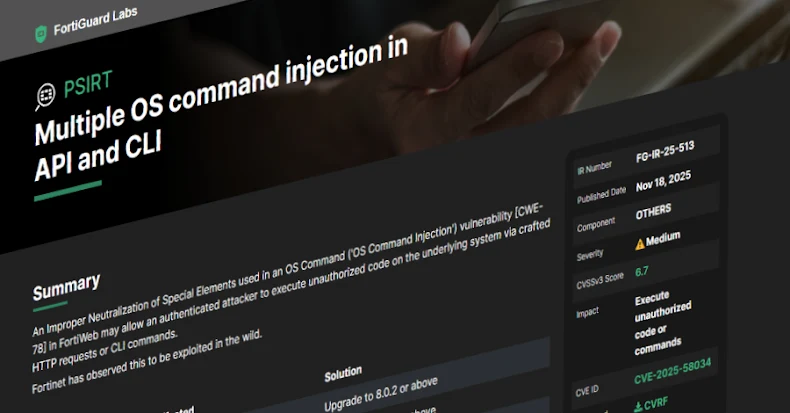
Fortinet has recently disclosed a medium-severity vulnerability in its FortiWeb web application firewall (WAF), identified as CVE-2025-58034, which has been actively exploited in the wild. This flaw, with a CVSS score of 6.7, allows authenticated attackers to execute unauthorized code on the underlying system through crafted HTTP requests or command-line interface (CLI) commands.
Understanding CVE-2025-58034
CVE-2025-58034 is categorized under CWE-78, indicating an Improper Neutralization of Special Elements used in an OS Command vulnerability, commonly known as OS Command Injection. This type of flaw arises when an application fails to properly sanitize user inputs, enabling attackers to inject and execute arbitrary commands on the host operating system.
In the context of FortiWeb, an attacker who has already authenticated can exploit this vulnerability by sending specially crafted HTTP requests or CLI commands. Successful exploitation could lead to unauthorized command execution, potentially compromising the integrity and security of the affected system.
Affected FortiWeb Versions
The vulnerability impacts the following FortiWeb versions:
– 8.0.0 through 8.0.1
– 7.6.0 through 7.6.5
– 7.4.0 through 7.4.10
– 7.2.0 through 7.2.11
– 7.0.0 through 7.0.11
Fortinet has addressed this issue in the following patched versions:
– 8.0.2 and above
– 7.6.6 and above
– 7.4.11 and above
– 7.2.12 and above
– 7.0.12 and above
Recommendations for Mitigation
To protect systems from potential exploitation of CVE-2025-58034, Fortinet recommends the following actions:
1. Immediate Patching: Upgrade FortiWeb appliances to the latest versions as specified above to remediate the vulnerability.
2. Restrict Administrative Access: Limit administrative access to trusted networks and users.
3. Monitor System Logs: Regularly review system logs for any unusual or unauthorized activities that may indicate exploitation attempts.
4. Implement Web Application Firewalls: Utilize additional security measures, such as web application firewalls, to detect and prevent malicious HTTP requests.
Contextualizing CVE-2025-58034 Amidst Other FortiWeb Vulnerabilities
The disclosure of CVE-2025-58034 follows closely on the heels of another critical FortiWeb vulnerability, CVE-2025-64446, which Fortinet addressed in version 8.0.2. CVE-2025-64446, with a CVSS score of 9.1, is a relative path traversal vulnerability that … attackers to execute administrative commands via crafted HTTP or HTTPS requests. This flaw has been actively exploited since early October 2025, leading to unauthorized administrative access and potential system compromise.
The rapid succession of these vulnerabilities underscores the importance of maintaining up-to-date systems and implementing robust security practices.
Industry Response and Best Practices
The cybersecurity community has responded promptly to these disclosures. Organizations such as the Cybersecurity and Infrastructure Security Agency (CISA) have added CVE-2025- … to their Known Exploited Vulnerabilities catalog, urging federal agencies to remediate the vulnerability by November 21, 2025. While CVE-2025-58034 has a lower severity score, its active exploitation necessitates immediate attention.
Security researchers have also highlighted the risks associated with these vulnerabilities. For instance, Qualys detailed the exploitation mechanics of CVE-2025- … , emphasizing the need for comprehensive security measures.
Conclusion
The active exploitation of CVE-2025-58034 in FortiWeb appliances serves as a critical reminder of the ever-evolving threat landscape. Organizations must prioritize timely patching, restrict administrative access, and continuously monitor their systems to detect and prevent potential attacks. By staying vigilant and proactive, businesses can safeguard their networks against emerging vulnerabilities and maintain robust cybersecurity defenses.