Beware: New ClickFix Attack Mimics Windows Update to Deploy Malware
A sophisticated cyberattack campaign, known as Fake OS Update, has emerged, exploiting users’ trust in familiar Windows error messages to deploy malware. This attack is a variant of the ClickFix technique, which manipulates users into executing malicious commands under the guise of resolving non-existent system issues.
Discovery and Mechanism of the Attack
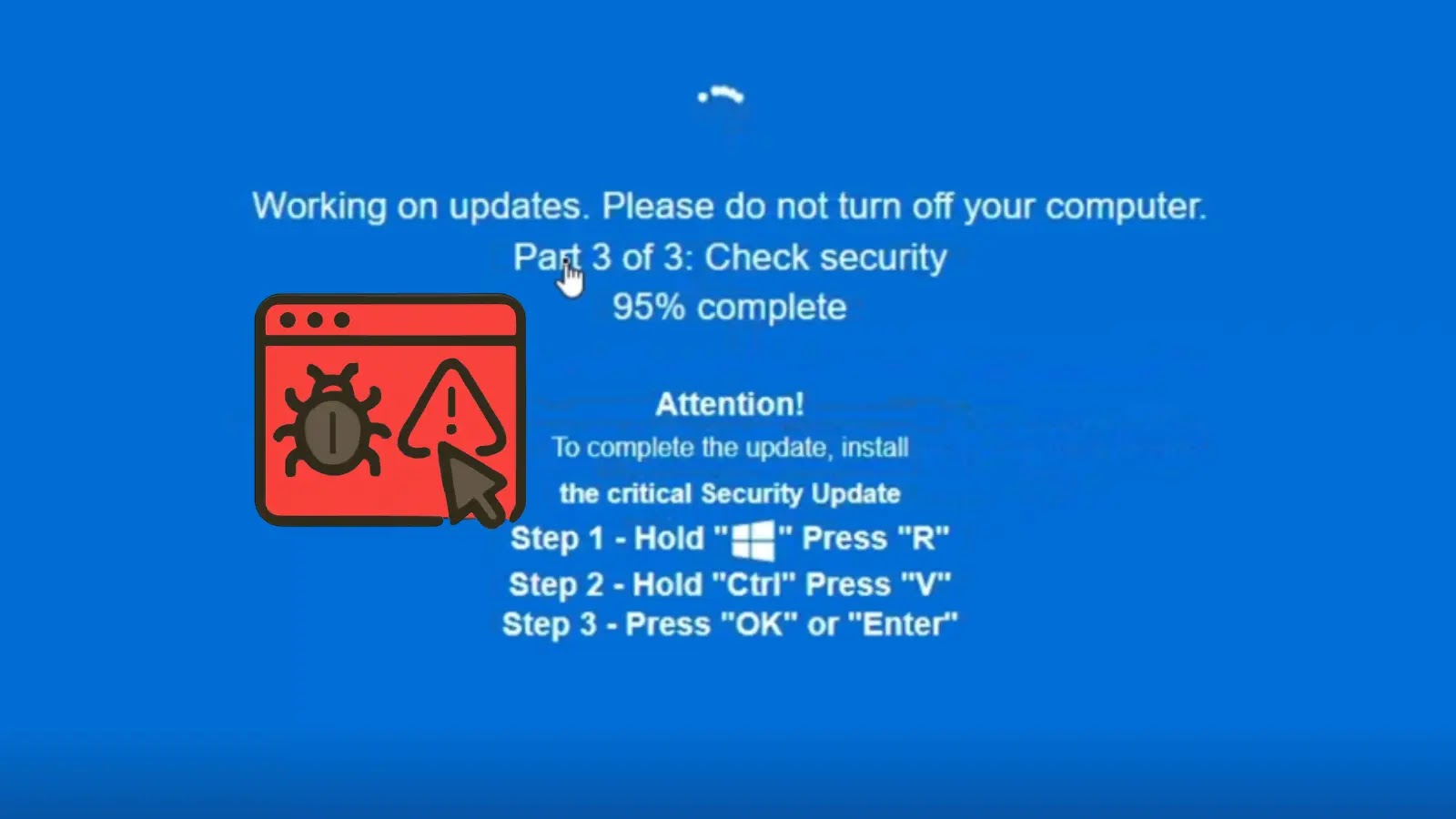
Cybersecurity researcher Daniel B., affiliated with the UK’s National Health Service, identified this deceptive campaign in October 2025. The attack primarily operates through the domain groupewadesecurity[.]com. Upon visiting this site—often accessed via malicious advertisements or spam links—users are presented with a full-screen overlay that convincingly simulates a Windows operating system crash or update prompt. This overlay, complete with error codes and progress indicators, is designed to induce panic and urgency, compelling users to follow the on-screen instructions.
Step-by-Step Deception
The attack unfolds in several stages:
1. Fake Blue Screen of Death (BSOD): Users encounter a screen mimicking the infamous Windows BSOD, suggesting a critical system error.
2. Manual Fix Instructions: The screen instructs users to perform specific actions:
– Pressing Ctrl+Alt+Del to restart services.
– Entering a command into a simulated command prompt.
– Downloading a recovery tool from a provided link.
These steps are meticulously crafted to appear as legitimate troubleshooting procedures.
Malware Deployment and Impact
In reality, following these instructions leads to the execution of malicious commands that can:
– Grant attackers remote access to the system.
– Install information-stealing malware.
– Deploy ransomware loaders.
The campaign’s sophistication is evident in its cross-device compatibility and its ability to evade immediate detection by browser security measures.
Evolution of ClickFix Attacks
ClickFix attacks have been a persistent threat since 2020, evolving in complexity and effectiveness. Earlier versions often involved simpler tactics, such as fake browser update prompts. However, recent iterations, like the Fake OS Update campaign, demonstrate a significant advancement in social engineering techniques. Attackers now employ hyper-realistic graphics, localized language support, and timely lures tied to real events, such as Microsoft’s Patch Tuesday updates, to enhance credibility and effectiveness.
Broader Context and Related Threats
The Fake OS Update campaign is part of a broader trend where cybercriminals exploit users’ trust in legitimate processes to deploy malware. Similar tactics have been observed in other campaigns:
– CastleLoader Attack: This campaign uses Cloudflare-themed ClickFix phishing pages and doctored GitHub repositories to compromise Windows hosts. Users are tricked into executing PowerShell commands that download and install malware, including information stealers and remote-access trojans. ([cybersecuritynews.com](https://cybersecuritynews.com/castleloader-attack-using-cloudflare-themed-clickfix-technique/?utm_source=openai))
– Fake BBC News Page Attack: In this attack, users are redirected to a convincing replica of a BBC news website, which then presents a fake Cloudflare verification screen. Users are instructed to execute commands that lead to malware installation. ([cybersecuritynews.com](https://cybersecuritynews.com/new-clickfix-attack/?utm_source=openai))
– Lampion Banking Malware: This malware campaign employs fake ClickFix lures to steal banking information. Users receive fraudulent emails impersonating legitimate software update services, leading them to download and execute malicious software. ([cybersecuritynews.com](https://cybersecuritynews.com/lampion-banking-malware-employs-clickfix-lures/?utm_source=openai))
Mitigation Strategies
To protect against such sophisticated social engineering attacks, users and organizations should adopt the following measures:
1. User Education and Awareness: Regular training programs should be implemented to help users recognize and avoid phishing attempts and deceptive prompts.
2. Behavioral Monitoring: Deploy security solutions that monitor for unusual system behaviors, such as unexpected command executions or unauthorized software installations.
3. Regular Software Updates: Ensure that all operating systems and applications are up-to-date with the latest security patches to mitigate vulnerabilities that attackers might exploit.
4. Use of Security Extensions: Employ browser extensions like uBlock Origin to block access to known malicious domains and prevent unwanted scripts from executing.
5. Verification of System Messages: Be skeptical of unexpected system messages or prompts. Verify their authenticity through official channels before taking any action.
Conclusion
The Fake OS Update ClickFix attack underscores the evolving nature of cyber threats, where attackers increasingly rely on sophisticated social engineering tactics to deceive users. By staying informed about these threats and implementing robust security practices, individuals and organizations can better defend against such deceptive campaigns.