Cybercriminals Exploit DNS TXT Records in ClickFix Attacks to Deploy Malware
In the ever-evolving landscape of cyber threats, the KongTuke campaign has emerged as a formidable adversary, continuously refining its tactics to circumvent traditional security measures. Active since mid-2025, this threat actor group has notably enhanced its ClickFix strategy—a deceptive technique that manipulates users into executing malicious code under the guise of resolving fictitious website errors.
Understanding the ClickFix Technique
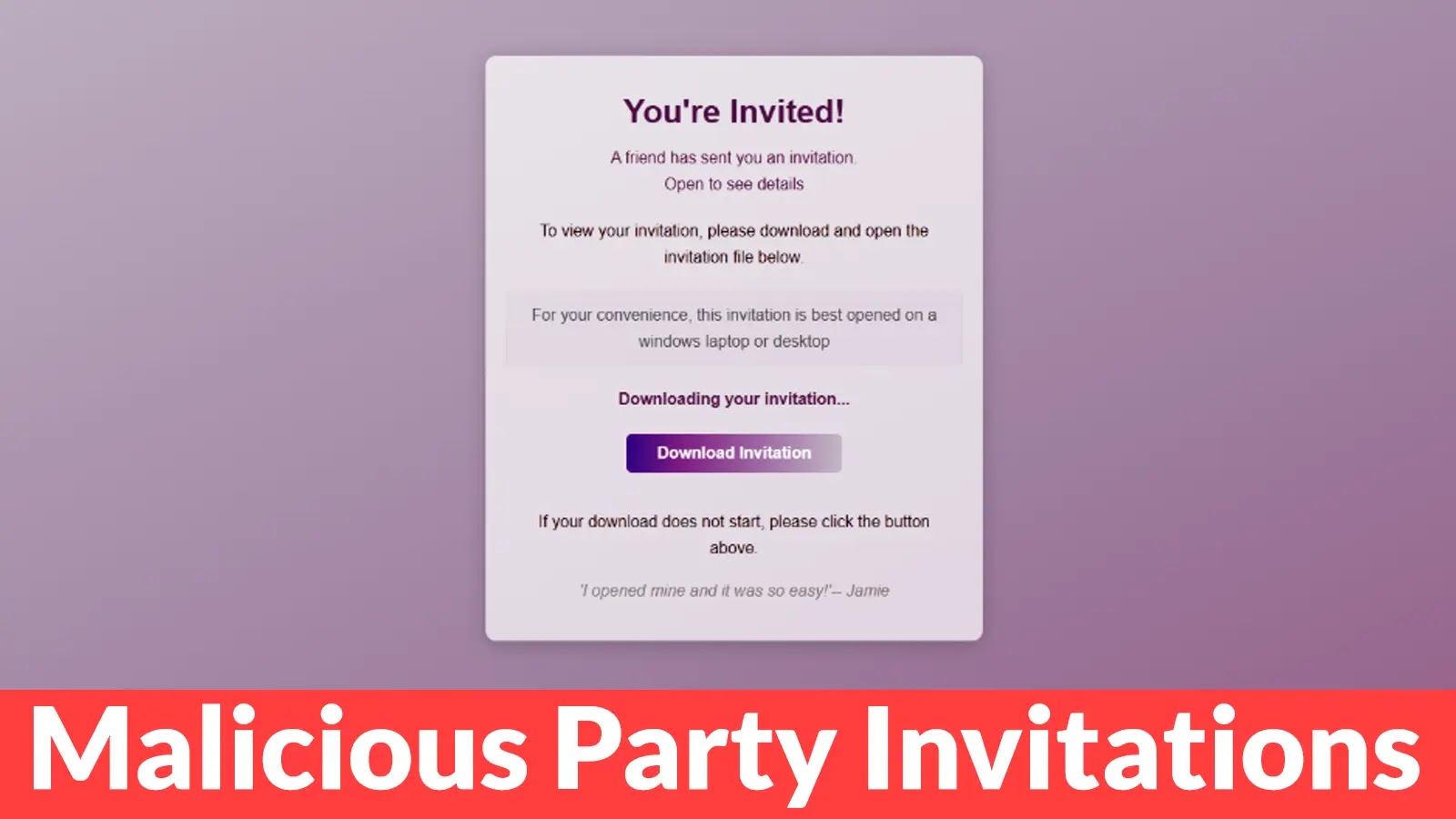
The ClickFix method is a sophisticated form of social engineering. Victims encounter simulated browser issues or counterfeit verification captchas on compromised legitimate websites. These deceptive prompts instruct users to copy a script and paste it into their system’s Run dialog or PowerShell terminal. By doing so, users inadvertently initiate the execution of malicious code, effectively bypassing automated security protocols that typically flag unauthorized downloads.
Advancement: Leveraging DNS TXT Records
Recent analyses by cybersecurity experts have unveiled a significant escalation in the KongTuke campaign’s tactics. The attackers now employ DNS TXT records to clandestinely deliver the next stage of their payload. This method involves the initial script querying a domain’s DNS records to retrieve malicious instructions embedded within the TXT records. Traditionally, DNS TXT records serve benign purposes, such as domain verification and spam prevention. However, in this context, they are repurposed to conceal malicious commands, complicating detection efforts that rely on monitoring standard HTTP traffic.
Mechanism of DNS TXT Record Exploitation
The technical innovation lies in the payload retrieval process. Upon execution of the initial ClickFix script, a PowerShell command is triggered to perform a DNS lookup for a specific TXT record associated with a seemingly legitimate domain. The TXT record contains encoded commands that, once retrieved, are executed in memory. This fileless approach minimizes on-disk artifacts, thereby evading many traditional security defenses. By embedding the payload within DNS responses, attackers effectively blend malicious traffic with regular DNS queries, exploiting the fact that DNS traffic is often less scrutinized than HTTP traffic.
Implications and Recommendations
The utilization of DNS TXT records in the ClickFix campaign underscores the increasing sophistication of cyber threats and the necessity for adaptive defense strategies. Organizations are advised to implement the following measures:
1. Monitor DNS Traffic: Regularly analyze DNS queries and responses for anomalies, such as unexpected TXT record lookups, which may indicate malicious activity.
2. Restrict PowerShell Execution: Enforce strict policies governing the use of PowerShell, including the implementation of execution policies that limit the running of scripts to those that are signed and from trusted sources.
3. User Education: Conduct ongoing training programs to educate users about social engineering tactics, emphasizing the risks associated with executing unsolicited scripts or commands.
4. Implement Network Segmentation: Design network architectures that limit the spread of malware by segmenting critical systems and applying strict access controls.
5. Deploy Advanced Threat Detection: Utilize security solutions capable of detecting fileless malware and monitoring for behavioral indicators of compromise, such as unusual PowerShell activity or unexpected DNS queries.
By adopting these proactive measures, organizations can enhance their resilience against sophisticated campaigns like KongTuke’s ClickFix attacks, thereby safeguarding their systems and data from emerging cyber threats.