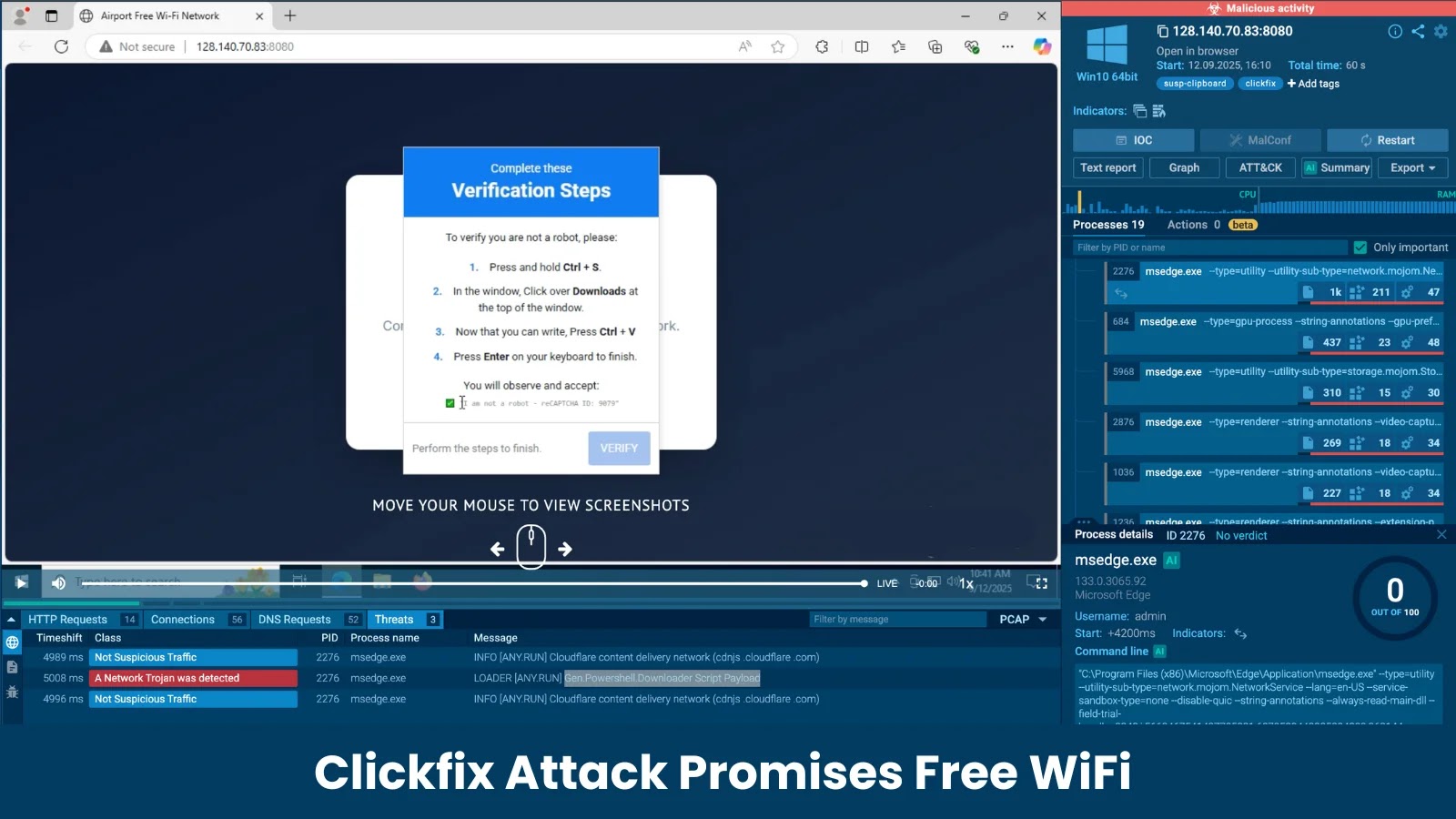
A newly identified cyber threat group, dubbed GhostRedirector, has been actively compromising Windows servers worldwide to manipulate search engine results for financial gain. Discovered by ESET Research, this group has infiltrated at least 65 servers across various countries, including Brazil, Thailand, Vietnam, and the United States. The victims span multiple sectors such as healthcare, retail, transportation, education, and technology.
Custom Tools and Techniques
GhostRedirector employs two previously undocumented tools:
1. Rungan: A C++ backdoor capable of executing commands on the compromised server, facilitating remote control and data exfiltration.
2. Gamshen: A malicious Internet Information Services (IIS) module designed to perform Search Engine Optimization (SEO) fraud. Gamshen intercepts web traffic and modifies server responses exclusively when requests originate from Google’s web crawler, Googlebot. This selective manipulation allows the attackers to artificially boost the search rankings of targeted websites, primarily gambling platforms.
Operational Tactics
The attack sequence initiated by GhostRedirector typically involves:
1. Initial Access: Exploiting vulnerabilities, likely through SQL injection, to gain entry into the server.
2. Privilege Escalation: Utilizing known exploits like EfsPotato and BadPotato to elevate privileges and create administrator-level user accounts, ensuring persistent access.
3. Deployment of Malicious Tools: Installing Rungan and Gamshen to maintain control and execute the SEO fraud scheme.
Implications and Recommendations
While the immediate impact on regular website visitors is minimal, the compromised servers suffer reputational damage due to their association with unethical SEO practices. To mitigate such threats, organizations are advised to:
– Regularly Update and Patch Systems: Ensure all software and systems are up-to-date to prevent exploitation of known vulnerabilities.
– Monitor Server Logs: Regularly review logs for unusual activities or unauthorized access attempts.
– Implement Strong Access Controls: Restrict administrative privileges and employ multi-factor authentication to enhance security.
By adopting these measures, organizations can bolster their defenses against sophisticated cyber threats like GhostRedirector.