GoBruteforcer Botnet Exploits Weak Credentials to Target Cryptocurrency Databases
A recent surge in cyberattacks has been attributed to GoBruteforcer, a sophisticated botnet that infiltrates databases associated with cryptocurrency and blockchain projects. By exploiting weak credentials, this malware gains unauthorized access to services such as FTP, MySQL, PostgreSQL, and phpMyAdmin on Linux servers, thereby expanding its network and enhancing its capabilities.
Evolution of GoBruteforcer
Initially identified in March 2023 by Palo Alto Networks Unit 42, GoBruteforcer, also known as GoBrut, was observed targeting Unix-like systems across various architectures, including x86, x64, and ARM. The malware deployed Internet Relay Chat (IRC) bots and web shells for remote access, utilizing brute-force modules to scan and compromise vulnerable systems, thereby enlarging its botnet.
By mid-2025, Check Point Research detected a more advanced iteration of this Golang-based malware. This version featured a heavily obfuscated IRC bot rewritten in Golang, improved persistence mechanisms, process-masking techniques, and dynamic credential lists. These enhancements significantly bolstered the malware’s ability to evade detection and maintain control over compromised systems.
Mechanisms of Attack
GoBruteforcer’s recent campaigns are driven by two primary factors:
1. Mass Reuse of AI-Generated Deployment Examples: The widespread use of AI-generated server deployment scripts has led to the propagation of common usernames and weak default credentials. These scripts often include default usernames and passwords that are easily exploitable.
2. Persistence of Legacy Web Stacks: Older web stacks, such as XAMPP, often expose FTP and administrative interfaces with minimal security hardening, making them prime targets for attackers.
The malware employs a combination of common usernames and passwords, such as myuser:Abcd@123 or appeaser:admin123456, to gain remote access. These credentials are frequently found in database tutorials and vendor documentation, which have been used to train large language models (LLMs). Consequently, LLMs may generate code snippets with these default usernames, inadvertently facilitating attacks.
Notably, some usernames are tailored to target cryptocurrency-related services (e.g., cryptouser, appcrypto, crypto_app, and crypto) or phpMyAdmin panels (e.g., root, wordpress, and wpuser). Attackers maintain a small, stable password pool for each campaign, refreshing per-task lists from that pool and rotating usernames and niche additions several times a week to pursue different targets. For FTP brute-force attacks, a small, hardcoded set of credentials is embedded in the bruteforcer binary, pointing to web-hosting stacks and default service accounts.
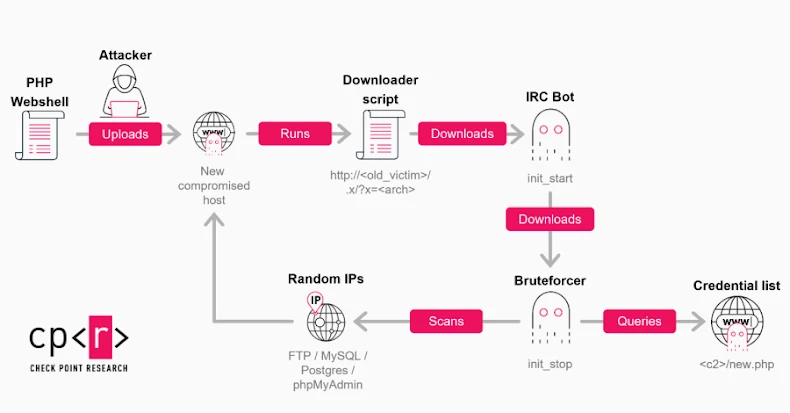
Infection Process
In observed instances, GoBruteforcer exploits internet-exposed FTP services on servers running XAMPP as an initial access vector. The malware uploads a PHP web shell, which then downloads and executes an updated version of the IRC bot using a shell script tailored to the system’s architecture. Once a host is successfully infected, it can serve multiple purposes:
– Brute-Force Component: The infected host attempts password logins for FTP, MySQL, PostgreSQL, and phpMyAdmin services across the internet, seeking to compromise additional systems.
– Payload Hosting: The compromised system can host and serve malicious payloads to other infected machines, facilitating further spread of the malware.
– Command-and-Control (C2) Operations: The infected host may function as an IRC-style control endpoint or act as a backup C2 server, enhancing the botnet’s resilience.
Targeting Cryptocurrency Projects
Further analysis revealed that one of the compromised hosts was used to stage a module that iterates through a list of TRON blockchain addresses. By querying balances using the tronscanapi[.]com service, the attackers identified accounts with non-zero funds, indicating a concerted effort to target blockchain projects.
Broader Implications
GoBruteforcer exemplifies a persistent cybersecurity challenge: the combination of exposed infrastructure, weak credentials, and increasingly automated tools. While the botnet itself is technically straightforward, its operators benefit from the vast number of misconfigured services that remain online.
The disclosure of these activities coincides with reports from GreyNoise, which revealed that threat actors are systematically scanning the internet for misconfigured proxy servers that could provide access to commercial LLM services. Between October 2025 and January 2026, campaigns have leveraged server-side request forgery (SSRF) vulnerabilities to target functionalities such as Ollama’s model pull and Twilio SMS webhook integrations. These activities underscore the importance of securing AI and machine learning services against potential exploitation.
Mitigation Strategies
To defend against threats like GoBruteforcer, organizations should implement the following measures:
– Enforce Strong Credentials: Replace default usernames and passwords with complex, unique credentials to reduce the risk of brute-force attacks.
– Regularly Update and Patch Systems: Keep all software, including web stacks like XAMPP, up to date with the latest security patches to mitigate known vulnerabilities.
– Limit Exposure of Services: Restrict internet exposure of critical services such as FTP, MySQL, PostgreSQL, and phpMyAdmin. Implement firewall rules and access controls to limit access to trusted IP addresses.
– Monitor for Anomalous Activity: Continuously monitor server logs and network traffic for signs of unauthorized access or unusual behavior, such as multiple failed login attempts or unexpected data transfers.
– Implement Multi-Factor Authentication (MFA): Enhance security by requiring multiple forms of verification for access to sensitive systems and services.
– Educate and Train Staff: Provide regular training to staff on cybersecurity best practices, including the importance of strong passwords and recognizing phishing attempts.
By adopting these strategies, organizations can significantly reduce their vulnerability to botnets like GoBruteforcer and protect their critical assets from unauthorized access and exploitation.