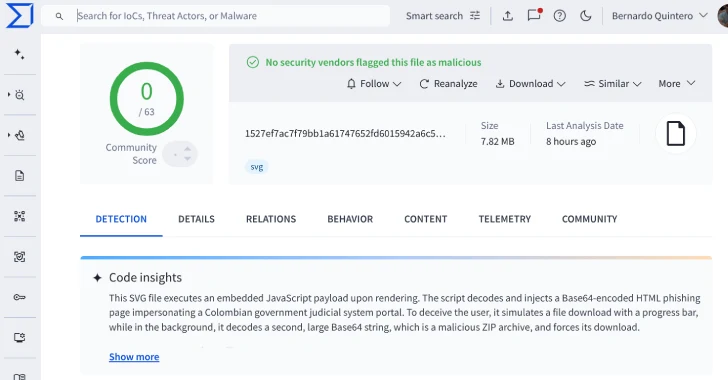
Cybersecurity experts have recently identified a sophisticated phishing campaign that leverages Scalable Vector Graphics (SVG) files to deceive users and deploy malicious payloads. This method involves embedding JavaScript within SVG files, which, when executed, injects a Base64-encoded HTML phishing page designed to mimic the official portal of the Fiscalía General de la Nación, Colombia’s Office of the Attorney General.
Mechanism of the Attack
The attack initiates with the distribution of SVG files via email. These files contain embedded JavaScript code that, upon execution, decodes and injects a Base64-encoded HTML page. This page is crafted to resemble the official website of the Colombian Attorney General’s Office, aiming to gain the trust of unsuspecting users.
Once the phishing page is displayed, it simulates an official document download process, complete with a fake progress bar. Simultaneously, it clandestinely triggers the download of a ZIP archive in the background. The exact contents of this ZIP file remain undisclosed, but it is presumed to contain further malicious payloads intended to compromise the victim’s system.
Evasion Techniques
The attackers employ advanced evasion techniques to ensure the SVG files remain undetected by traditional antivirus engines. These techniques include:
– Obfuscation: The malicious code is deliberately obscured to make it difficult for security tools to analyze and detect.
– Polymorphism: The code changes its appearance with each iteration, making signature-based detection methods ineffective.
– Insertion of Junk Code: The inclusion of non-functional code increases the file size and complexity, further hindering analysis.
VirusTotal, a Google-owned malware scanning service, reported the discovery of 44 unique SVG files associated with this campaign, all of which evaded detection due to these sophisticated techniques. In total, 523 such SVG files have been identified, with the earliest sample dating back to August 14, 2025.
Evolution of the Payloads
An analysis of the malicious SVG files revealed an evolution in their payloads. Early samples were approximately 25 MB in size, but over time, the file sizes decreased. This trend suggests that the attackers are refining their methods, possibly to enhance the efficiency and effectiveness of their attacks.
Broader Implications
This discovery underscores a broader trend in cyber threats, where attackers are increasingly targeting macOS systems. For instance, malicious actors are distributing cracked versions of legitimate software to deploy the Atomic macOS Stealer (AMOS). This malware is capable of stealing a wide range of sensitive information, including credentials, browser data, cryptocurrency wallets, Telegram chats, VPN profiles, keychain items, Apple Notes, and files from common folders.
The attack chain typically involves users seeking cracked software on websites like haxmac[.]cc. These sites redirect users to fraudulent download links that provide installation instructions designed to trick them into executing malicious commands in the Terminal app, leading to the deployment of AMOS.
Mitigation Measures
Apple’s Gatekeeper protections in macOS Sequoia have been enhanced to block the installation of malicious or unsigned .dmg files by default. While this measure raises the barrier for successful infections, it does not eliminate the risk entirely, especially for users who may bypass built-in protections. Consequently, attackers are adapting their delivery methods, such as using terminal-based installation techniques that can bypass these security controls.
Conclusion
The use of SVG files in phishing attacks highlights the evolving tactics of cybercriminals and the need for continuous vigilance. Users are advised to exercise caution when opening email attachments, especially those from unknown sources, and to keep their systems updated with the latest security patches. Employing comprehensive security solutions that can detect and mitigate such sophisticated attacks is crucial in safeguarding sensitive information.