GhostLocker: Exploiting Windows AppLocker to Disable EDR Systems
A groundbreaking tool named GhostLocker has emerged, showcasing a novel method to disable Endpoint Detection and Response (EDR) systems by leveraging Windows’ native AppLocker feature. Developed by security researcher zero2504, GhostLocker underscores a critical architectural flaw in contemporary EDR solutions: their dependence on user-mode components for analysis and reporting.
Understanding the Mechanism
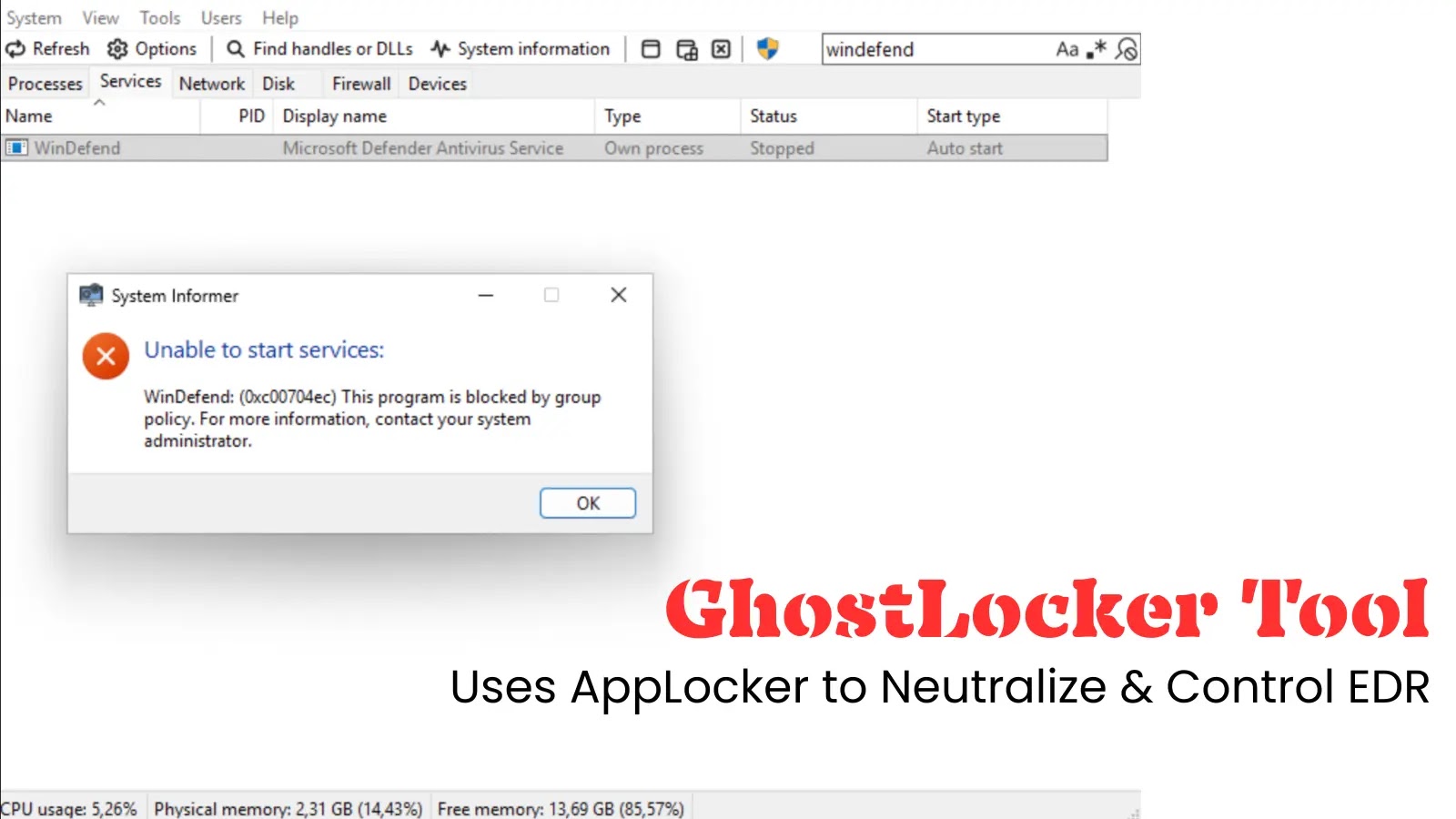
Traditional approaches to bypassing EDR systems often involve intricate kernel driver exploits or complex memory manipulations. In contrast, GhostLocker capitalizes on the legitimate administrative capabilities inherent in Windows systems. By utilizing AppLocker—a Microsoft application whitelisting framework introduced in Windows 7—GhostLocker enforces Deny rules against specific EDR executables.
The process is both straightforward and effective: system administrators possess the legitimate authority to control software execution. GhostLocker automates this control by deploying policies that explicitly prevent EDR processes from initiating or restarting.
Operational Modes of GhostLocker
GhostLocker offers two distinct modes of operation:
1. Dynamic Mode: This mode enumerates currently running processes to generate precise blocking rules tailored to the active environment.
2. Static Mode: Utilizing wildcard paths (e.g., `\MsMpEng.exe`), this mode blocks targeted executables without the need for prior enumeration.
Implications and Effectiveness
Research indicates that while AppLocker cannot terminate processes that are already running, a simple system reboot after policy application effectively neutralizes the EDR system. Notably, GhostLocker does not obstruct the EDR’s kernel drivers (`.sys` files). These drivers continue to load, register callbacks, and collect telemetry data.
However, this telemetry becomes ineffective without the corresponding user-mode services. Modern EDRs rely heavily on user-mode components to correlate events, perform behavioral analyses, and transmit alerts to centralized systems. By blocking these user-mode brains using AppLocker, GhostLocker effectively blinds the EDR, even though its kernel eyes remain operational.
Testing and Observations
Extensive testing against various commercial EDR products demonstrated that GhostLocker could achieve complete neutralization. Despite the blocking measures, management consoles continued to report the agents as online and protected, primarily because the heartbeat mechanisms were often decoupled from the analysis engines. Additionally, previously detected injection attacks went unnoticed due to the inactivity of the behavioral analysis engines.
Comparison with Other Techniques
GhostLocker presents a distinct advantage over attacks targeting Windows Defender Application Control (WDAC). While WDAC operates at the kernel level to block drivers, AppLocker policies function strictly in user mode. This user-mode operation makes AppLocker policies easier to deploy for targeted blocking while maintaining the appearance of a fully functional system.
Defensive Measures and Recommendations
It’s crucial to note that GhostLocker does not exploit a vulnerability but rather abuses legitimate features within Windows. To defend against such tactics, organizations are advised to:
– Monitor AppLocker Policy Changes: Utilize AppID.sys IOCTL signals to detect unauthorized modifications to AppLocker policies.
– Pre-validate Execution Status: Ensure that security products employ the `Get-AppLockerFileInformation` API to verify their own execution status and integrity.
By implementing these measures, organizations can enhance their resilience against techniques that seek to disable EDR systems through legitimate administrative functionalities.