Cybercriminals Exploit Malicious Ads to Deploy OysterLoader Malware via PuTTY and Microsoft Teams
A sophisticated cyberattack campaign is currently underway, leveraging malicious advertisements to distribute a potent malware known as OysterLoader. This malware, previously identified as Broomstick and CleanUpLoader, serves as an initial access tool for cybercriminals, facilitating unauthorized entry into corporate networks. The ultimate objective of these intrusions is often the deployment of the notorious Rhysida ransomware, which has been targeting enterprises since its emergence from the Vice Society group in 2021 and subsequent rebranding in 2023.
Evolution of Rhysida’s Tactics
The operators behind Rhysida have refined their methods over time, with the current campaign representing their second major malvertising operation. Building upon tactics that proved successful between May and September 2024, these threat actors have, since June 2025, intensified their efforts, expanding both the scale and sophistication of their attacks.
Malvertising Strategy
Central to this campaign is the strategic purchase of advertisements on Bing’s search engine. These ads are designed to appear prominently in search results, including within the Windows 11 start menu searches, thereby increasing the likelihood of user engagement. By impersonating popular software applications such as Microsoft Teams, PuTTY, and Zoom, the attackers create nearly identical fake download pages that deceive users into downloading malicious software.
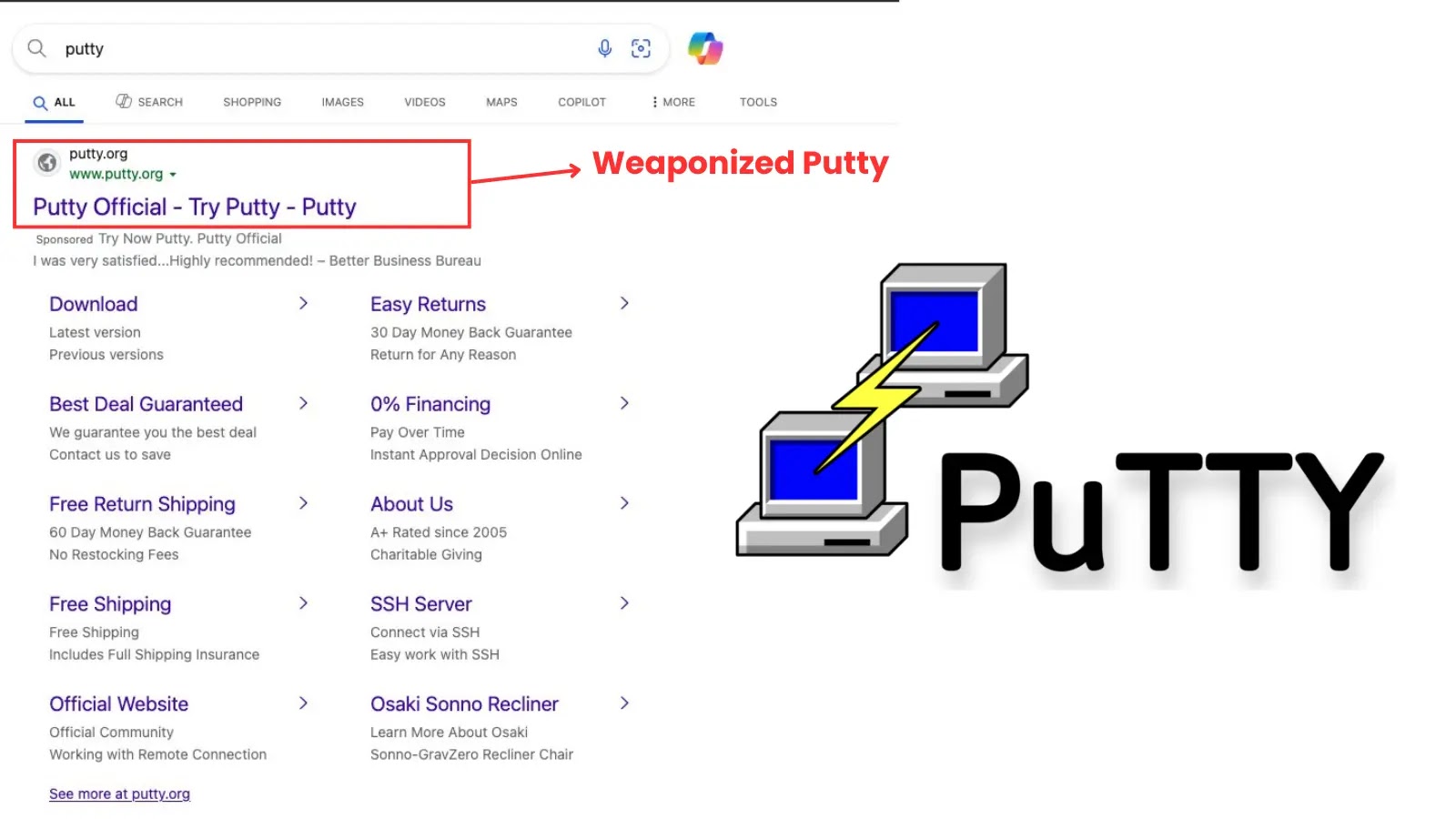
Case Study: Malicious PuTTY Advertisements
A notable example of this tactic involves the use of sponsored results that intentionally misspell PuTTY as Putty. Despite the subtle misspelling, these ads appear legitimate enough to mislead users seeking the authentic remote access tool. Upon clicking these ads, users are redirected to malicious landing pages where they inadvertently download the compromised software.
OysterLoader’s Evasion Techniques
OysterLoader’s effectiveness is largely attributed to two primary evasion techniques:
1. Obfuscation and Compression: The malware is packed through compression and obfuscation methods, concealing its true capabilities from security tools. This results in remarkably low initial detection rates, with fewer than five antivirus engines typically flagging new samples.
2. Code-Signing Certificates: Attackers employ code-signing certificates to exploit Windows trust mechanisms, making the malware appear legitimate. The scale of this operation is evident in certificate usage; while the 2024 campaign utilized seven certificates, the current 2025 campaign has burned through over 40 unique code-signing certificates, indicating substantial resource investment and operational commitment.
Additional Malware Deployment
Rhysida’s operations are not limited to OysterLoader. Researchers have discovered the gang simultaneously deploying Latrodectus malware, confirmed when identical code-signing certificates appeared on both malware families. Additionally, Rhysida has exploited Microsoft’s Trusted Signing service, circumventing its 72-hour certificate validity restrictions. Microsoft reports revoking over 200 certificates associated with this campaign, yet operations remain active.
Recommendations for Security Teams
Given the sophistication and persistence of these malvertising campaigns, security teams are advised to:
– Remain Vigilant: Continuously monitor for signs of malvertising campaigns and unauthorized software downloads.
– Verify Software Sources: Ensure that all software downloads are conducted exclusively through official channels to avoid compromise.
– Educate Users: Provide training to users on recognizing and avoiding malicious advertisements and phishing attempts.
– Implement Advanced Security Measures: Utilize advanced endpoint protection and network monitoring tools to detect and respond to suspicious activities promptly.
By adopting these proactive measures, organizations can enhance their defenses against the evolving tactics of cybercriminals and protect their networks from potential breaches.