Google Unveils AI-Powered Alert Triage and Investigation Agent to Revolutionize Security Operations
In a significant advancement for cybersecurity, Google has announced the public preview of its Alert Triage and Investigation Agent, an AI-driven tool designed to enhance the efficiency and effectiveness of security operations centers (SOCs). This innovative agent is now integrated directly into Google Security Operations, offering security teams a powerful resource to process alerts more swiftly and accurately.
Pioneering the Agentic SOC
The introduction of this intelligent agent marks a pivotal step toward realizing Google’s vision of an Agentic SOC—a security operations center augmented by intelligent automation. Traditionally, security analysts are tasked with manually reviewing each alert, a process that can be both time-consuming and prone to human error. Google’s new agent automates this process by independently assessing alerts, gathering pertinent information, and determining their legitimacy. This automation allows security teams to concentrate their efforts on alerts that genuinely necessitate human intervention.
Proven Impact Across Industries
During its private preview phase, the agent was deployed to investigate hundreds of thousands of alerts across diverse organizations and industries. Feedback from sectors such as financial services and major retail indicated substantial time savings. Analysts reported that the agent’s comprehensive investigation summaries facilitated quicker decision-making by consolidating complex information that would otherwise require extensive manual queries and analysis.
Operational Mechanics of the Agent
The agent’s investigation process is initiated when alerts are generated within Google’s detection engine. Upon receiving an alert, the agent formulates a dynamic investigation plan aligned with best practices established by Mandiant experts. It then executes a series of analytical tasks, including:
– YARA-L Searches: To retrieve relevant events and identify potential threats.
– Threat Intelligence Enrichment: Utilizing Google Threat Intelligence to provide context and depth to the analysis.
– Command-Line Analysis: Decoding or deobfuscating commands to uncover malicious activities.
– Process Tree Reconstruction: Mapping out the sequence of processes to understand the full scope of potential attacks.
Upon completing its investigation, the agent determines the validity of the alert and assigns a confidence score, indicating the level of certainty in its assessment.
Emphasis on Transparency and Continuous Improvement
Google places a strong emphasis on the explainability of the agent’s processes. The system references its sources and outlines each step of the investigation, ensuring that analysts can comprehend how conclusions were reached. To maintain accuracy and foster continuous improvement, Google employs multiple evaluation techniques, including comparisons with human expert assessments and advanced AI evaluation methods.
Availability and Future Enhancements
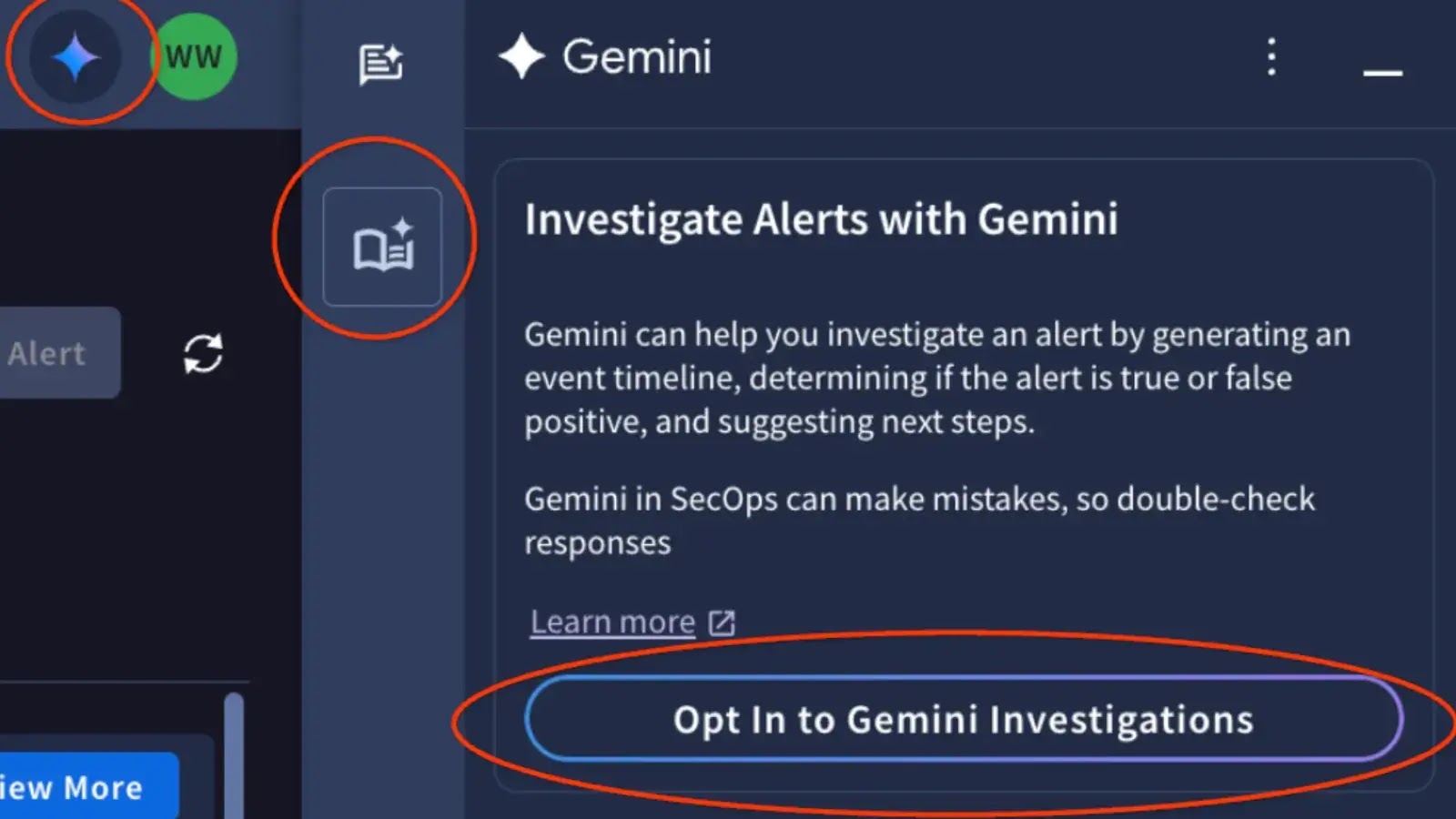
All eligible users of Google Security Operations Enterprise and Enterprise Plus can opt into the public preview immediately by clicking the Gemini icon within Google Security Operations. Once enrolled, investigations commence automatically, though users also have the option to trigger investigations manually. Google plans to transition the agent to general availability in 2026, with additional enhancements aimed at deepening investigation capabilities and further integrating with existing workflows.