As the digital landscape continues to evolve at an unprecedented pace, organizations worldwide are preparing for a new wave of security challenges in 2025. The convergence of artificial intelligence (AI), geopolitical tensions, and quantum computing is reshaping the threat environment, necessitating a fresh approach to risk management and cyber defense. This analysis explores the most significant emerging risks and the strategies enterprises must adopt to remain resilient against mounting cyber threats.
The Rise of AI-Driven Threats
Artificial intelligence has rapidly become a double-edged sword in cybersecurity. On one hand, AI-powered tools are assisting organizations in detecting anomalies, automating responses, and predicting attacks with greater accuracy. On the other hand, cybercriminals are weaponizing AI to launch more sophisticated and scalable attacks.
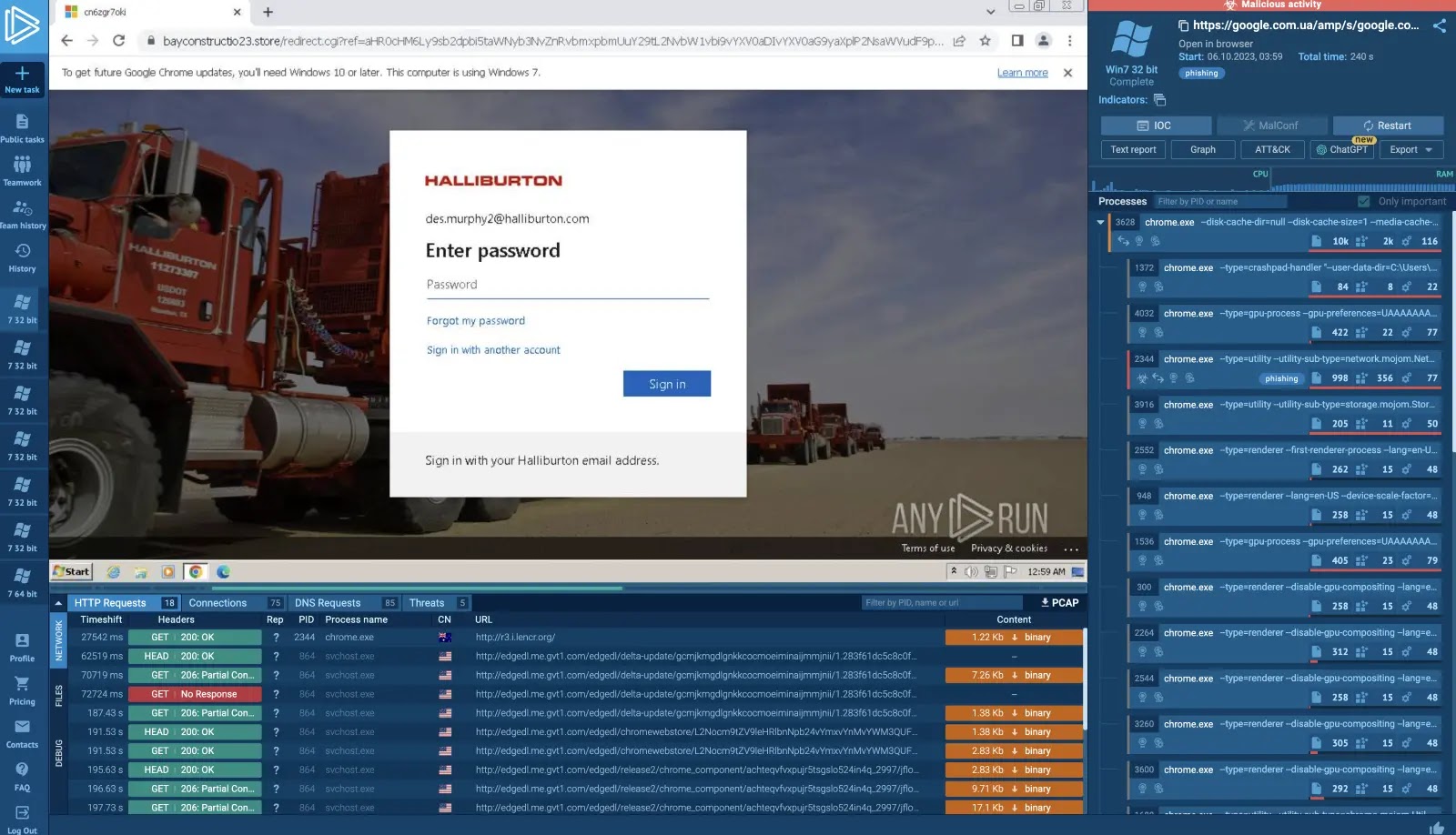
In 2025, enterprises are witnessing a surge in AI-driven social engineering campaigns. Deepfakes and voice cloning are being used to impersonate executives, deceive employees, and bypass traditional verification methods. Automated malware, created and adapted by generative AI, can evade signature-based defenses and mutate rapidly, making detection and response more challenging than ever.
Organizations are responding by investing in adversarial AI training, deploying behavioral analytics, and implementing multi-factor authentication, including biometric and contextual checks. However, the arms race between attackers and defenders is intensifying, and staying ahead will require continuous innovation and vigilance.
Quantum Computing: The Next Frontier of Risk
While quantum computing promises revolutionary advances in medicine and logistics, it poses a looming threat to encryption standards. Experts warn that quantum computers could soon have the power to break widely used cryptographic algorithms, exposing sensitive data to interception and decryption.
In anticipation of this risk, organizations are transitioning to post-quantum cryptography, adopting algorithms designed to withstand quantum attacks. However, the migration is complex and time-consuming, particularly for industries with legacy systems and vast data stores. The specter of “harvest now, decrypt later” attacks, where adversaries steal encrypted data now, intending to decrypt it once quantum capabilities mature, adds urgency to the need for quantum-safe security measures.
Geopolitical Tensions and Supply Chain Attacks
Geopolitical instability is increasingly spilling into cyberspace, with nation-state actors targeting critical infrastructure, supply chains, and intellectual property. In 2025, cyberattacks are being used as tools of economic sabotage and political coercion, often blurring the lines between criminal and state-sponsored activity.
Supply chain vulnerabilities remain a top concern. Attackers exploit weak links in vendor networks and third-party software to access otherwise well-defended organizations. The complexity of modern supply chains, combined with the proliferation of cloud services and IoT devices, has dramatically expanded the attack surface.
Organizations are adopting zero-trust architectures, segmenting networks, and enforcing strict access controls for partners and vendors to counter these threats. Continuous monitoring and real-time threat intelligence sharing are becoming standard practices, as is the need for transparent and enforceable security standards across supply chains.
Ransomware Evolution and the Human Factor
Ransomware attacks continue to evolve, with criminals adopting new tactics such as double extortion, in which data is encrypted and threatened with public release. The rise of Ransomware-as-a-Service (RaaS) platforms has lowered the barrier to entry for attackers, leading to an increase in the frequency and sophistication of attacks.
The human factor remains a critical vulnerability. Phishing attacks, often the initial vector for ransomware, are becoming more convincing, leveraging AI to craft personalized and contextually relevant messages. Employee training and awareness programs are essential but must be continuously updated to address the evolving tactics of attackers.
Organizations are also investing in advanced endpoint detection and response (EDR) solutions, regular data backups, and incident response planning to mitigate the impact of ransomware attacks. Collaboration with law enforcement and information sharing within industry groups are crucial components of a comprehensive defense strategy.
The Proliferation of IoT Devices and 5G Networks
The rapid expansion of Internet of Things (IoT) devices and the rollout of 5G networks are creating new security challenges. IoT devices often lack robust security features, making them easy targets for attackers who can exploit them to gain access to larger networks.
5G networks, while offering faster speeds and lower latency, also introduce new vulnerabilities. The increased number of connected devices and the complexity of network slicing can provide attackers with more entry points and potential attack vectors.
Organizations must ensure that IoT devices are securely configured and regularly updated. Implementing network segmentation and monitoring for anomalous behavior can help detect and prevent attacks. Collaboration with device manufacturers to establish security standards and best practices is also essential.
Regulatory Changes and Compliance Challenges
As cyber threats evolve, so do regulatory requirements. Governments and international bodies are introducing stricter standards for data protection, critical infrastructure security, and incident reporting. Compliance with these regulations is becoming more complex and resource-intensive.
Organizations must stay informed about regulatory changes and ensure that their security practices align with legal requirements. This includes conducting regular audits, implementing robust data protection measures, and developing incident response plans that meet reporting obligations.
Failure to comply with regulations can result in significant financial penalties and reputational damage. Therefore, integrating compliance into the overall cybersecurity strategy is essential for maintaining trust and avoiding legal repercussions.
The Importance of Cyber Resilience
In the face of these emerging risks, cyber resilience—the ability to prepare for, respond to, and recover from cyber incidents—is more critical than ever. Organizations must adopt a holistic approach to cybersecurity that encompasses prevention, detection, response, and recovery.
This includes investing in advanced security technologies, fostering a culture of security awareness, and developing comprehensive incident response and business continuity plans. Regular testing and updating of these plans ensure that organizations can quickly adapt to new threats and minimize the impact of incidents.
Collaboration with industry peers, government agencies, and cybersecurity experts can provide valuable insights and resources. Sharing information about threats and best practices enhances the collective defense against cyber adversaries.
Conclusion
The cybersecurity landscape in 2025 is characterized by rapid technological advancements, evolving threats, and increasing regulatory pressures. Organizations must remain vigilant and proactive, continuously adapting their strategies to address emerging risks. By embracing innovation, fostering collaboration, and prioritizing resilience, enterprises can navigate the complexities of the digital age and safeguard their assets, reputation, and stakeholders.