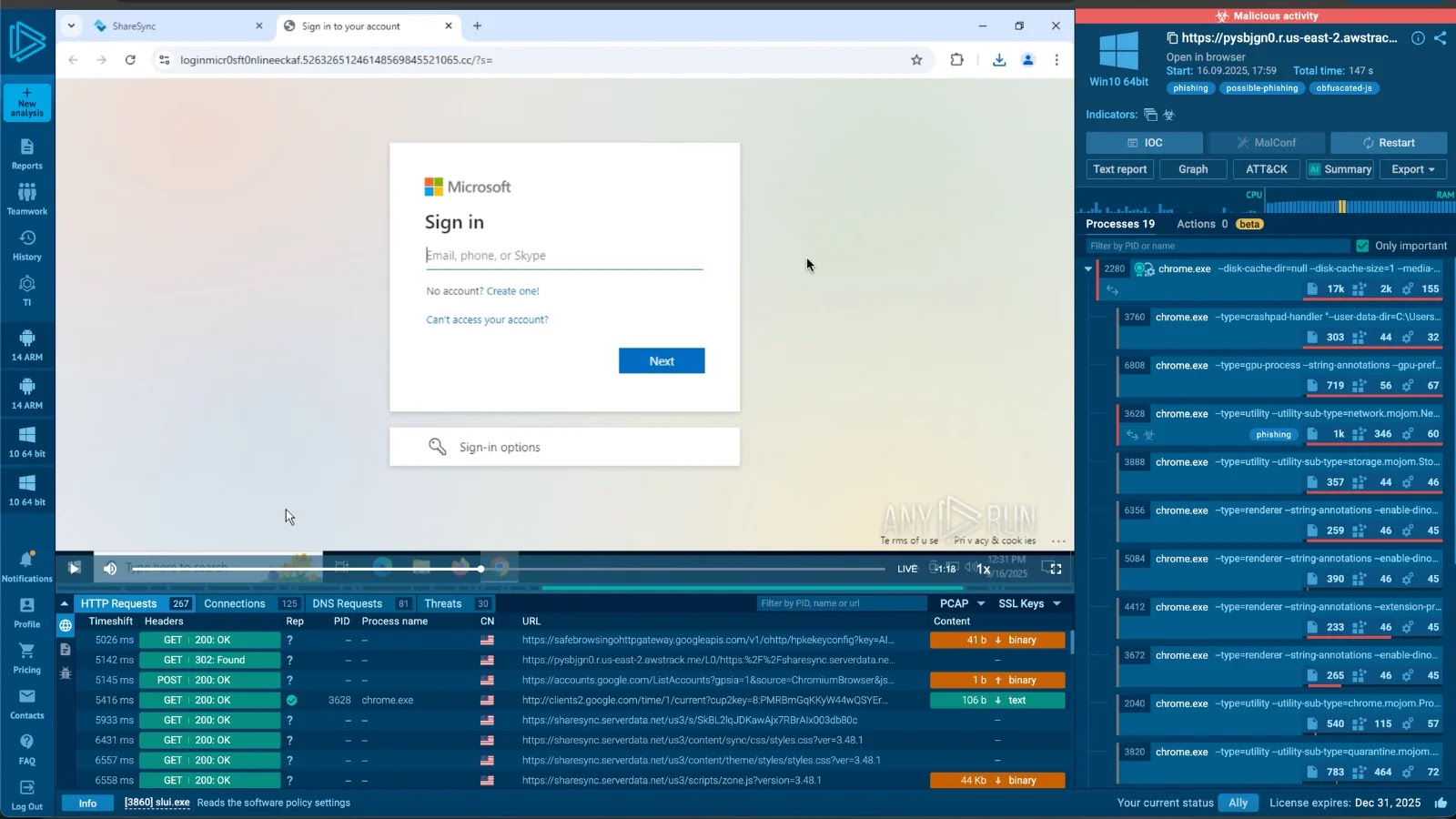
In the evolving landscape of cyber threats, a new phishing kit named Tykit has surfaced, posing significant risks to corporate security. First identified in May 2025, Tykit has gained momentum in recent months, particularly during September and October, by adeptly impersonating Microsoft 365 login pages to harvest corporate account credentials.
Understanding Tykit’s Mechanism
Tykit distinguishes itself from conventional phishing tools through its advanced obfuscation techniques and multi-stage command-and-control (C2) interactions. This complexity enhances its effectiveness in credential theft across various organizations worldwide.
A notable aspect of Tykit’s operation is its exploitation of Scalable Vector Graphics (SVG) files as delivery mechanisms. These seemingly harmless image files embed JavaScript payloads that, upon execution, reconstruct malicious code using XOR encoding. This code then utilizes the eval() function to redirect victims to counterfeit login pages, thereby facilitating the theft of sensitive information.
Technical Insights into Tykit’s Operations
Cybersecurity firm ANY.RUN has conducted an in-depth analysis of Tykit, revealing its sophisticated approach:
– Initial Detection and Spread: Tykit was first observed in sandbox environments in early May 2025. Researchers traced a single suspicious SVG file (SHA256: a7184bef39523bef32683ef7af440a5b2235e83e7fb83c6b7ee5f08286731892) to over 189 related sessions, indicating a rapid proliferation of this phishing kit.
– Infrastructure and Domain Patterns: The phishing pages are hosted on domains such as loginmicr0sft0nlineeckaf[.]52632651246148569845521065[.]cc, which often append Base64-encoded victim emails via the “?s=” parameter. Data exfiltration targets servers on segy[.]cc variants, sending staged POST requests to /api/validate and /api/login. The infrastructure exhibits patterns resembling domain-generation algorithms, with phishing hosts following the pattern ^loginmicr(o|0)s.?.([a-z]+)?\d+.cc$ and C2 servers following ^segy?.
– Obfuscation and Anti-Detection Measures: Tykit’s consistent client-side logic and obfuscation techniques suggest organized operators distributing it widely. The kit employs basic anti-debugging measures, such as blocking developer tools and context menus, to evade detection.
The Phishing Process
The attack sequence initiated by Tykit unfolds as follows:
1. Initial Contact: The victim receives an SVG file prompting a fake “phone number check.” Any input is accepted to proceed, leading the victim further into the phishing scheme.
2. CAPTCHA Verification: The victim is redirected to a CAPTCHA page utilizing Cloudflare Turnstile, designed to filter out bots and ensure human interaction.
3. Fake Login Page: Subsequently, a counterfeit Microsoft 365 login page is presented. In the background, the system verifies emails using JSON data, including session keys and redirects.
4. Credential Harvesting: Upon entering credentials, obfuscated JavaScript exfiltrates the data to /api/login, including expired JWT tokens to enhance authenticity.
5. Server Responses: The server’s response dictates the next steps:
– Success: Renders benign HTML to mask the credential theft.
– Error: Displays “incorrect password” prompts to encourage re-entry of credentials.
– Info Status: Triggers logging to /x.php.
This adversary-in-the-middle (AitM) setup effectively bypasses basic Multi-Factor Authentication (MFA), capturing emails, passwords, and tokens in JSON format.
Targeted Sectors and Geographical Reach
Tykit’s campaigns have impacted a diverse range of sectors, including construction, information technology, finance, government, telecommunications, real estate, and education. The geographical reach is extensive, affecting regions such as the United States, Canada, Latin America, Europe, the Middle East, Southeast Asia, and others.
The consequences of such compromises are severe, enabling account takeovers, data exfiltration from Software as a Service (SaaS) applications, and lateral movement within networks. These breaches can lead to regulatory fines and erosion of trust among clients and partners.
Mitigation Strategies
To counteract the threats posed by Tykit, organizations are advised to implement the following measures:
– Inspection of SVG Content: Utilize sandboxing and content disarmament techniques to scrutinize SVG files for embedded malicious code.
– Adoption of Phishing-Resistant MFA: Implement Multi-Factor Authentication methods that are resistant to phishing, such as FIDO2 standards, to enhance security.
– Monitoring Indicators of Compromise (IOCs): Keep an eye on specific IOCs, including eval() calls, Base64 parameters, and suspicious domain patterns, to detect potential threats early.
– SIEM Rules Implementation: Develop Security Information and Event Management (SIEM) rules to detect patterns like /api/validate requests, aiding in the early disruption of phishing campaigns.
– User Training: Educate users about the risks associated with anomalous “image” files and the importance of verifying the authenticity of login pages.
As phishing tactics continue to evolve, the emergence of Tykit underscores the necessity for proactive threat hunting and the adoption of advanced security measures to stay ahead of these sophisticated attacks.