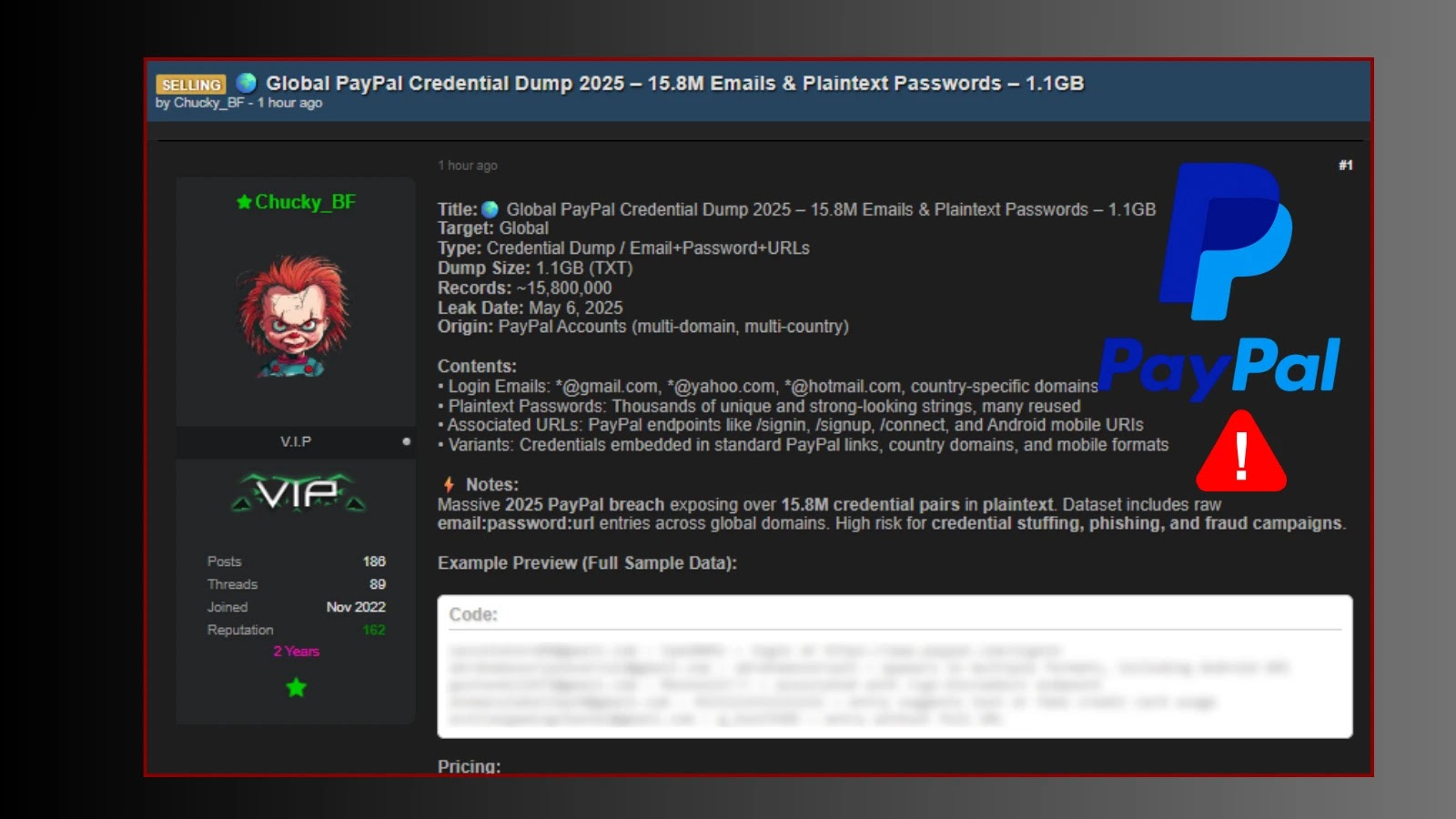
In recent months, cybersecurity researchers have identified a surge in Android spyware campaigns that exploit users’ trust in secure messaging applications. Malicious actors are distributing trojanized versions of popular apps like Signal and ToTok, aiming to infiltrate devices and harvest sensitive information.
Deceptive Distribution Tactics
The attackers employ sophisticated social engineering techniques to lure users into downloading these malicious applications. Phishing websites and counterfeit app stores are the primary distribution channels, presenting users with seemingly legitimate download links. For instance, domains such as signal.ct.ws and encryption-plugin-signal.com-ae.net have been identified as sources distributing a fake Signal Encryption Plugin. Similarly, fraudulent ToTok applications have been disseminated through websites mimicking the Samsung Galaxy Store.
Infection Mechanism and Data Exfiltration
Once installed, these spyware applications request extensive permissions under the guise of enhanced functionality. Upon granting these permissions, the malware embeds itself into the system, operating discreetly to avoid detection. The spyware then initiates data exfiltration processes, collecting a wide array of sensitive information, including:
– Contact lists
– SMS messages
– Media files
– Documents
– Device information
– Lists of installed applications
In the case of the ToTok-specific spyware, it targets .ttkmbackup files to extract chat histories. The exfiltrated data is encrypted using a hardcoded AES-CBC key and transmitted via HTTPS POST requests to command-and-control servers controlled by the attackers.
Technical Analysis of the Spyware Families
The campaigns revolve around two distinct spyware families:
1. AndroidSpy.ProSpy: This variant impersonates Signal and ToTok plugins. It is distributed through phishing domains that present a non-existent Signal Encryption Plugin, deceiving users into manual APK installations.
2. AndroidSpy.ToSpy: This variant poses as a standalone ToTok application. It is disseminated via counterfeit websites designed to resemble legitimate app stores, such as the Samsung Galaxy Store.
Both variants are manually installed outside official app stores, exploiting Android’s unknown sources setting to bypass standard security measures.
Persistence and Concealment Strategies
To maintain persistence on the infected device, the spyware employs several techniques:
– Foreground Services: The malware registers a foreground service to ensure continuous operation, even if the application is closed.
– Activity Aliasing: By modifying the AndroidManifest with activity-alias entries, the spyware changes its icon and name to Play Services, effectively camouflaging itself among legitimate system applications.
– AlarmManager and BroadcastReceivers: The malware sets alarms to restart its services if terminated and registers a BOOT_COMPLETED BroadcastReceiver to relaunch after device reboots, ensuring its longevity on the device.
Regional Focus and Targeted Demographics
These spyware campaigns appear to be regionally focused, with a particular emphasis on users in the United Arab Emirates. By leveraging the local popularity of Signal and ToTok, the attackers increase the likelihood of successful infections. The choice of these specific applications suggests a strategic targeting of privacy-conscious individuals who may be more inclined to use secure messaging platforms.
Mitigation Strategies and Recommendations
To protect against such sophisticated threats, users are advised to:
– Download Applications Exclusively from Official Sources: Always obtain apps from trusted platforms like the Google Play Store to minimize the risk of downloading malicious software.
– Verify App Authenticity: Before installation, check the developer’s credentials, read user reviews, and confirm the app’s legitimacy.
– Exercise Caution with Permissions: Be wary of applications requesting excessive permissions that are unrelated to their intended functionality.
– Keep Devices Updated: Regularly update your device’s operating system and applications to benefit from the latest security patches.
– Utilize Security Solutions: Employ reputable mobile security software to detect and prevent potential threats.
Conclusion
The emergence of Android spyware masquerading as trusted messaging applications underscores the evolving tactics of cybercriminals. By exploiting users’ trust in secure communication platforms, these malicious actors can infiltrate devices and exfiltrate sensitive information. Vigilance, informed downloading practices, and robust security measures are essential in mitigating the risks posed by such sophisticated threats.