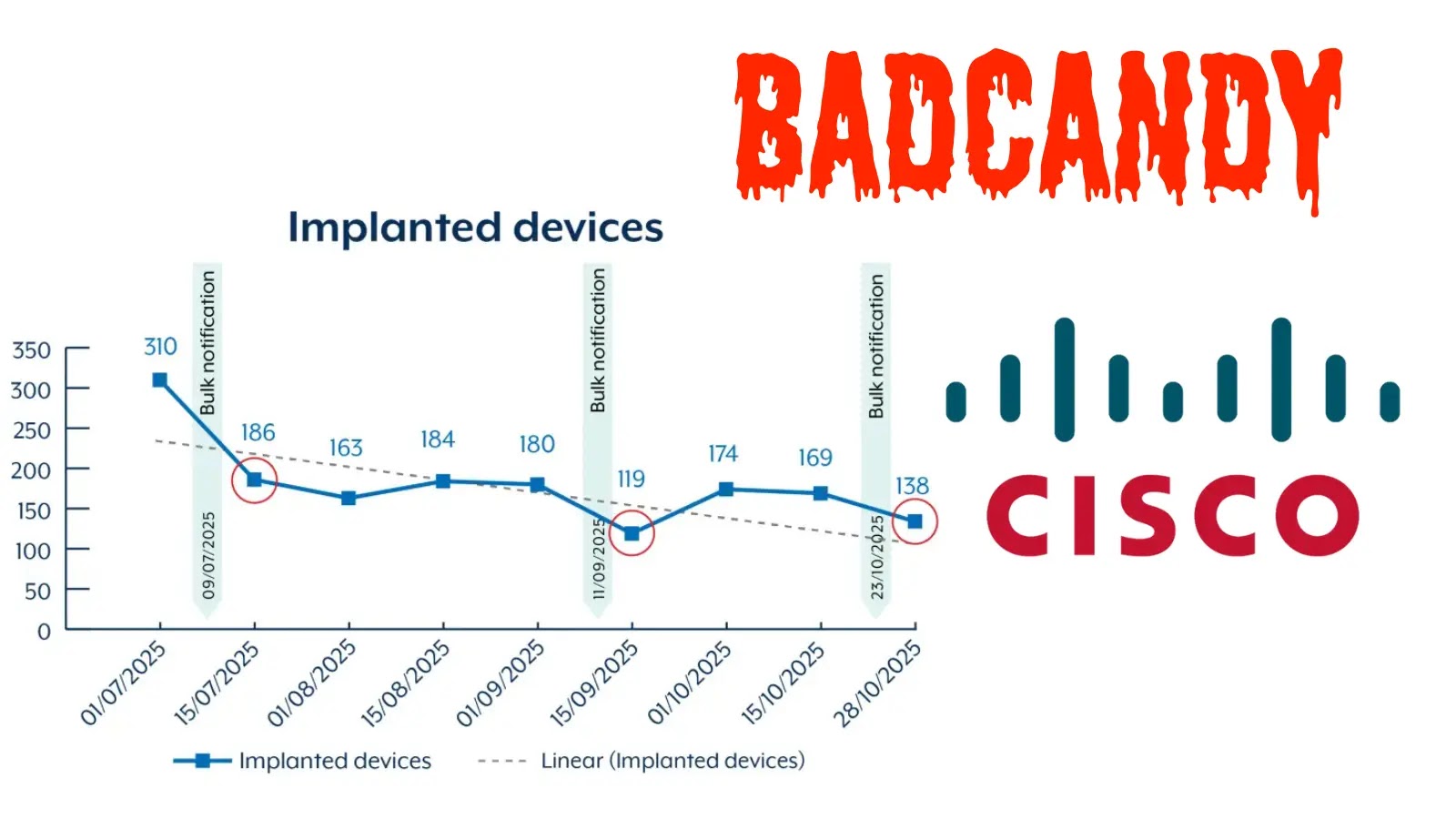
The Australian Signals Directorate (ASD) has reported that over 400 devices were potentially compromised since July 2025, with more than 150 still infected as of late October. This ongoing threat underscores the critical need for organizations to secure their network infrastructure against such vulnerabilities.
Attackers’ Tactics and Persistence
After successfully compromising a device, attackers often apply a non-persistent patch to conceal the vulnerability, while simultaneously installing the BADCANDY implant. Although BADCANDY is removed upon a system reboot, attackers can maintain access through stolen credentials or other persistence mechanisms. This persistence makes re-exploitation relatively straightforward, especially on devices with exposed web interfaces.
The CVE-2023-20198 vulnerability was among the most routinely exploited flaws in 2023, and ASD confirms that attacks have continued into 2025, particularly targeting internet-facing devices. Groups like SALT TYPHOON have leveraged similar Cisco vulnerabilities in global telecommunications breaches, often using legitimate credentials alongside exploits like CVE-2023-20198 and CVE-2023-20273.
Additionally, other criminal actors and nation-states have been observed reusing BADCANDY, scanning for unpatched systems, and re-infecting devices that had previously been cleared. The implant’s minimal footprint makes detection challenging without thorough configuration reviews, highlighting the risks to edge networks worldwide.
ASD’s Response and Recommendations
In response to this escalating threat, ASD has issued bulk notifications to affected entities through service providers, urging immediate patching, system reboots, and comprehensive incident response measures since July 2025. These efforts have reduced the number of infections from over 400 to approximately 150 by late October. However, fluctuations in infection rates suggest that attackers are detecting and re-exploiting devices that have been cleared.
ASD attributes these resurgences to unpatched systems remaining online, emphasizing that reboots alone are insufficient without addressing the underlying vulnerability.
To mitigate the risk of exploitation, ASD recommends the following actions:
1. Review Running Configurations: Examine configurations for privilege level 15 accounts, especially those with suspicious names like cisco_tac_admin or random strings, and remove any unauthorized entries.
2. Scan for Unknown Tunnel Interfaces: Identify and investigate any unexpected tunnel interfaces, such as interface tunnel[number] with unfamiliar IP addresses.
3. Monitor TACACS+ Logs: If TACACS+ is enabled, review logs for any unauthorized changes or activities.
4. Apply Cisco’s Patch: Implement the security patch provided by Cisco for CVE-2023-20198 to address the vulnerability.
5. Disable HTTP Server Feature: Turn off the HTTP server feature to reduce the attack surface.
6. Follow IOS XE Hardening Guide: Adhere to Cisco’s IOS XE hardening guidelines to restrict web user interface access and enhance overall security.
7. Post-Reboot Checks: After rebooting the system to remove the implant, conduct thorough checks for any lingering unauthorized changes.
8. Implement Network Segmentation: Apply broader edge-device security measures, such as network segmentation, to prevent lateral movement by attackers.
Cisco has provided indicators of compromise in its advisory to assist organizations in identifying and mitigating potential threats. ASD continues to issue notifications to reduce the attack surface in Australia. By prioritizing these actions, organizations can thwart re-exploitation attempts and strengthen their defenses against evolving cyber threats.