JackFix: Cybercriminals Exploit Fake Windows Updates on Adult Sites to Deploy Stealer Malware
Cybersecurity experts have recently uncovered a sophisticated campaign, dubbed JackFix, that employs deceptive tactics to trick users into executing malicious commands under the guise of critical Windows security updates. This operation primarily targets visitors to counterfeit adult websites, leveraging psychological manipulation to increase compliance.
The Mechanics of the JackFix Campaign
The JackFix campaign utilizes a combination of ClickFix lures and fraudulent adult websites to deceive users. ClickFix attacks have surged over the past year, accounting for 47% of initial access methods, according to Microsoft data. These attacks typically involve prompts for technical fixes or CAPTCHA verifications that lead users to execute harmful commands on their own systems.
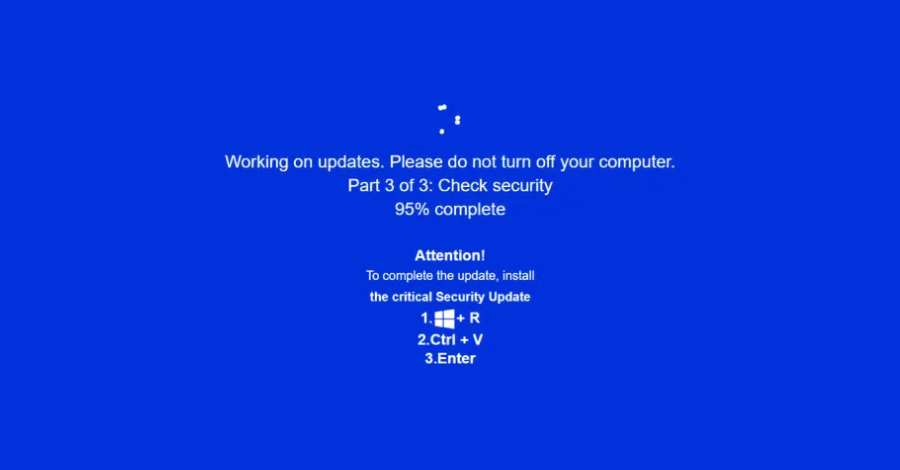
In this campaign, users are redirected to fake adult sites through malvertising or other social engineering methods. Once on these sites, they encounter a convincing Windows update screen that hijacks the entire display. This screen instructs users to open the Windows Run dialog, paste a provided command, and press Enter, thereby initiating the infection sequence.
Technical Execution and Obfuscation Techniques
The fraudulent Windows update alert is crafted entirely using HTML and JavaScript, designed to mimic the infamous blue screen of death. Upon any interaction with the phishing site, this alert appears, urging immediate action. To prevent users from exiting the full-screen alert, the attackers disable the Escape and F11 keys, along with F5 and F12. However, due to flawed logic, users can still use the Escape and F11 keys to exit full-screen mode.
The initial command executed is an MSHTA payload launched via the legitimate mshta.exe binary. This payload contains JavaScript designed to run a PowerShell command that retrieves another PowerShell script from a remote server. Notably, these domains are configured to redirect users to benign sites like Google or Steam when accessed directly, adding a layer of obfuscation. Only when accessed through specific PowerShell commands do they deliver the malicious code.
Privilege Escalation and Payload Deployment
The downloaded PowerShell script employs various obfuscation and anti-analysis techniques, including the insertion of garbage code to complicate analysis. It attempts to elevate privileges by continuously prompting the user for administrative rights until granted. Once successful, the script creates exclusions in Microsoft Defender Antivirus for command-and-control (C2) addresses and paths where the payloads are staged.
Subsequently, the script drops additional payloads, such as simple remote access trojans (RATs) programmed to contact a C2 server, potentially to deploy more malware. The PowerShell script has been observed serving up to eight different payloads, including Rhadamanthys Stealer, Vidar Stealer 2.0, RedLine Stealer, and Amadey, among others. This spray and pray approach increases the likelihood of successful infection, risking the loss of passwords, cryptocurrency wallets, and more.
Broader Implications and Related Campaigns
The JackFix campaign is part of a broader trend where cybercriminals exploit social engineering tactics to deceive users into executing malicious commands. Similar campaigns have been observed, such as the use of fake CAPTCHA checks leading to the deployment of Lumma Stealer and Amadey Trojan. These campaigns often involve compromised websites serving fake update notifications or CAPTCHA verifications to trick users into executing harmful commands.
Another related campaign involves the use of fake Zoom pages in the GhostCall campaign, where victims are prompted to download a malicious AppleScript file or execute a PowerShell command under the pretense of updating a Zoom SDK. These tactics highlight the evolving nature of social engineering attacks and the importance of user vigilance.
Mitigation Strategies and Recommendations
To defend against such attacks, organizations and individuals should implement the following strategies:
1. User Education and Awareness: Regularly train employees and users to recognize social engineering tactics, such as fake update prompts and deceptive websites.
2. Restrict Administrative Privileges: Limit the use of administrative accounts and privileges to reduce the risk of unauthorized changes to systems.
3. Implement Technical Controls: Disable the Windows Run box via Registry changes or Group Policy to prevent users from executing arbitrary commands.
4. Regular Software Updates: Ensure that all software and systems are up to date with the latest security patches to mitigate vulnerabilities.
5. Deploy Advanced Threat Detection: Utilize endpoint detection and response (EDR) solutions to monitor and respond to suspicious activities.
By adopting these measures, organizations can enhance their security posture and reduce the risk of falling victim to sophisticated social engineering attacks like JackFix.