A recently developed tool named EDR-Redir has surfaced, enabling attackers to manipulate the executable directories of prominent Endpoint Detection and Response (EDR) systems. This technique, demonstrated by cybersecurity researcher TwoSevenOneT, exploits Windows’ Bind Filter driver (bindflt.sys) and Cloud Filter driver (cldflt.sys) to compromise EDR protections without necessitating kernel-level access.
This user-mode exploit, rooted in the Bring Your Own Vulnerable Driver (BYOVD) approach, allows attackers to disable defenses, inject malicious code, or hijack processes, thereby leaving systems susceptible to undetected intrusions.
Understanding the Vulnerability
The vulnerability originates from Windows 11’s Bind Link feature, introduced in version 24H2. Bind Links offer filesystem namespace redirection via virtual paths, managed by the bindflt.sys minifilter driver. Unlike traditional symbolic links, which EDRs actively monitor and block using mechanisms like Microsoft’s RedirectionGuard, Bind Links operate transparently at the driver level. They map virtual paths to real ones, local or remote, without creating physical files, inheriting permissions from the target while remaining invisible to most applications.
This subtlety allows attackers with administrator privileges to perform read and open operations on protected EDR folders, which are typically locked against writes.
EDR-Redir in Action
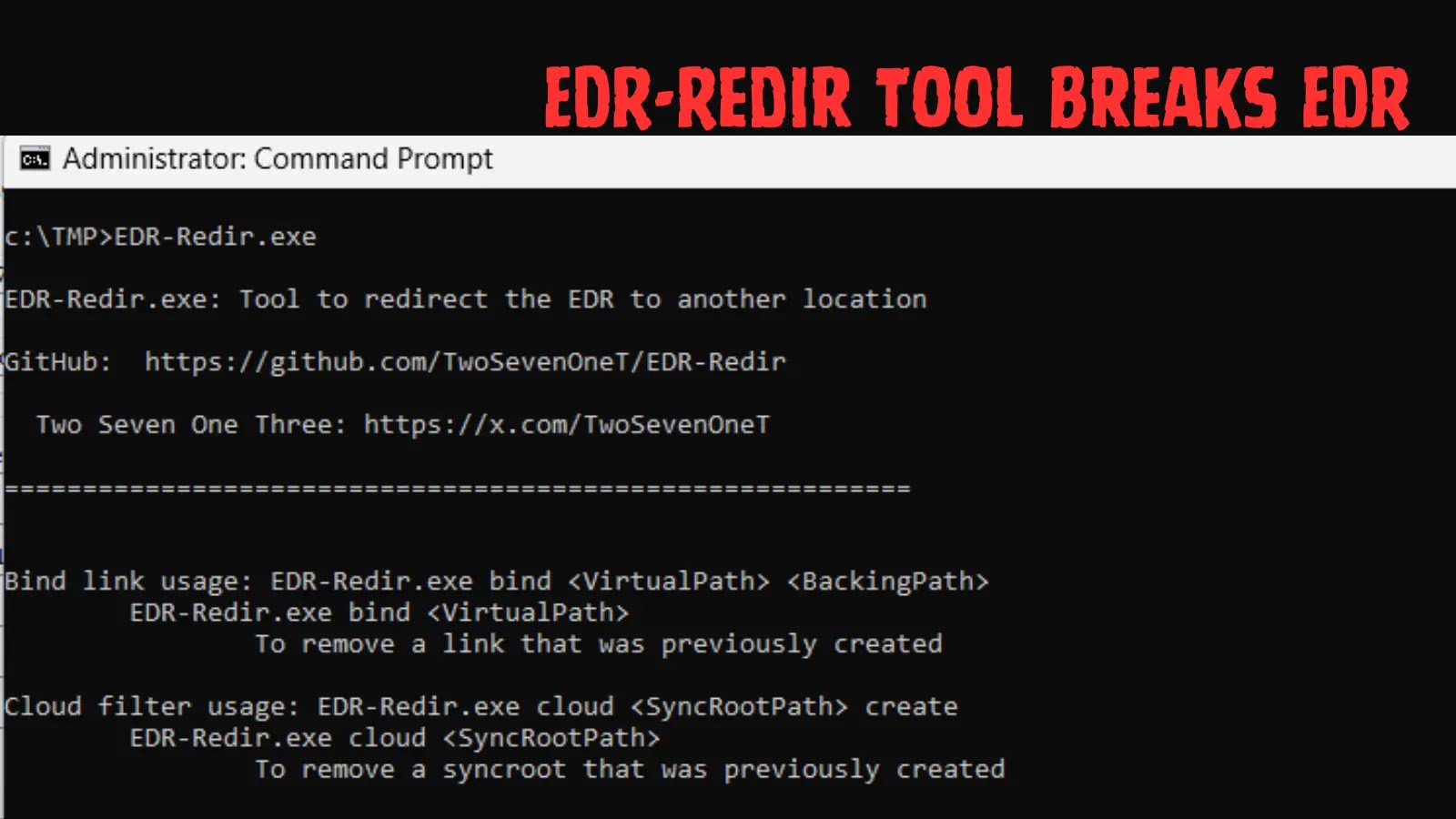
EDR-Redir, available as an open-source tool on GitHub, simplifies the process with straightforward commands. For instance, executing EDR-Redir.exe bind C:\TMP\123 C:\TMP\456 creates a virtual path at C:\TMP\123 that redirects all interactions to C:\TMP\456.
The researcher tested this against multiple EDRs. With Elastic Defend and Sophos Intercept X, the tool successfully redirected their executable folders to attacker-controlled locations.
Once redirected, adversaries could drop DLLs for process hijacking, insert malicious executables, or empty the folder to halt EDR operations on reboot. Notably, these Bind Links do not persist across restarts, requiring a scheduled task or service for automation.
Bypassing Windows Defender with Cloud Filter Techniques
Windows Defender proved more resilient to direct Bind Link redirection, likely due to its integrated protections. However, the researcher devised a workaround using the Cloud Files API (CFAPI), powered by cldflt.sys.
This API, designed for sync engines like OneDrive, enables on-demand file access through placeholder files. By invoking CfRegisterSyncRoot with minimal policies—essentially an incomplete registration—EDR-Redir registers the Defender folder as a sync root.
This corrupts access, preventing the EDR from reading or writing to its directory. Post-reboot, Defender’s services fail to start, effectively isolating it.
Unlike Bind Links, this Cloud Filter method persists without additional setup, making it particularly stealthy. A demo video shared by the researcher illustrates the process, showing Defender’s folder becoming inaccessible after registration.
Tests confirmed similar efficacy against two unnamed commercial EDRs, highlighting a broad risk.
Implications and Recommendations
This technique underscores a growing challenge: EDRs must evolve beyond user-mode symlink defenses to scrutinize minifilter interactions. Attackers gain full control over EDR behaviors, potentially evading detection in red-team exercises or real breaches.
Organizations should audit administrator privileges, monitor for unusual driver loads, and apply Windows patches promptly. Vendors like Microsoft, Elastic, and Sophos are urged to enhance folder protections against these API abuses.
As endpoint threats intensify, tools like EDR-Redir remind us that even robust defenses can falter on overlooked filesystem features.