In a significant cybersecurity development, researchers have uncovered critical vulnerabilities within eSIM technology that could allow attackers to clone mobile subscriber profiles and hijack phone identities. This discovery raises serious concerns about the security of over 2 billion SIMs worldwide.
The Discovery
AG Security Research recently demonstrated the first successful public hack against consumer GSMA eUICC and EAL-certified GSMA security chips. They managed to extract private ECC keys from compromised eUICC cards and download eSIM profiles from major mobile network operators—including AT&T, Vodafone, O2, Orange, and T-Mobile—in unencrypted formats.
Technical Exploitation
The attack exploits fundamental flaws in the Java Card Virtual Machine implementation, specifically targeting type confusion vulnerabilities similar to issues reported in 2019. The researchers developed a proof of concept that mimics malicious applet installation over the OTA SMS-PP protocol, allowing attackers to bypass multiple security mechanisms, including EAL4/5 certification and Java Card Runtime security features.
Implications of the Attack
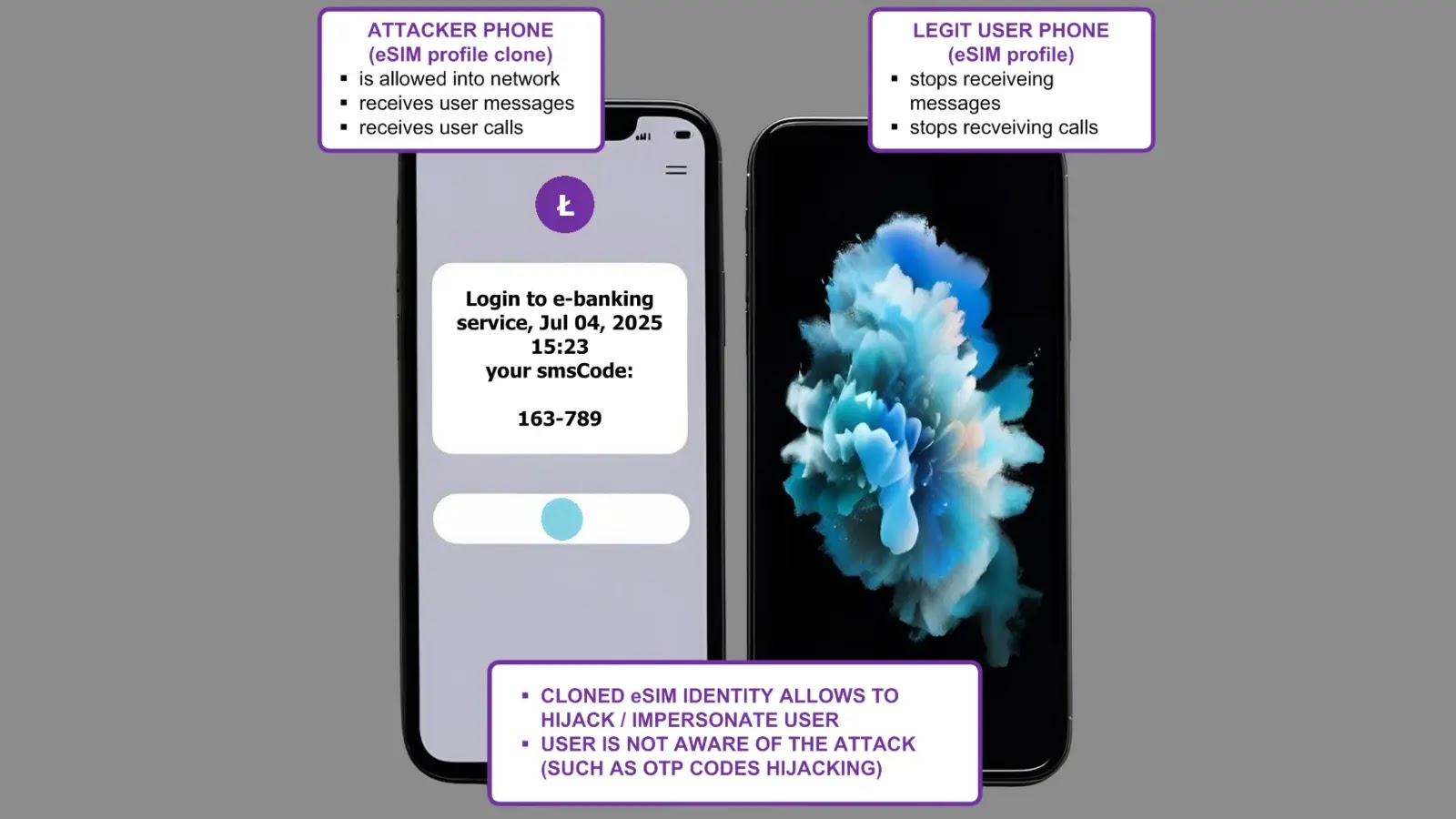
The most alarming demonstration involved successful eSIM cloning tests conducted on Orange Poland’s network in July 2025. Researchers installed identical Orange eSIM profiles on two different physical eUICC cards and demonstrated complete subscriber identity hijacking. When the malicious device was activated, it immediately began receiving all calls and SMS messages intended for the legitimate subscriber. This cloning capability poses severe risks for two-factor authentication systems, as attackers can intercept SMS-based verification codes for services like Gmail and e-banking platforms. Legitimate users remain unaware of the hijacking, as no visible trace appears at the user end.
Industry Response
In response to these findings, Kigen has implemented type safety checks across approximately 180 JavaCard bytecode instructions and coordinated with GSMA to update the TS.48 Generic Test Profile specification. The company distributed patches to millions of eSIMs and issued a security bulletin detailing mitigation strategies. GSMA has also published new application notes and shut down all test profiles to prevent further exploitation.
Broader Security Concerns
This breakthrough represents a significant security breach in the eSIM ecosystem, which processes over 2 billion SIMs enabled by Kigen’s secure SIM OS. The vulnerability affects over 2 billion SIMs, allowing one compromised certificate to access any mobile operator’s eSIM profiles globally.
Additional Attack Vectors
Beyond the cloning vulnerability, eSIM technology faces other security challenges:
– SIM Swap Attacks: Cybercriminals can impersonate users to request a switch from a physical SIM to an eSIM, gaining control over the victim’s phone number. This access allows them to intercept calls, messages, and bypass two-factor authentication, potentially leading to financial fraud and identity theft. ([astound.com](https://www.astound.com/learn/mobile/can-an-esim-be-hacked/?utm_source=openai))
– Phishing Scams: Attackers may send fraudulent emails or messages posing as trusted entities, prompting users to provide sensitive information or download malicious eSIM profiles. ([makeuseof.com](https://www.makeuseof.com/how-esim-can-be-hacked/?utm_source=openai))
– Malware and Spyware: Malicious software can infiltrate devices to steal eSIM data, monitor communications, and even control the device remotely. ([makeuseof.com](https://www.makeuseof.com/how-esim-can-be-hacked/?utm_source=openai))
– QR Code Exploitation: Since eSIM activation often involves scanning QR codes, attackers can create fraudulent codes that, when scanned, install malicious profiles or redirect data through the hacker’s servers. ([makeuseof.com](https://www.makeuseof.com/how-esim-can-be-hacked/?utm_source=openai))
Protective Measures
To mitigate these risks, users and organizations should adopt the following practices:
1. Use Trusted Providers: Only use well-established eSIM providers with strong reputations for security. ([cybersecuritynews.com](https://cybersecuritynews.com/securing-your-digital-life-with-providers-like-esim-plus/amp/?utm_source=openai))
2. Enable Two-Factor Authentication (2FA): Implement 2FA to add an extra layer of security to accounts. ([cybersecuritynews.com](https://cybersecuritynews.com/securing-your-digital-life-with-providers-like-esim-plus/amp/?utm_source=openai))
3. Regular Software Updates: Keep device software and eSIM management apps up to date to protect against known vulnerabilities. ([cybersecuritynews.com](https://cybersecuritynews.com/securing-your-digital-life-with-providers-like-esim-plus/amp/?utm_source=openai))
4. Avoid Public Wi-Fi Networks: Use a virtual private network (VPN) when accessing eSIM profiles or managing settings on public Wi-Fi to prevent man-in-the-middle attacks. ([cybersecuritynews.com](https://cybersecuritynews.com/securing-your-digital-life-with-providers-like-esim-plus/amp/?utm_source=openai))
5. Monitor Account Activity: Regularly check eSIM account activity for unauthorized changes or unfamiliar connections. ([cybersecuritynews.com](https://cybersecuritynews.com/securing-your-digital-life-with-providers-like-esim-plus/amp/?utm_source=openai))
6. Be Wary of Phishing Attempts: Remain vigilant against unsolicited communications requesting personal information or prompting the scanning of QR codes. ([cybernews.com](https://cybernews.com/best-esim-providers/are-esims-safe/?utm_source=openai))
Conclusion
The recent discovery of eSIM vulnerabilities underscores the importance of robust security measures in the rapidly evolving mobile technology landscape. As eSIM adoption grows, both users and providers must remain vigilant and proactive in implementing security protocols to safeguard against potential threats.