Google’s Threat Intelligence Group (GTIG) has recently identified and detailed the operations of a financially motivated cybercriminal group, designated as UNC6040. This group specializes in voice phishing, commonly known as vishing, to infiltrate organizations’ Salesforce platforms, leading to extensive data breaches and subsequent extortion attempts.
Modus Operandi of UNC6040
UNC6040 employs sophisticated social engineering tactics, primarily through telephone-based impersonation of IT support personnel. By engaging English-speaking employees in convincing conversations, these attackers manipulate their targets into divulging sensitive information or performing actions that compromise organizational security. This method has proven effective in deceiving employees into granting unauthorized access to critical systems.
Exploitation of Salesforce’s Data Loader
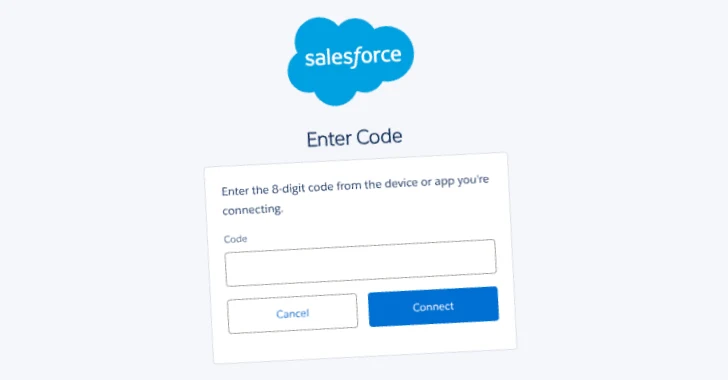
A notable aspect of UNC6040’s strategy involves the misuse of Salesforce’s Data Loader application. Data Loader is a legitimate tool designed for bulk data import, export, and updates within the Salesforce environment. The attackers have modified this application, rebranding it with names such as My Ticket Portal, to deceive users into authorizing its connection to their organization’s Salesforce portal. Once authorized, this malicious application provides the attackers with unauthorized access, enabling them to exfiltrate vast amounts of sensitive data.
Lateral Movement and Broader Implications
Beyond the initial data theft from Salesforce, UNC6040 demonstrates the capability to move laterally within compromised networks. This lateral movement allows them to access and harvest information from other critical platforms, including Okta, Workplace, and Microsoft 365. Such extensive access amplifies the potential damage, exposing organizations to broader security risks and data breaches.
Delayed Extortion Tactics
In several instances, UNC6040 has engaged in extortion activities, often several months after the initial breach. This delay suggests a calculated approach to monetizing stolen data, possibly in collaboration with other threat actors. During these extortion attempts, the group has claimed affiliation with the notorious hacking collective ShinyHunters, likely to exert additional pressure on their victims.
Connections to The Com and Scattered Spider
UNC6040’s operations exhibit overlaps with groups linked to The Com, an online cybercrime collective. Similarities include targeting Okta credentials and employing social engineering tactics via IT support impersonation. These methods are also characteristic of Scattered Spider, another financially motivated threat actor associated with The Com. However, while Scattered Spider focuses on account takeovers for broad network access, UNC6040’s primary objective is the targeted theft of Salesforce data, highlighting the diverse risks posed by vishing campaigns.
Utilization of Automated Phone Systems
UNC6040 leverages automated phone systems featuring pre-recorded messages and interactive menus to gather information about their targets. These systems enable attackers to anonymously identify common issues faced by end users, internal application names, additional support team contact numbers, and, in some cases, alerts about company-wide technical issues. This information aids in crafting more convincing social engineering attacks.
Mitigation Strategies
To defend against such sophisticated vishing attacks, organizations should implement comprehensive security measures, including:
– Employee Training: Regularly educate staff on recognizing and responding to social engineering attempts.
– Multi-Factor Authentication (MFA): Enforce MFA across all critical systems to add an extra layer of security.
– Access Controls: Limit user permissions to only what is necessary for their roles, reducing the potential impact of compromised accounts.
– Monitoring and Logging: Implement robust monitoring to detect unusual activities and maintain logs for forensic analysis.
– Incident Response Plan: Develop and regularly update an incident response plan to swiftly address security breaches.
By adopting these strategies, organizations can enhance their resilience against vishing attacks and protect their sensitive data from malicious actors like UNC6040.