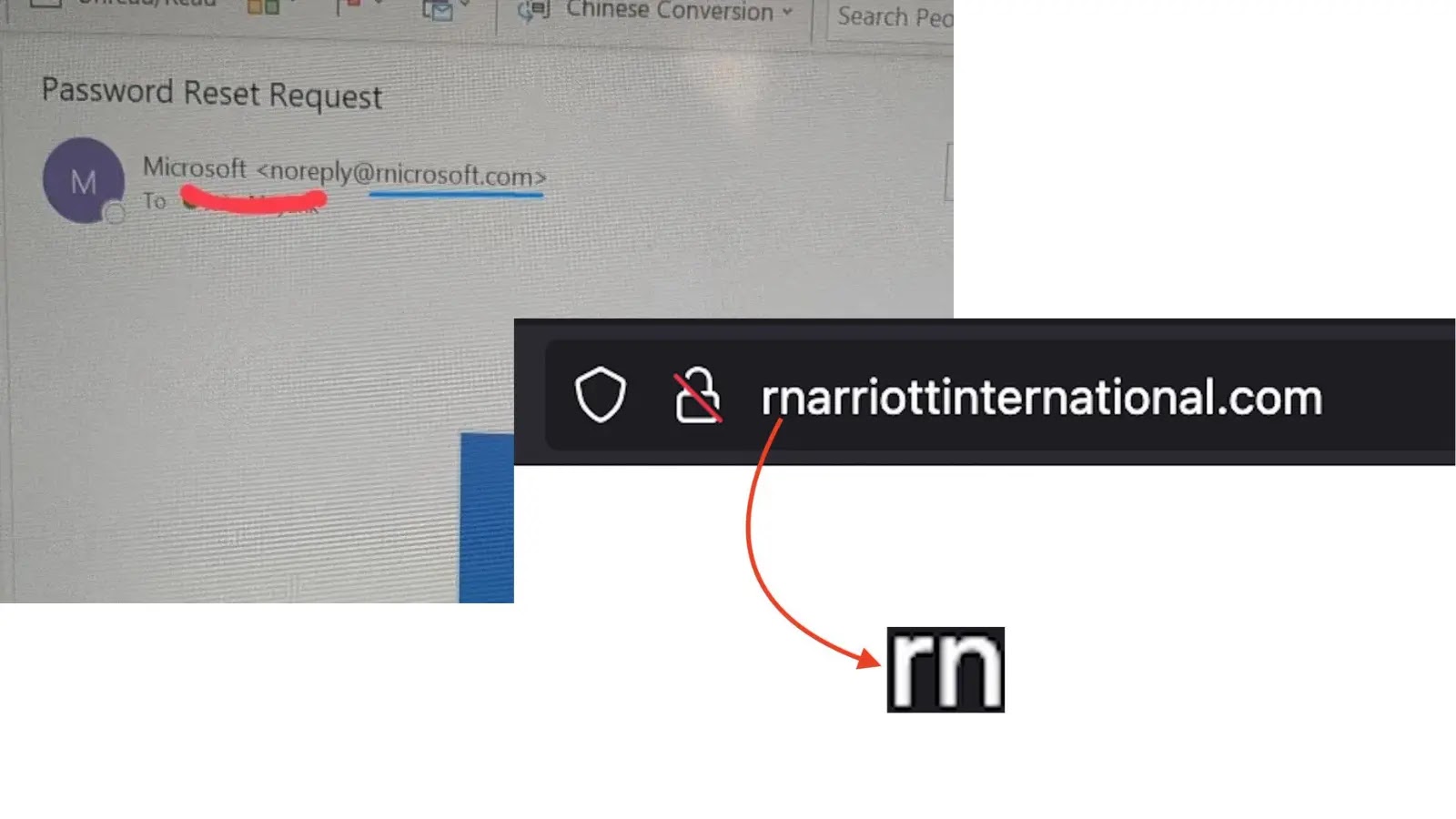
Cybercriminals Exploit ‘rn’ Typo to Mimic Microsoft and Marriott in Sophisticated Phishing Attacks
In a recent wave of cyberattacks, malicious actors have employed a deceptive technique known as typosquatting to impersonate reputable companies like Microsoft and Marriott International. By substituting the letter ‘m’ with the combination ‘r’ and ‘n’ (‘rn’), they create counterfeit domains that closely resemble legitimate ones, thereby tricking users into divulging sensitive information.
Understanding the ‘rn’ Typo Technique
Typosquatting, or domain mimicry, involves registering domain names that are visually similar to those of well-known organizations. In this case, attackers exploit the visual similarity between ‘rn’ and ‘m’ in certain fonts, making domains like ‘rnicrosoft.com’ appear nearly identical to ‘microsoft.com’. This subtle alteration can easily go unnoticed, especially when users are quickly scanning URLs.
Recent Phishing Campaigns Targeting Major Corporations
Security researchers have identified several phishing campaigns utilizing this ‘rn’ substitution:
– Marriott International Impersonation: Attackers registered domains such as ‘rnarriottinternational.com’ and ‘rnarriotthotels.com’ to mimic Marriott’s official websites. Unsuspecting users visiting these sites may be prompted to enter personal information, which is then harvested by cybercriminals.
– Microsoft User Deception: Similarly, domains like ‘rnicrosoft.com’ have been used to send fraudulent emails that appear to originate from Microsoft. These emails often contain fake security alerts or invoice notifications, urging recipients to click on malicious links or provide login credentials.
Indicators of Compromise (IOCs)
To aid in the identification and mitigation of these threats, the following malicious domains have been flagged:
– `rnarriottinternational.com`
– `rnarriotthotels.com`
– `rnicrosoft.com`
– `micros0ft.com` (where ‘o’ is replaced with ‘0’)
– `microsoft-support.com`
Security teams are advised to block these domains and remain vigilant for similar typosquatting attempts.
Protective Measures Against Typosquatting Attacks
To safeguard against such deceptive tactics, consider implementing the following strategies:
1. Verify Sender Details: On mobile devices, tap the sender’s name to reveal the full email address. Look closely for subtle typos or unusual characters.
2. Hover Over Links: On desktops, hover your mouse over hyperlinks without clicking to preview the actual URL destination.
3. Manually Enter URLs: Instead of clicking on links in unsolicited emails, type the known, official website address directly into your browser.
4. Utilize Password Managers: These tools can detect and prevent auto-filling credentials on unrecognized or suspicious websites.
The Broader Implications of Homoglyph Attacks
The ‘rn’ substitution is part of a broader category of homoglyph attacks, where characters from different scripts or similar-looking character combinations are used to create deceptive domain names. Other examples include replacing ‘o’ with ‘0’ (zero) or adding hyphens to legitimate brand names. These tactics exploit the nuances of human visual perception and the rendering of characters in various fonts and devices.
The Role of Font Rendering in Deception
The effectiveness of these attacks is amplified by the way fonts render characters. In many typefaces, the combination of ‘r’ and ‘n’ can appear indistinguishable from ‘m’, especially in sans-serif fonts commonly used in digital interfaces. This visual similarity can lead users to misinterpret malicious domains as legitimate ones.
Case Study: Mobile Device Vulnerability
The risk is heightened on mobile devices due to smaller screen sizes and truncated URL displays. For instance, a user receiving an email on their smartphone may see ‘rnicrosoft.com’ in the address bar, which, at a glance, appears identical to ‘microsoft.com’. This makes it easier for attackers to deceive users into clicking malicious links or providing sensitive information.
Historical Context and Evolution of Typosquatting
Typosquatting is not a new phenomenon. Cybercriminals have long registered misspelled versions of popular domains to capture traffic from users who mistype URLs. However, the use of homoglyphs like ‘rn’ for ‘m’ represents an evolution in these tactics, leveraging typographic nuances to enhance the deception.
The Importance of User Education and Awareness
Educating users about these tactics is crucial. Regular training sessions can help individuals recognize suspicious emails and URLs. Encouraging a culture of skepticism and verification can significantly reduce the success rate of such phishing attempts.
Technological Solutions and Email Filtering
Implementing advanced email filtering solutions that can detect and block emails from typosquatted domains is essential. These systems can analyze incoming emails for known indicators of phishing and prevent them from reaching end-users.
Collaboration Between Organizations and Security Firms
Organizations should collaborate with cybersecurity firms to stay updated on emerging threats. Sharing information about new phishing tactics and compromised domains can help in developing more effective defense strategies.
Conclusion
The use of ‘rn’ in place of ‘m’ in domain names is a sophisticated phishing tactic that exploits human visual perception and typographic rendering. By understanding these methods and implementing robust security measures, both individuals and organizations can better protect themselves against such deceptive attacks.