Emerging Cyber Threats: QR Codes, ClickFix, and LOLBins Challenge SOC Defenses
In the rapidly evolving landscape of cybersecurity, attackers are increasingly exploiting everyday technologies to circumvent traditional security operations centers (SOCs). Recent analyses have highlighted the sophisticated use of QR code phishing, ClickFix social engineering, and Living Off the Land Binaries (LOLBins) as methods that effectively evade standard defenses.
ClickFix Attacks: Mastering Human Deception
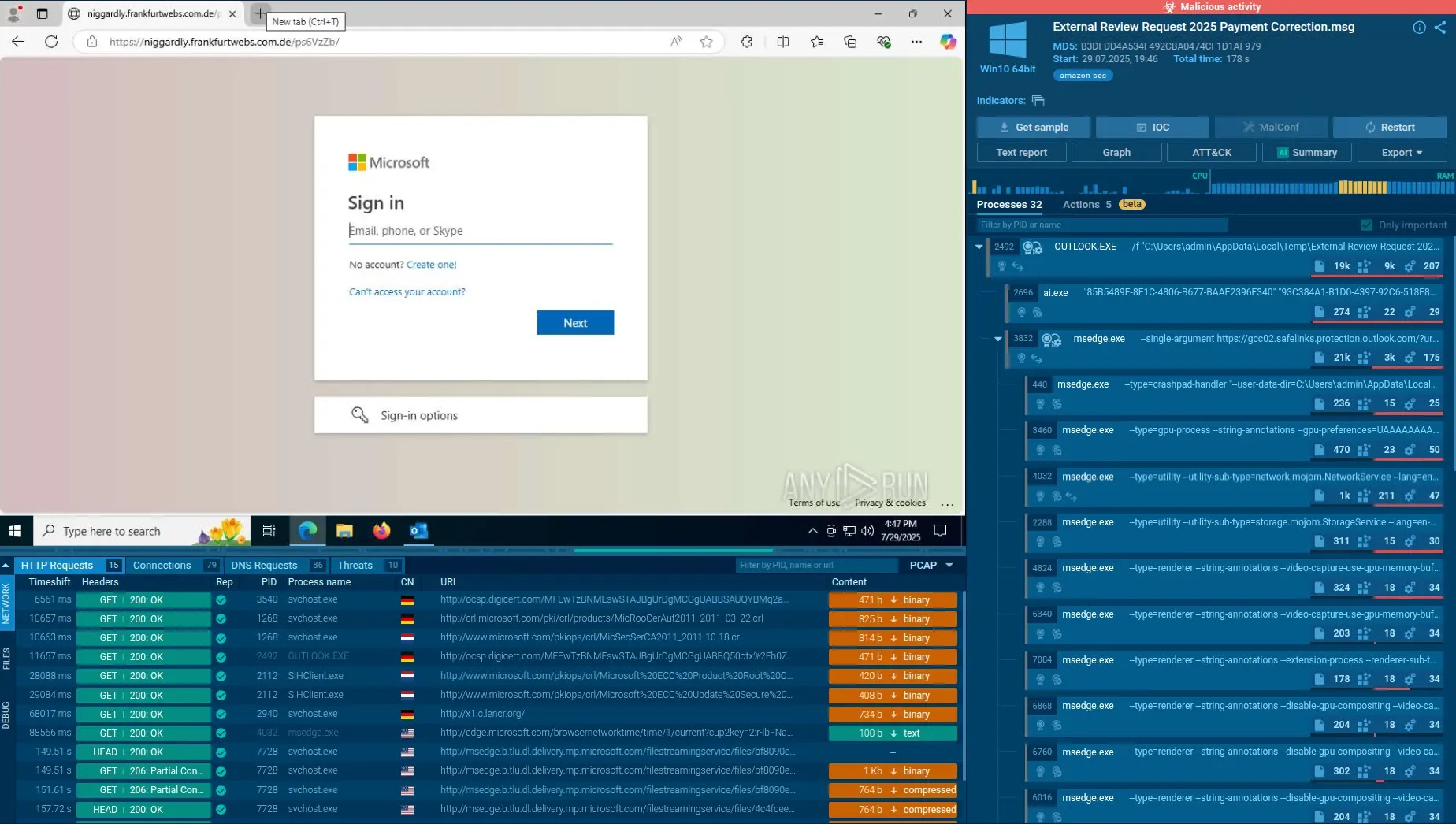
ClickFix attacks represent a significant advancement in social engineering tactics. In these schemes, cybercriminals dispatch phishing emails that mimic trusted platforms, such as booking services, and include counterfeit CAPTCHAs. When a user interacts with these elements, a malicious PowerShell script is discreetly copied to the clipboard. The user is then prompted to paste and execute this script through a system dialog, unknowingly initiating the malware.
This multi-layered deception relies heavily on user interaction, making it particularly challenging for automated security systems to detect. The attack chain often culminates in the deployment of information stealers like Lumma or remote access trojans such as AsyncRAT, establishing persistence by modifying startup files. Traditional security tools often struggle with these tactics, as they are designed to bypass automated scanners through manual user steps.
PhishKit Attacks: QR Codes as Stealth Vectors
Phishing kits, commonly referred to as phishkits, have become readily accessible on the dark web, enabling even novice attackers to execute sophisticated campaigns against major corporations like Microsoft and Google. A notable evolution in these kits is the incorporation of QR codes into PDF attachments that masquerade as legitimate documents, such as those from DocuSign. When scanned, these QR codes direct users to phishing sites on their mobile devices, where the smaller screen size can obscure telltale signs of malicious intent.
These advanced phishing kits often utilize AI-generated lures, multi-stage verification processes, and CAPTCHAs like Cloudflare Turnstile to create convincing fake login pages aimed at harvesting user credentials. Automated analysis tools can extract QR code links, solve embedded challenges, and trace the entire attack chain, revealing connections to known threat groups. However, many security defenses currently overlook QR code content, allowing these attacks to bypass traditional detection methods.
LOLBins: Weaponizing Trusted Tools
LOLBins involve the misuse of legitimate Windows utilities—such as PowerShell, mshta.exe, and cmd.exe—to execute malicious activities under the guise of normal operations. For instance, a phishing attack might use a shortcut (.lnk) file to invoke mshta via PowerShell, retrieving payloads from remote servers. To further obfuscate the attack, decoy PDFs may be downloaded alongside the actual malware, such as DeerStealer.
This living off the land strategy is particularly effective because it leverages trusted system tools, making it difficult for traditional security measures to identify and block the malicious activity. Behavioral analysis within sandbox environments can help uncover connections to command-and-control servers and persistence mechanisms, distinguishing between legitimate administrative tasks and malicious exploitation.
Implications for Security Operations Centers
The emergence of these sophisticated attack vectors underscores the limitations of relying solely on automated security solutions. The interactive nature of ClickFix attacks, the obfuscation provided by QR code phishing, and the stealth of LOLBins highlight the need for SOCs to adopt more dynamic and comprehensive defense strategies.
Integrating interactive analysis tools with shared intelligence can enhance detection capabilities, allowing SOCs to simulate user interactions and uncover complex attack chains. By staying informed about these evolving threats and adapting their defenses accordingly, organizations can better protect themselves against the increasingly sophisticated tactics employed by cybercriminals.