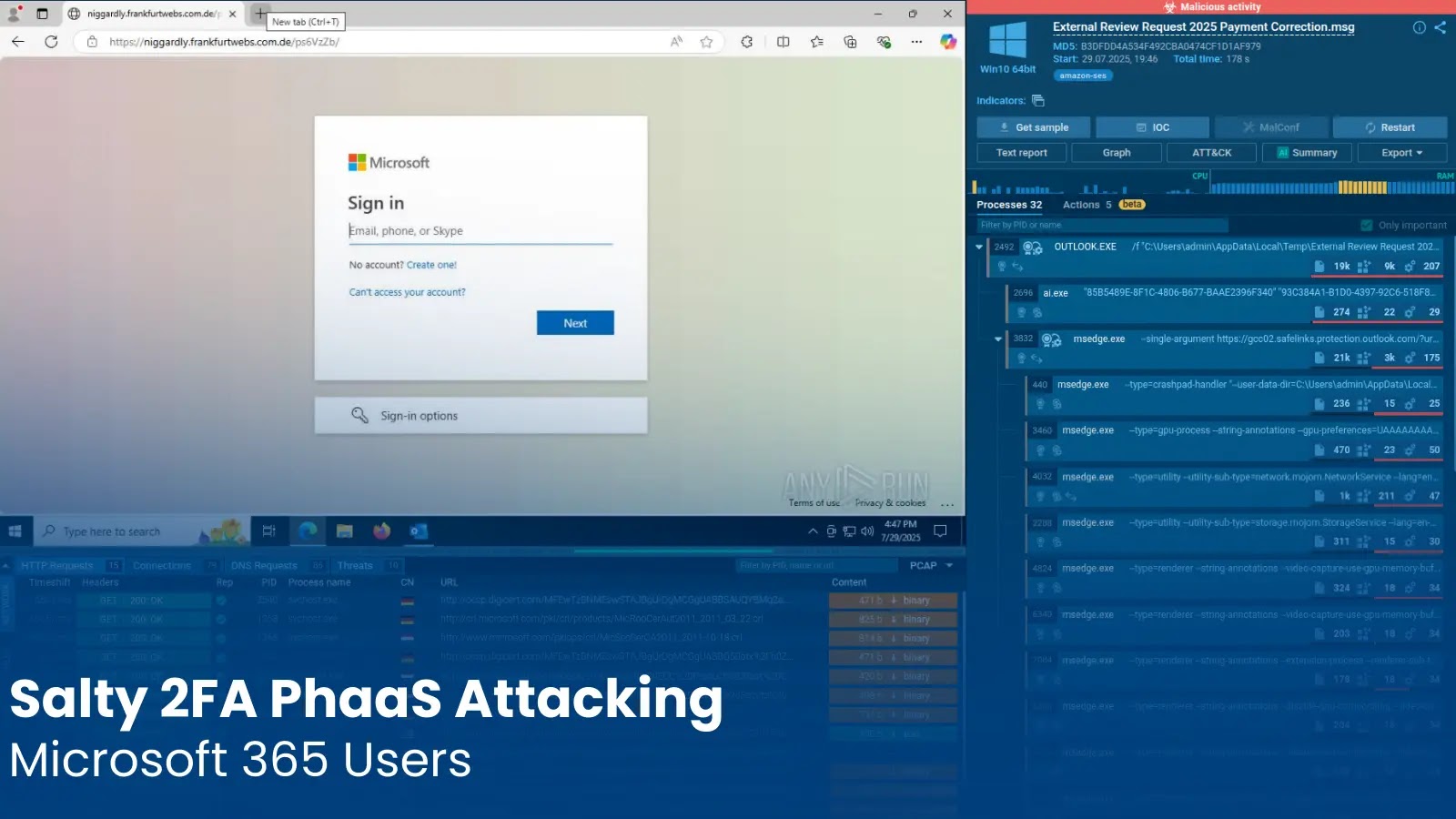
A newly identified Phishing-as-a-Service (PhaaS) platform, dubbed Salty 2FA, has surfaced as a significant cybersecurity threat, particularly targeting Microsoft 365 users across various industries in the United States and Europe. This advanced platform employs intricate obfuscation techniques and multi-stage execution processes specifically designed to circumvent two-factor authentication (2FA) mechanisms, thereby facilitating the theft of corporate credentials.
Targeted Sectors and Attack Vectors
Salty 2FA’s reach extends across multiple sectors, including finance, telecommunications, energy, logistics, and education. The platform orchestrates meticulously crafted phishing campaigns that deceive recipients into divulging sensitive information. These campaigns often utilize deceptive emails containing lures such as fake voice messages, document access requests, and billing statements. Unsuspecting victims who interact with these emails are redirected to convincingly replicated Microsoft login pages, where their credentials are harvested.
Unique Domain Infrastructure and Evasion Techniques
One of the distinguishing features of Salty 2FA is its unique domain infrastructure. The platform combines compound domains in .com zones with domains registered under the Russian .ru top-level domain. This strategic pairing creates a complex web of redirections and payload delivery mechanisms, effectively evading traditional detection systems. For instance, domains like innovationsteams[.]com and marketplace24ei[.]ru are utilized in tandem to obfuscate the attack’s origin and intent.
Discovery and Analysis
The Salty 2FA framework was identified by analysts at ANY.RUN during routine monitoring of phishing campaigns. They observed multiple sandbox sessions exhibiting similar behavioral patterns, despite variations in domains and obfuscation techniques. A consistent use of Cloudflare Turnstile protection, combined with the distinctive domain pairing, prompted a comprehensive analysis that unveiled the full capabilities of Salty 2FA.
Advanced 2FA Interception Capabilities
Salty 2FA demonstrates a high level of sophistication in intercepting and processing various two-factor authentication methods. These include push notifications, SMS codes, voice calls, and authenticator app tokens. By effectively bypassing these security measures, the platform enables threat actors to maintain persistent access to compromised accounts, even when traditional 2FA protections are in place.
Multi-Stage Execution Chain and Obfuscation Techniques
The technical architecture of Salty 2FA relies on a meticulously orchestrated five-stage execution process designed to resist analysis and detection:
1. Initial Stage: An obfuscated JavaScript function serves as the entry point, containing comments with inspirational quotes to complicate static analysis.
2. Element ID Encoding: The framework employs sophisticated encoding of element IDs using Base64 and XOR operations with a fixed generated value, making dynamic analysis significantly more challenging.
3. Dynamic Element Identification: All front-end logic relies on jQuery calls to dynamically generated element identifiers, which must be decoded through a dedicated routine before manipulation.
4. Anti-Analysis Mechanisms: The platform incorporates multiple anti-analysis mechanisms, including blocking keyboard shortcuts for debugging tools and measuring execution time to detect controlled environments.
5. Data Exfiltration: Stolen credentials are transmitted to Russian-hosted servers through encoded POST requests containing both the encrypted data and decoding parameters.
Indicators of Compromise (IoCs)
Security professionals should be vigilant for the following indicators associated with Salty 2FA:
– Domains:
– innovationsteams[.]com
– marketplace24ei[.]ru
– nexttradeitaly[.]it[.]com
– frankfurtwebs[.]com[.]de
– URLs:
– hxxps[://]telephony[.]nexttradeitaly[.]com/SSSuWBTmYwu/
– hxxps[://]parochially[.]frankfurtwebs[.]com[.]de/ps6VzZb/
Mitigation Strategies
To defend against threats like Salty 2FA, organizations should implement a multi-layered security approach:
– Enhanced Email Filtering: Deploy advanced email filtering solutions to detect and block phishing emails before they reach end-users.
– User Education: Conduct regular training sessions to educate employees about recognizing phishing attempts and the importance of not interacting with suspicious emails or links.
– Behavioral-Based Detection Systems: Utilize security systems that analyze user behavior to detect anomalies indicative of compromised accounts.
– Phishing-Resistant MFA Methods: Implement multi-factor authentication methods that are resistant to phishing, such as hardware tokens or biometric verification.
By adopting these strategies, organizations can enhance their resilience against sophisticated phishing attacks and protect sensitive corporate information from unauthorized access.