Cybercriminals Exploit Genuine Enterprise Email Threads to Deploy Phishing Links
In a sophisticated supply chain phishing attack, cybercriminals infiltrated an active email conversation among C-suite executives discussing a document pending final approval. The attackers, masquerading as legitimate participants, inserted a phishing link that closely resembled a Microsoft authentication form. This breach was traced back to a compromised sales manager’s account at a contractor firm, enabling the seamless integration of the malicious link into a trusted business dialogue.
This incident highlights a growing trend where adversaries exploit authentic enterprise communications instead of crafting generic phishing lures. By early January 2026, analyses connected this event to a broader campaign active since December 2025, primarily targeting companies in the Middle East.
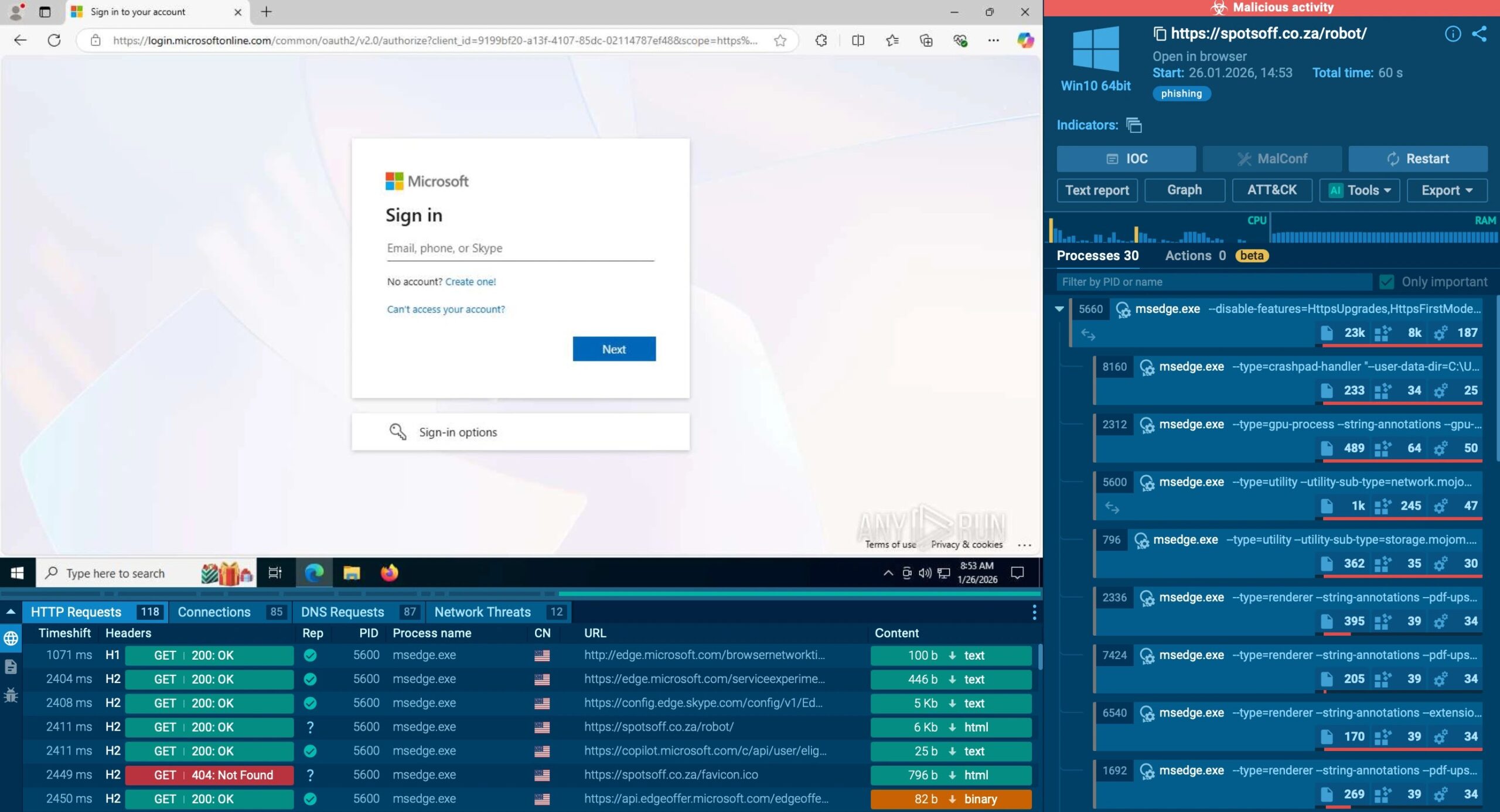
Samples tested in the ANY.RUN Sandbox revealed the use of EvilProxy, a proxy-aware phishing tool designed to evade traditional session-based detection methods. Threat intelligence lookups confirmed overlapping infrastructure, indicating a coordinated effort.
Attack Mechanics and Execution Chain
The attack employed layered social engineering tactics:
1. Initial Compromise: The attackers initiated the scheme with a supply chain attack (SCA) phishing email sent to the contractor.
2. Propagation: This email triggered a series of seven forwarded messages, enhancing the credibility of the communication as it circulated through internal channels.
3. Phishing Link Deployment: The final reply in the thread contained a phishing link leading to:
– An antibot landing page protected by Cloudflare Turnstile CAPTCHA.
– A phishing page with an additional Turnstile layer for human verification.
– Deployment of EvilProxy, capturing credentials via man-in-the-middle proxying.
This sequence mimicked legitimate Microsoft 365 processes, utilizing dynamic HTML/PDF attachments with embedded scripts. Notably, the attackers did not rely on zero-day vulnerabilities or exploits; their success hinged on exploiting business trust and hijacking ongoing conversations. The infrastructure used rivaled phishing-as-a-service (PhaaS) platforms in scale, employing rented domains and bot mitigation techniques to evade detection by analysts.
Detonations in the ANY.RUN Sandbox visualized the entire attack chain, revealing network callbacks to command-and-control servers, credential exfiltration, and session token theft—all occurring in under 60 seconds.
Indicators pointed to numerous victims, with a focus on the Middle East, likely tied to the region’s finance and energy sectors. The resurgence of EvilProxy, following its debut in 2023, underscores the evolution of PhaaS platforms: modular kits now integrate Turnstile and geo-fencing, complicating efforts to dismantle them.
Unlike attacks exploiting technical vulnerabilities, this approach weaponizes human workflows. Compromised contractor accounts produce emails that appear perfectly legitimate, bypassing DMARC and other filters. As remote work becomes more prevalent, enterprises face increased risks due to asynchronous approval processes.
Mitigation Strategies and Indicators of Compromise (IOCs)
To defend against such attacks, organizations should implement the following strategies:
– Process Hardening: Flag HTML/PDF files with dynamic content and sandbox suspicious files before interaction.
– Approval Protocols: Enforce the four-eyes principle, ensuring that initiation and approval processes are handled separately.
– Training Simulations: Conduct realistic SCA simulations that mimic hijacked email threads to train employees effectively.
ANY.RUN provides security operations centers (SOCs) with behavioral reports, significantly reducing mean time to detect (MTTD) and mean time to respond (MTTR).
Key IOCs:
– URI Pattern: POST ^(/bot/
– Domains:
– himsanam[.]com
– bctcontractors[.]com
– studiofitout[.]ro
– st-fest[.]org
– komarautikat[.]hu
– eks-esch[.]de
– avtoritet-car[.]com
– karaiskou[.]edu[.]gr
– Domain Pattern: ^loginmicrosoft
By understanding and mitigating these sophisticated phishing tactics, organizations can better protect themselves against evolving cyber threats.