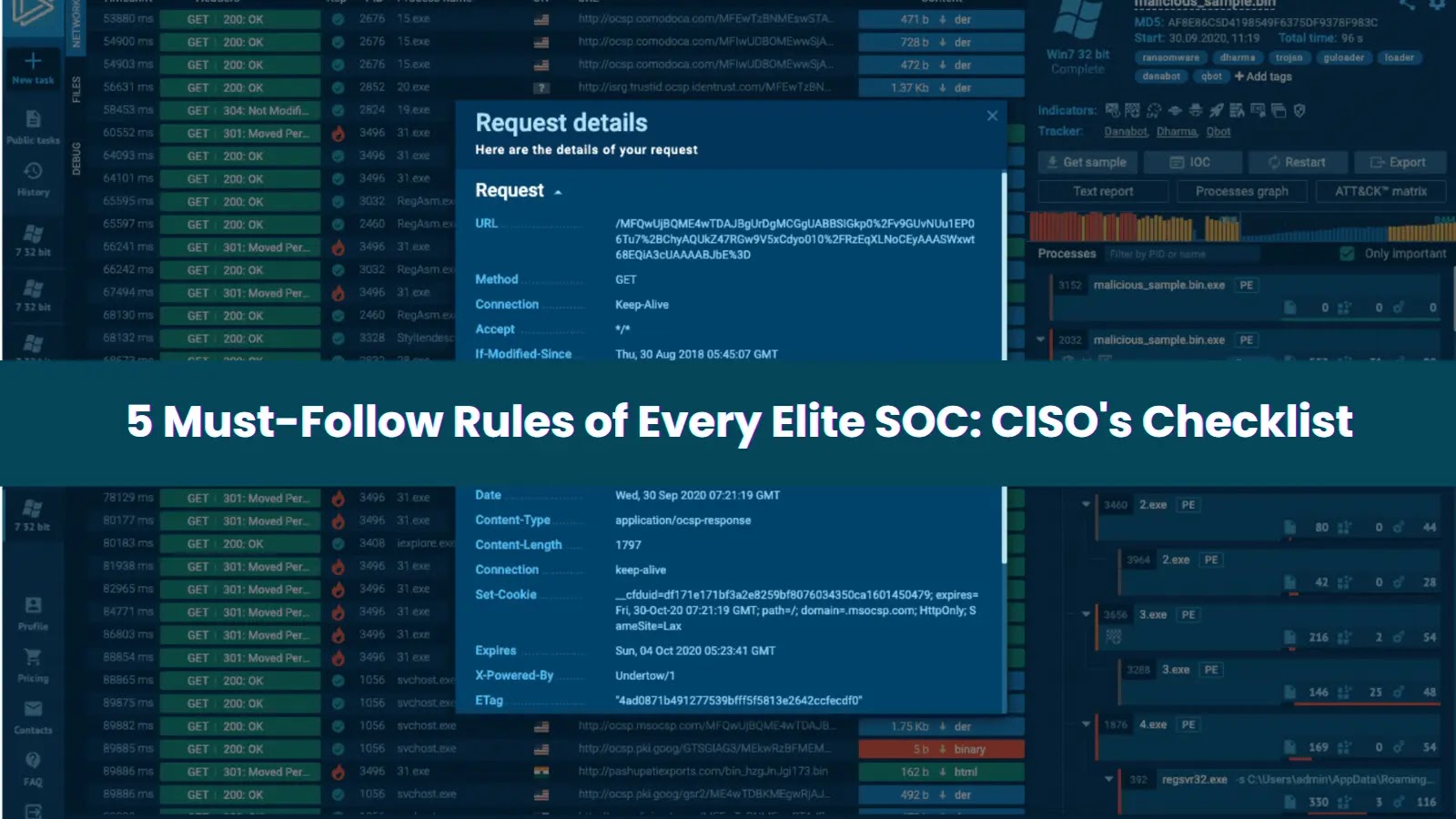
In the critical moments following a security alert, the distinction between an average Security Operations Center (SOC) and an elite one becomes evident. While some teams may scramble for answers, others operate seamlessly, swiftly transforming confusion into clarity. This level of efficiency is not coincidental but the result of adhering to fundamental principles that keep top-tier SOCs agile, focused, and proactive.
Rule #1: Prioritize Speed to Transform Panic into Precision
Rapid response is paramount in cybersecurity. When threats emerge, immediate visibility can convert chaos into clarity. The quicker a team comprehends the situation, the faster it can contain the threat, minimize damage, and restore normalcy.
Modern SOCs often utilize cloud-based sandboxes to enhance their response times. These platforms eliminate the need for deploying or maintaining virtual machines, allowing analyses to commence within seconds and providing teams with an instant view of the entire attack chain.
For example, in a recent analysis, a LockBit attack was fully exposed in just 33 seconds, complete with related Indicators of Compromise (IOCs), mapped Tactics, Techniques, and Procedures (TTPs), behavior details, and process trees.
With such rapid detection capabilities, teams can swiftly transition from reactive to strategic modes, understanding the threat, planning the response, and maintaining control.
Rule #2: Foster Collaboration in Threat Detection
Even the most skilled analysts cannot detect every threat in isolation. When communication falters and teams operate in silos, critical information can be overlooked, leading to missed alerts, redundant efforts, and sluggish investigations.
Collaboration is a cornerstone of effective SOC performance. Features that enable analysts to join the same live workspace, share results in real time, and coordinate across roles without switching tools are invaluable. Team leads can assign tasks, monitor progress, and track productivity from a unified interface, ensuring alignment across the team, regardless of time zones.
The outcome is a SOC that operates cohesively. Every analyst understands their role, every lead has a comprehensive view, and decisions are made promptly. This level of teamwork is essential for robust threat detection.
Rule #3: Automate Repetitive Tasks to Enhance Efficiency
SOC teams often face an overwhelming number of alerts, leading to time-consuming repetitive tasks such as opening files, running scripts, navigating pop-ups, or solving CAPTCHAs to trigger hidden payloads.
Implementing automated interactivity can alleviate this burden. Systems that automatically handle routine actions—like opening malicious links hidden behind QR codes, interacting with deceptive installers, solving CAPTCHAs, and performing other repetitive tasks—can expose every stage of the attack chain more efficiently.
The advantage is clear: analysts can bypass mundane tasks and focus directly on deriving insights. This leads to faster detection, cleaner data, and more time for investigations that require human judgment. Automation paves the way for cybersecurity professionals to perform at their best, saving significant time.
Rule #4: Engage in Hands-On Analysis to Uncover Hidden Threats
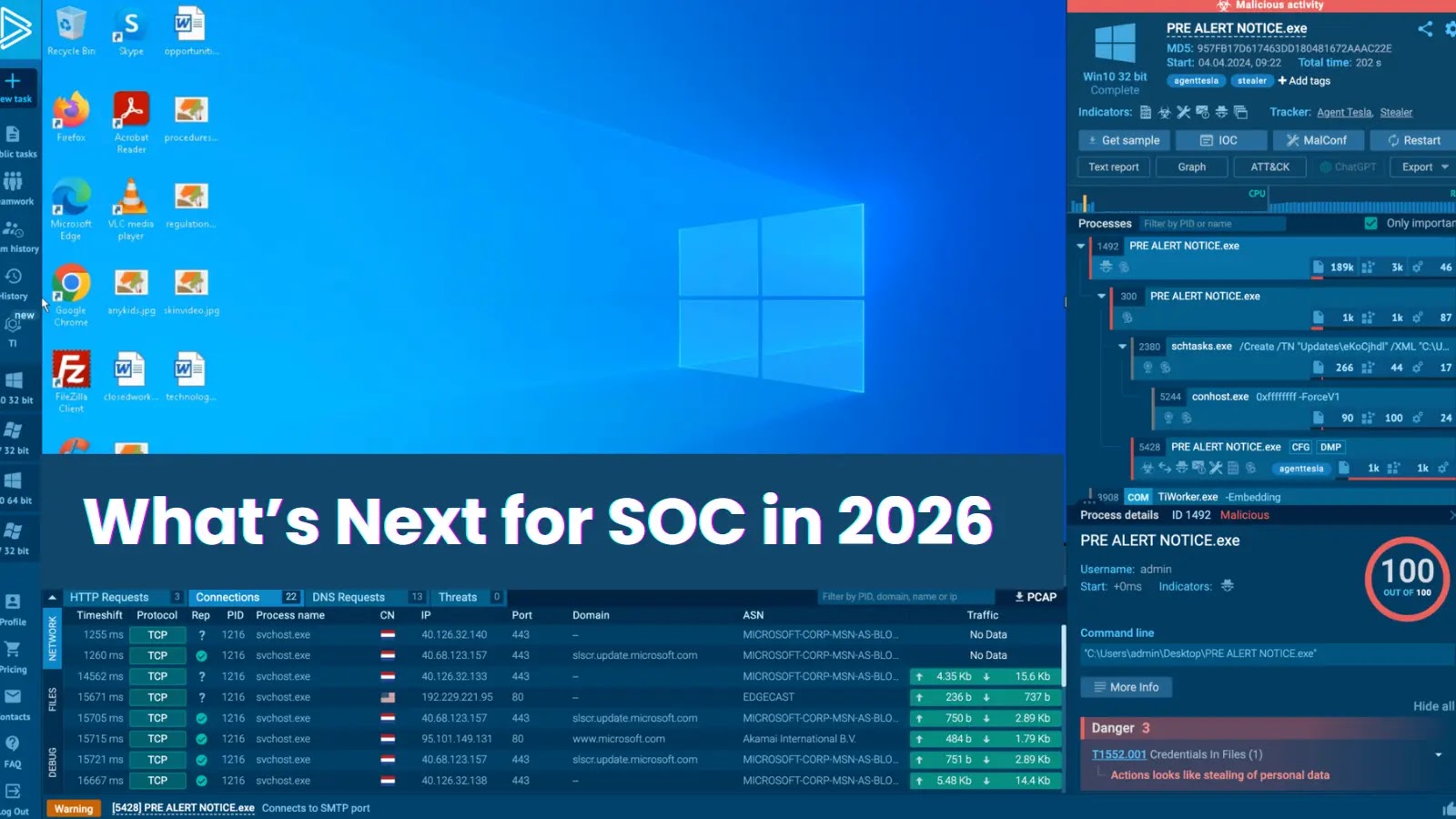
Even the most advanced detection tools can miss certain threats. False negatives are common; a file deemed safe might conceal malicious behavior deep within its code or activate only under specific conditions.
Therefore, elite SOCs do not rely solely on automation. When something appears suspicious, analysts delve deeper in an interactive environment, where they can open files, click buttons, follow links, and provoke real behavior in real time.
This hands-on approach transforms static analysis into active discovery, revealing payloads, persistence mechanisms, and hidden network activity that automated scanners might overlook.
While automation provides speed, hands-on analysis offers certainty. Balancing the two is crucial to prevent significant damage.
Rule #5: Train Analysts Through Real-World Experience
Developing exceptional analysts requires more than theoretical knowledge. Real expertise comes from observing how threats behave, testing hypotheses, and learning through direct experience, rather than relying solely on static examples or outdated labs.
Modern SOCs utilize sandboxes to transform real-world incidents into learning opportunities. Within these environments, junior analysts can safely explore live samples, experiment with behaviors, and build intuition that no textbook can impart.
Simultaneously, through teamwork management features, managers can observe progress in real time, tracking how analysts investigate, collaborate, and grow with each session.
The result is faster onboarding, stronger retention, and a team that learns from actual threats instead of simulated ones. This approach saves both time and training costs while building genuine, lasting expertise across the SOC.
Building a SOC That Sets the Standard
By integrating these five rules into daily SOC workflows, organizations can achieve remarkable results. Teams that combine automation, collaboration, and hands-on analysis work more intelligently, with measurable improvements across all levels.
– Up to 58% more threats identified: Detect attacks that bypass standard defenses with interactive analysis and data from a vast network of global businesses.
– 88% of attacks visible within 60 seconds: Observe live behavior instantly, automate detection, and enrich alerts with key indicators.
– 94% of users report faster triage: Collect IOCs and TTPs, simplify assessments, and act more swiftly with real threat data.
– 95% of SOC teams accelerate investigations: Collaborate in real time, manage more alerts, and track performance within a single workspace.
– Up to 20% reduction in Tier 1 workload and 30% fewer escalations: Decrease manual effort, eliminate hardware costs, and reduce alert fatigue.
By adopting these principles, organizations can build a SOC that not only meets but sets the standard in cybersecurity excellence.