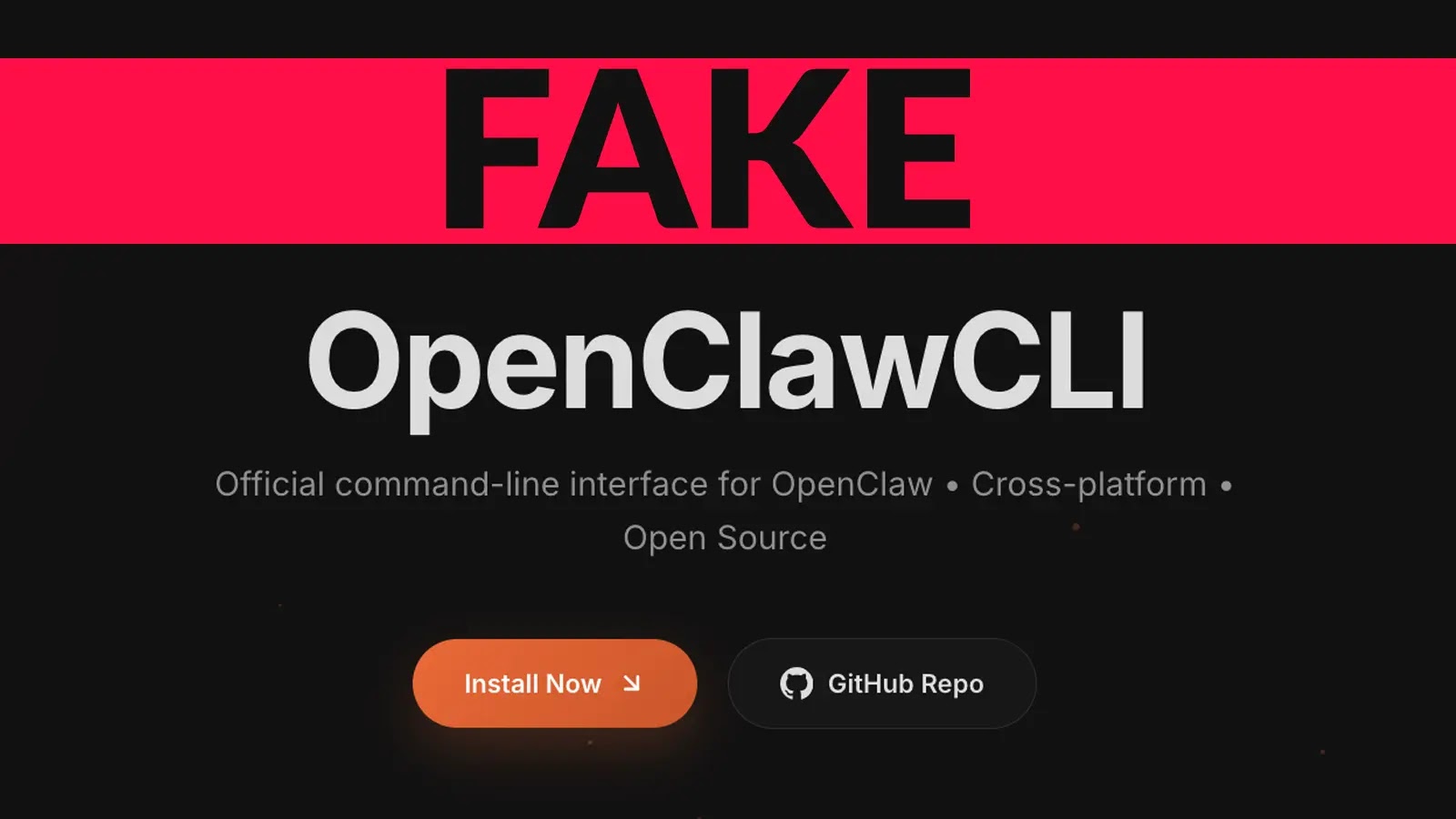
Cybercriminals Exploit ClawHub Skills to Evade VirusTotal Detection Through Social Engineering
In a concerning development within the ClawHub ecosystem, cybercriminals have refined their tactics to distribute malware, effectively bypassing traditional security measures. By leveraging social engineering techniques, these threat actors exploit the trust users place in open-source platforms, leading to potential supply chain compromises.
Evolution of Attack Strategies
Historically, malicious actors embedded harmful code directly into files, making detection by security scanners relatively straightforward. However, recent observations indicate a strategic shift: attackers now host malicious payloads on external websites, while presenting seemingly benign `SKILL.md` files within ClawHub. This method allows them to evade automated security checks that rely on known code signatures, as the `SKILL.md` files themselves contain no malicious code. Consequently, these files often pass security scans on platforms like VirusTotal, misleading users into a false sense of security.
The Deceptive Mechanism
The success of this campaign hinges on a clean lure, dirty dependency model. Attackers create `SKILL.md` files that appear legitimate, often masquerading as tools for SEO, coding, or video transcription services. These files instruct users to install a prerequisite tool named OpenClawCLI before utilizing the skill. The provided installation command, which appears standard, is actually obfuscated using Base64 encoding, concealing its true intent. When executed, this command downloads and runs a bash script from a remote server, thereby installing malware onto the victim’s system.
Implications and Recommendations
This sophisticated approach underscores the importance of vigilance when interacting with open-source platforms. Users are advised to:
– Verify Sources: Always confirm the authenticity of installation commands by cross-referencing with official project repositories.
– Be Cautious of Anomalies: Exercise caution with skills that have random character suffixes in their names or require additional installations.
– Implement Security Measures: Security teams should monitor for patterns involving the `openclawcli` domain and proactively block associated command-and-control IP addresses to prevent data exfiltration.
By adopting these practices, users and organizations can better protect themselves against evolving cyber threats that exploit trust and social engineering tactics.