Cybercriminals Exploit Fake BSODs and Trusted Tools to Deploy DCRat
A sophisticated cyberattack campaign, identified as PHALT#BLYX, has been targeting the hospitality sector by exploiting fake Blue Screen of Death (BSOD) warnings and trusted Microsoft build tools to deploy the DCRat remote access trojan.
Deceptive Phishing Tactics
The attack initiates with phishing emails masquerading as reservation alerts from Booking.com. These emails present alarming charges exceeding €1,000, prompting recipients to click on a See Details link. This link redirects victims to counterfeit websites that closely mimic the authentic Booking.com interface, complete with matching colors, fonts, and logos. This psychological manipulation leverages urgency and financial concern, increasing the likelihood of victims bypassing standard security protocols.
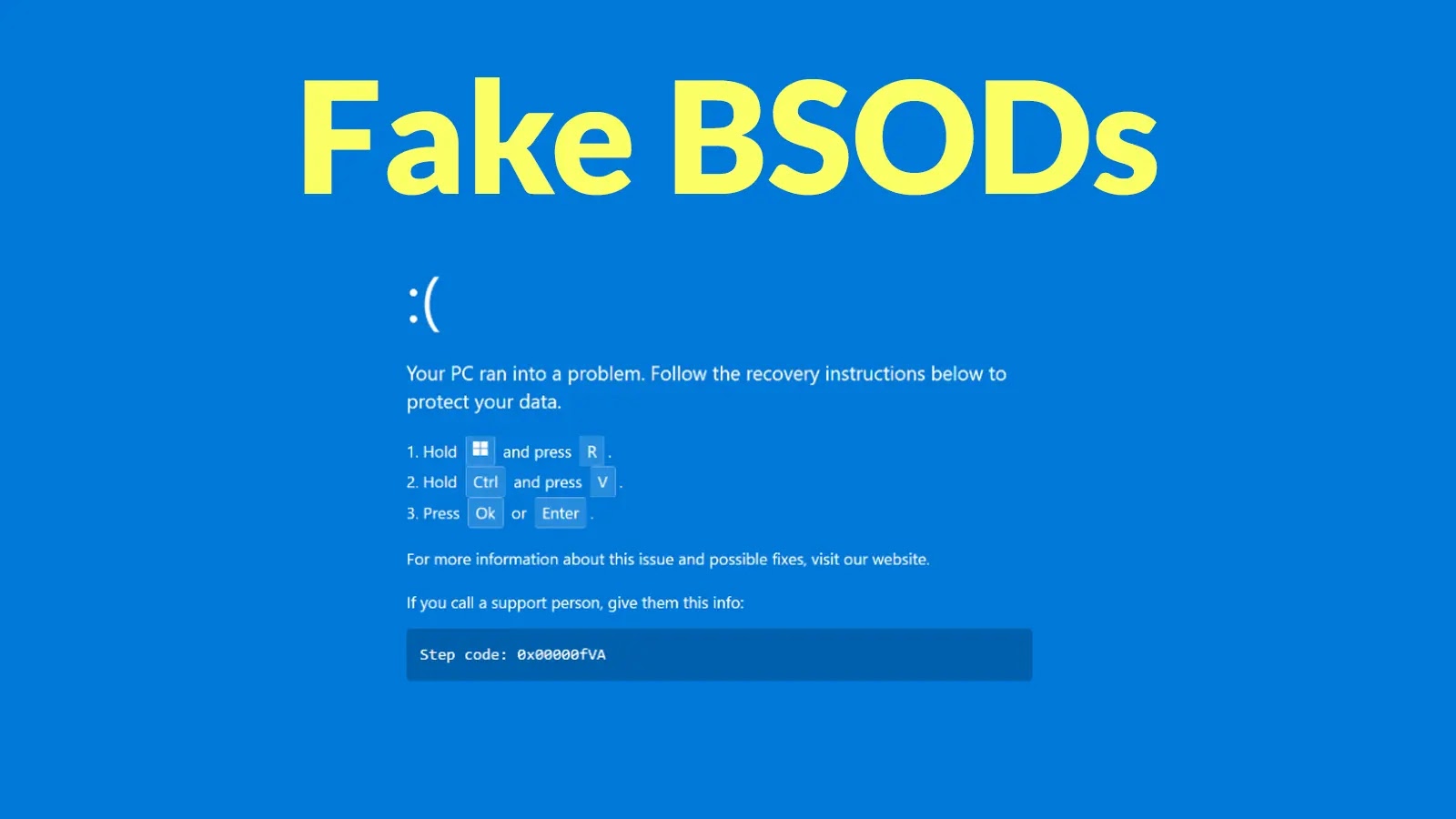
Fake BSOD and ClickFix Technique
Upon visiting the fraudulent site, victims encounter a simulated browser loading error followed by a fake BSOD that appears convincingly real. The page instructs users to fix the issue by pressing the Windows key + R, pasting clipboard content, and pressing Enter. This method, known as the ClickFix technique, deceives users into manually executing PowerShell commands that download malicious project files and launch them via MSBuild.exe, a legitimate Microsoft compilation tool.
Living off the Land Techniques
Securonix researchers have observed an evolution in the attackers’ tactics, transitioning from simpler HTML application delivery methods to more sophisticated MSBuild-based infection chains. This shift signifies a strategic move towards Living off the Land techniques, which exploit trusted system utilities to evade traditional antivirus detection. Analysis of the malware code revealed Russian language strings, suggesting connections to Russian-speaking threat groups known for using DCRat in underground forums.
Multi-Stage Infection Process and Defense Evasion
The malicious PowerShell dropper performs several operations simultaneously:
– Opens the legitimate Booking.com admin page as a decoy.
– Searches the system for MSBuild.exe.
– Downloads a project file named v.proj from attacker-controlled infrastructure.
– Launches the project file through MSBuild.exe.
Since MSBuild.exe carries a valid Microsoft signature, application whitelisting and endpoint security solutions often fail to flag its execution as suspicious.
The v.proj file contains embedded PowerShell scripts that target Windows Defender by adding exclusions for the entire ProgramData directory and specific file extensions, including .exe, .ps1, and .proj. This preparation ensures the final payload can land on disk without triggering quarantine alerts.
The malware then attempts privilege escalation through User Account Control (UAC) spam tactics, repeatedly prompting users to grant administrator rights via repetitive pop-ups designed to wear down their resistance.
Deployment of DCRat
After establishing persistence through Internet Shortcut files in the Startup folder, the malware deploys staxs.exe, a heavily obfuscated variant of DCRat. This payload uses AES-256 encryption with PBKDF2 key derivation and connects to command-and-control servers at asj77.com, asj88.com, and asj99.com over port 3535. The trojan injects itself into legitimate system processes like aspnet_compiler.exe through process hollowing, effectively masking malicious activity behind trusted Windows binaries.
Capabilities of DCRat
DCRat possesses a range of capabilities, including:
– Keylogging.
– Remote desktop access.
– Process injection.
– Downloading secondary payloads such as cryptocurrency miners.
The malware collects comprehensive system fingerprints, including hardware identifiers, installed antivirus software, active window titles, and domain membership status, before sending this intelligence back to its operators. This information enables attackers to assess victim value and deploy appropriate follow-on tools for credential theft, lateral movement, or ransomware deployment.