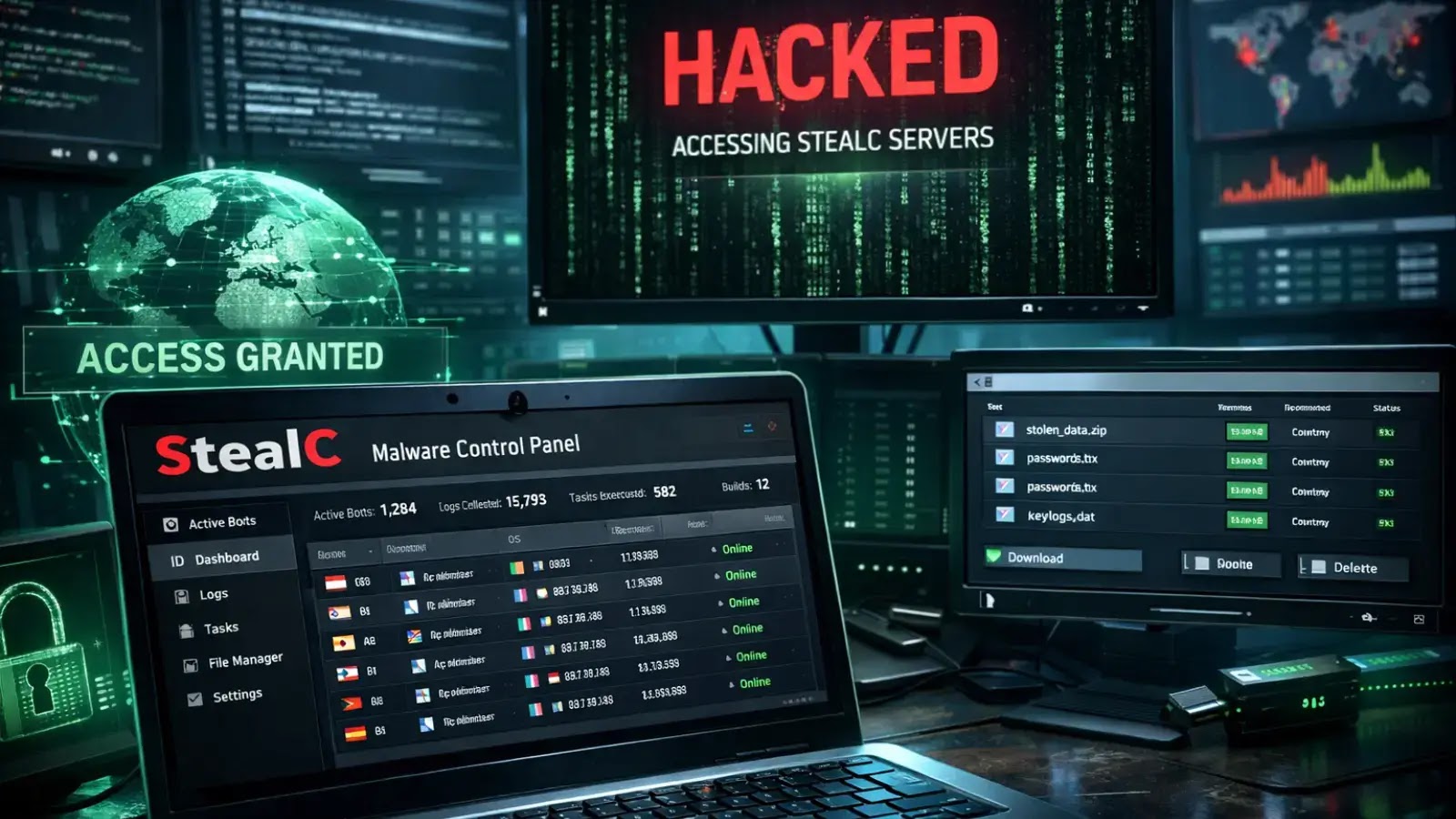
Researchers Infiltrate StealC Malware’s Command-and-Control Systems, Unmasking Operator Identity
In a significant breakthrough, cybersecurity experts have successfully penetrated the command-and-control (C2) infrastructure of StealC, a notorious information-stealing malware. This operation not only exposed critical vulnerabilities within the malware’s framework but also led to the identification of a key threat actor behind its distribution.
Unveiling StealC’s Infrastructure Weaknesses
StealC has been a prominent player in the cybercrime landscape since its emergence in early 2023. Operating under a Malware-as-a-Service (MaaS) model, it has facilitated numerous credential theft campaigns. However, a pivotal moment occurred in the spring of 2025 when a code leak revealed a cross-site scripting (XSS) vulnerability within StealC’s web panel.
CyberArk Labs, leveraging this vulnerability, embarked on an in-depth analysis of StealC’s operations. By exploiting the XSS flaw, researchers were able to gather system fingerprints, monitor active sessions, and crucially, capture authentication cookies from the very infrastructure designed to steal them. This ironic twist underscored a glaring oversight: the operators, adept at cookie theft, had neglected to implement fundamental security measures, such as the httpOnly flag, which would have safeguarded against such XSS attacks.
Tracing the Footsteps of YouTubeTA
The investigation led to the identification of a singular operator, designated YouTubeTA (YouTube Threat Actor). This individual maintained an extensive database comprising over 5,000 infection logs, which included a staggering 390,000 stolen passwords and 30 million cookies.
Further analysis of the stolen data revealed that victims were often individuals searching for cracked versions of popular software like Adobe Photoshop and After Effects on YouTube. This pattern suggested that YouTubeTA had compromised legitimate YouTube channels with substantial subscriber bases to disseminate StealC malware.
The operator’s web panel configuration was meticulously crafted, with specific markers targeting studio.youtube.com credentials. This strategy indicated a deliberate attempt to hijack content creator accounts, thereby expanding the malware’s distribution network through trusted channels.
Operational Security Lapses and Geolocation Insights
Through panel fingerprinting techniques, researchers determined that YouTubeTA operated from a system equipped with an Apple M3 processor. Consistent hardware signatures across all sessions pointed to a single operator. Language preferences set to English and Russian, coupled with a timezone setting of GMT+0300 (Eastern European Summer Time), provided further context to the operator’s background.
A critical operational security lapse occurred when the operator momentarily connected without the protection of a Virtual Private Network (VPN). This oversight exposed an IP address linked to a Ukrainian Internet Service Provider (ISP), TRK Cable TV. Such a revelation underscores the inherent risks and potential for exposure that threat actors face, even when they believe their operations are concealed.
Broader Implications for Malware-as-a-Service Operations
This breach into StealC’s infrastructure serves as a stark reminder of the vulnerabilities that can exist within criminal enterprises. The exploitation of the XSS flaw not only compromised the malware’s operations but also highlighted the paradox of cybercriminals falling victim to the very tactics they employ.
The incident also sheds light on the evolving landscape of Malware-as-a-Service platforms. While these platforms offer scalability and anonymity to cybercriminals, they are not immune to security flaws. The exposure of YouTubeTA’s identity and operational methods provides valuable intelligence for cybersecurity professionals and law enforcement agencies aiming to dismantle such networks.
The Role of Social Engineering in Malware Distribution
The case of YouTubeTA underscores the effectiveness of social engineering tactics in malware distribution. By compromising legitimate YouTube channels, the operator was able to exploit the trust established between content creators and their audiences. This method of distribution is particularly insidious, as it leverages the credibility of well-known platforms to propagate malicious software.
Users seeking free or cracked versions of software are often lured into downloading malware-laden files, believing them to be legitimate. This highlights the critical need for user education on the risks associated with downloading software from unverified sources and the importance of maintaining updated security measures.
Technical Insights into StealC’s Operations
StealC’s infrastructure was designed with a focus on efficiency and scalability. The web panel allowed operators to manage infections, view stolen data, and configure malware builds with relative ease. However, the presence of the XSS vulnerability indicates a lack of rigorous security practices in the development of the malware’s backend systems.
The malware’s ability to capture extensive amounts of data, including passwords and cookies, poses significant risks to individuals and organizations alike. Stolen credentials can be used for a variety of malicious purposes, including identity theft, financial fraud, and further propagation of malware.
Conclusion
The successful infiltration of StealC’s command-and-control systems marks a significant victory for cybersecurity researchers. It not only disrupts the operations of a prolific malware but also serves as a cautionary tale for cybercriminals about the importance of securing their own infrastructures.
For the broader cybersecurity community, this incident emphasizes the need for continuous vigilance, the importance of identifying and exploiting vulnerabilities within malicious networks, and the value of collaboration in the fight against cybercrime.